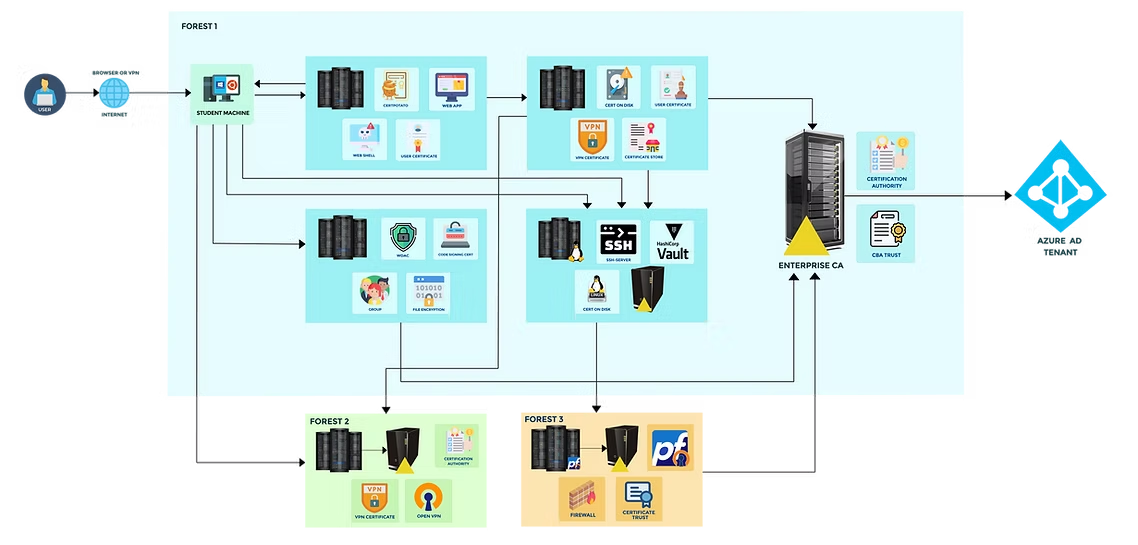
AD CS Attacks for Red and Blue Teams Lab Objective:
Identity plays a crucial role in security of an enterprise environment. Certainly, Identity is the new security perimeter. In an enterprise environment, Identity is usually managed by Active Directory or by Azure AD in case of a Hybrid Identity. An often-overlooked part of enterprise infrastructure is Active Directory Certificate Services (AD CS). AD CS is a Windows Server Role that implements Public Key Infrastructure and can be used for user authentication, machine authentication, document signing, email signing, file encryption and so much more. This makes AD CS a crucial part of Identity Management.

Unfortunately, not many professionals understand AD CS. This, of course, makes it harder to secure it against even the simplest attacks that may result in compromise of the entire enterprise environment.
We have years of experience of teaching classes at world’s leading organizations and hacker conferences and Red Team operations against some of the better enterprise environments. Drawing from that experience, we have created this course and lab that helps you in getting started with Attacking and Defending AD CS.
The AD CS Attacks for Red and Blue Teams lab provides course videos, learning aids and a meticulously created lab environment that helps you in understanding AD CS security in-depth. The lab is beginner friendly and you don’t need any prior experience with AD CS. We cover a lot of interesting topics like CA enumeration, Local Privilege Escalation, Persistence by abusing Certificates, Domain Privilege Escalation by - abusing CA, Certificate Templates, Abusing Certificates – Client Auth, EFS, Code Signing, SSH etc., Domain persistence after compromising CA, Network Pivoting by abusing VPN Certificates, Abusing certificates on Linux machines, Lateral movement to Azure and a lot more!
What's Included

- Access to a lab environment (One/Two/Three months) with updated Server 2022 and Linux machines. Lab can be accessed using a web browser or VPN.
- A ready to use student VM in the cloud that has both Windows and Linux tools pre-installed.
- Life time access to all the learning material (including course updates).
- 11+ hours of video course
- Slides, Lab Manual, Walk-through videos and Diagrams as learning aid.
- Lab manual for solving the labs.
- One exam attempt for the Certified Enterprise Security Professional – AD CS (CESP - ADCS) certification.
- Support on email and Discord.
What will you Learn?

- Performing Red Team operation or Penetration Test against a modern AD CS environment.
- AD CS is not the only CA in the lab. Learn and practice attacks against other Certificate Services too!
- Pivot to Azure by abusing Azure Certificate-based authentication.
- Abuse VPN certificates to pivot to protected networks .
- Abuse Trusted CAs across the AD forests.
- Learn to execute attacks from both Windows and Linux.
Prerequisites for the course
- If you are new to Red Teaming, Enterprise security and Active Directory security, you may like to go for the
This link is hidden for visitors. Please Log in or register now.
- Ability to use command line tools.
What will you Learn?
20 Learning Objectives, 25 Modules, 40 Flags, >130 Hours of FunI. AD CS Enumeration
- Use built-in tools and external tools to enumerate the AD CS CA and its various template configurations.
- Enumerate, understand, and find common and complex AD CS misconfigurations for abuse.
- Explore interconnected attack chains as seen in enterprise environments.
- Analyse certificates to parse and extract useful information from them.
- Enumerate alternate Certification Authorities.
II. AD CS Local Privilege Escalation
- Escalate privileges from Virtual Account to SYSTEM by abusing AD CS misconfigurations.
- Hunt for local admin privileges on machines in the target domain using multiple methods.
- Replay certificates to find elevated privileges on compromised machines.
- Abuse Linux groups dynamically mapped to AD groups to escalate privileges on Linux.
III. AD CS Domain Privilege Escalation
- Abuse SubjectAltName to escalate privileges to Domain / Enterprise Admins by abusing AD CS misconfigured templates.
- Abuse misconfigured ACLs over AD CS templates and the CA server itself to escalate to Domain / Enterprise Admins.
- Compromise forest by abusing overly permissive role assignments on the CA server.
- Abuse certificate EKUs to execute interesting and fun attacks to escalate privileges.
- Leverage CA Access Control roles to perform administrative actions and escalate domain privileges.
- Setup and perform relaying attacks to CA endpoints to relay and impersonate a high privileged computer account.
IV. AD CS Pivoting and Lateral Movement
- Pivot into air-gapped protected networks by abusing VPN certificates stolen from an alternate CA.
- Reconstruct OpenVPN configuration files using stolen certificates to pivot to restricted networks.
- Use Kerberos PKINIT and Schannel authentication to execute lateral movement.
- Execute Pass-the-Cert for lateral movement to multiple machines.
- Execute Shadow Credential attack to access remote machines with administrative privileges.
- Perform S4U2Self to access other machines in the network.
V. AD CS Theft and Collection
- Export certificates from the User / Machine Certificate Stores using CRYPTO WINAPIs.
- Search for interesting certificates, keys, config files, tokens etc on-disk.
- Exfiltrating certificates from the Certificate Store using DPAPI.
- Certificate exfiltration on Linux from flat SQLite NSS databases.
- Execute UnPAC-the-hash / Shadow Credentials attack to extract NTLM hashes of target accounts.
- Extracting secrets like certificates and private keys from Vault.
VI. AD CS Local and Domain Persistence
- User and Computer Account Persistence using new Certificate Requests.
- User and Computer Account Persistence using Certificate Renewal before expiration.
- Forge ANY domain certificate using stolen CA certificate and private keys.
- Backdoor a CA server using malicious AD CS misconfigurations.
- Use root token to persist with highest privileges on Vault.
VII. Abusing Cross Forest and External Trusted CAs
- Escalate privileges to trusting forest using a stolen CA certificate and private key trusted for Cross Forest CA deployment.
- Compromise Linux AD-joined machines by abusing SSH Signer services by an alternate CA.
VIII. Abusing Azure CBA for Lateral Movement and Persistence on Cloud
- Forge certificates for ANY Azure AD user to access the Azure AD tenant (CBA) that trusts the compromised CA.
- Replay forged or compromised certificates of Azure AD users for persistence.
IX. Evasion and Bypasses
- Use Microsoft Signed binaries to sign attack tools.
- Evade WDAC by abusing a certificate with CodeSigning EKU to execute attack tools on a target machine.
- Use Microsoft Signed binaries to analyse encrypted files on a target machine.
- Retrieve encrypted files protected by EFS (Encrypted File System) using a stolen certificate.
- Bypass a JEA endpoint by abusing binaries that are allowed in the NoLanguageMode.
- Bypass Kerberos Double Hop Issues using reverse shells and leveraging legitimate channels such as CredSPP.
- Bypass Microsoft's CBA patch in FullEnforcement mode.
- Obfuscate tools to bypass Windows Defender on the target fully patched Server 2022 machines.
- Use in-memory execution of payloads to bypass Enhanced Logging and AV.
X. AD CS Defence - Prevention and Detection
- Configure auditing using Group Policy and CA server settings.
- Understand commonly generated Event IDs by AD CS.
- Analyse logs generated by the attack techniques used in the lab.
- Understand how to differentiate anomalous Event IDs from the normal ones.
- Harden AD CS server and certificate templates to prevent common attacks.
- Understand the benefits of CBA patch.
- Use custom policy to stop bypass of the CBA patch.
Download
Free download for users PRIV8Password
htdark.com