- Joined
- Jan 8, 2019
- Messages
- 56,607
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,453
- Points
- 2,313
- Credits
- 32,590
6 Years of Service
76%
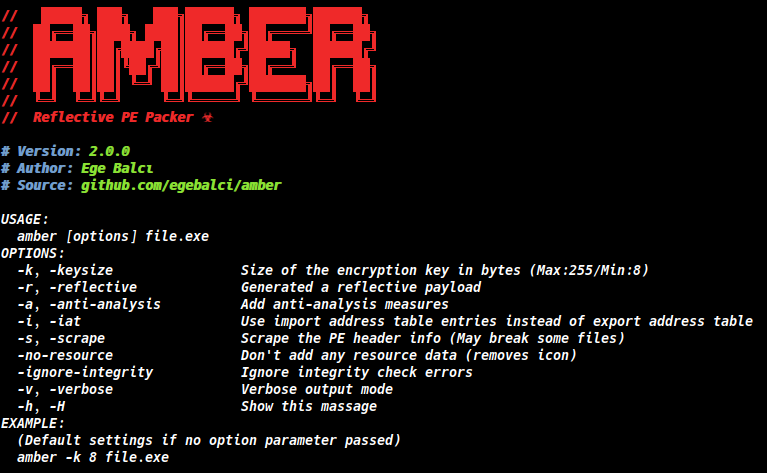
amber is a reflective PE packer for bypassing security products and mitigations. It can pack regularly compiled PE files into reflective payloads that can load and execute itself like a shellcode. It enables stealthy in-memory payload deployment that can be used to bypass anti-virus, firewall, IDS, IPS products and application white-listing mitigations. If you want to learn more about the packing methodology used inside amber check out below.
New Features
x64 support added !
Support for MacOS and Windows (Currently supporting all major platforms)
Assembly stubs rewritten
External dependencies reduced to two
C++ stubs converted to go
All project converted into a go package
To see this hidden content, you must like this content.