- Joined
- Jan 8, 2019
- Messages
- 56,605
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,451
- Points
- 2,313
- Credits
- 32,570
6 Years of Service
76%
This link is hidden for visitors. Please Log in or register now.
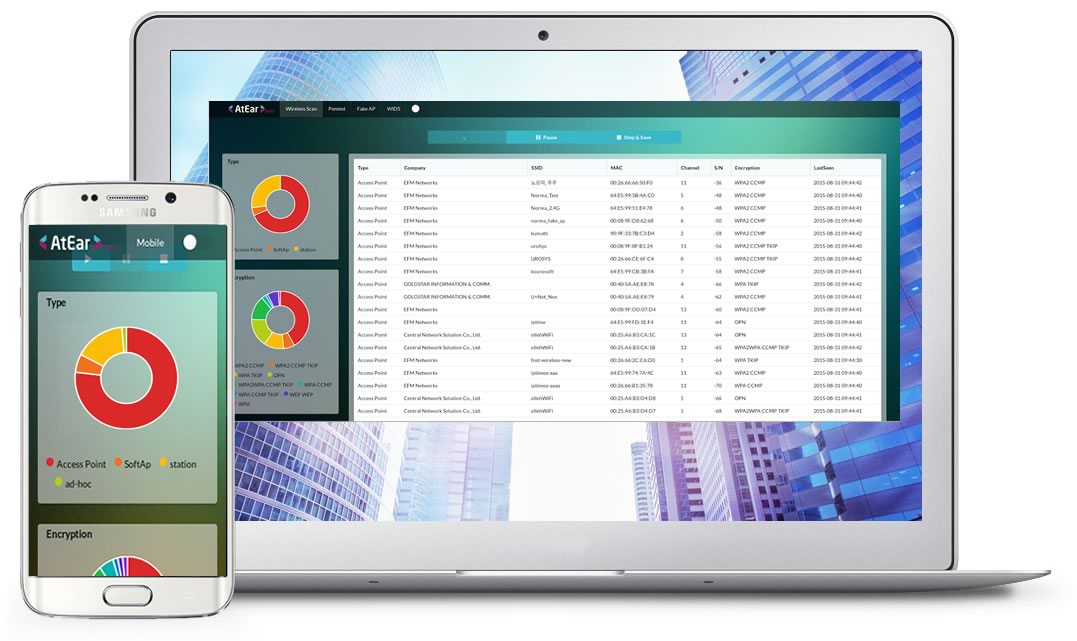
## AtEar AtEar is a scalable and efficient system, and also the first web-based wireless vulnerability assessment solution.
This Wireless Vulnerability Analysis/Management Solution, AtEar, can be utilized both by businesses and in the home.
For business use, AtEar utilizes fingerprint devices for access to the network and to analyze the current wireless network conditions.
The automatic penetration testing function makes it possible to analyze wireless vulnerability conveniently and meticulously.
AtEar for home networks inspects network security conditions and monitors for any unregistered devices.
This Wireless Vulnerability Analysis/Management Solution, AtEar, can be utilized both by businesses and in the home.
For business use, AtEar utilizes fingerprint devices for access to the network and to analyze the current wireless network conditions.
The automatic penetration testing function makes it possible to analyze wireless vulnerability conveniently and meticulously.
AtEar for home networks inspects network security conditions and monitors for any unregistered devices.
Intro
In short,
is a wireless pentest system.
AtEar provides a web-based user interface.
AtEar is easy and fast to use.
This link is hidden for visitors. Please Log in or register now.
AtEar provides a web-based user interface.
AtEar is easy and fast to use.
Is your company’s wireless network secure?
AtEar helps keep your wireless network safe from hackers and intruders.
This link is hidden for visitors. Please Log in or register now.
Operation Video
This link is hidden for visitors. Please Log in or register now.
AtEar Features
Wireless Scanning(Ad-Hoc, Station, Access Point, Soft-Acess Point)
Wireless Chart(Channel, Encryption, Type)
Wireless Pentesting(WEP, WPA1, WPA2)
Network Information Getting(IP, Connected Host Info)
Fake AP
Google Phishing Sites
Facebook Phishing Sites
Twitter Phishing Sites
WIDS(Wireless intrusion detection system)
Disassocation Flood
Deauth Flood
WESSID-NG Attack
Koreck Chopchop attack
Fragmentation PGRA Attack
MDK MICHEAL SHUTDOWN Exploitation TKIP Attack
Attack By TKIPUN-NG
Authentication DOS Attack
Assocation Flood
High Amount of Assocation Sent
Suspect Rouge AP
Detected Beacon Flood
These features will be released this month.
Network Pentesting
FTP Brute Force
SSH Brute Force
Telnet Brute Force
SMTP Brute Force
POP Brute Force
IMAP Brute Force
LDAP Brute Force
SMB Brute Force
rlogin Brute Force
MSSQL Brute Force
MYSQL Brute Force
PGSQL Brute Force
VNC Brute Force
SNMP Brute Force
To see this hidden content, you must like this content.