- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,456
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
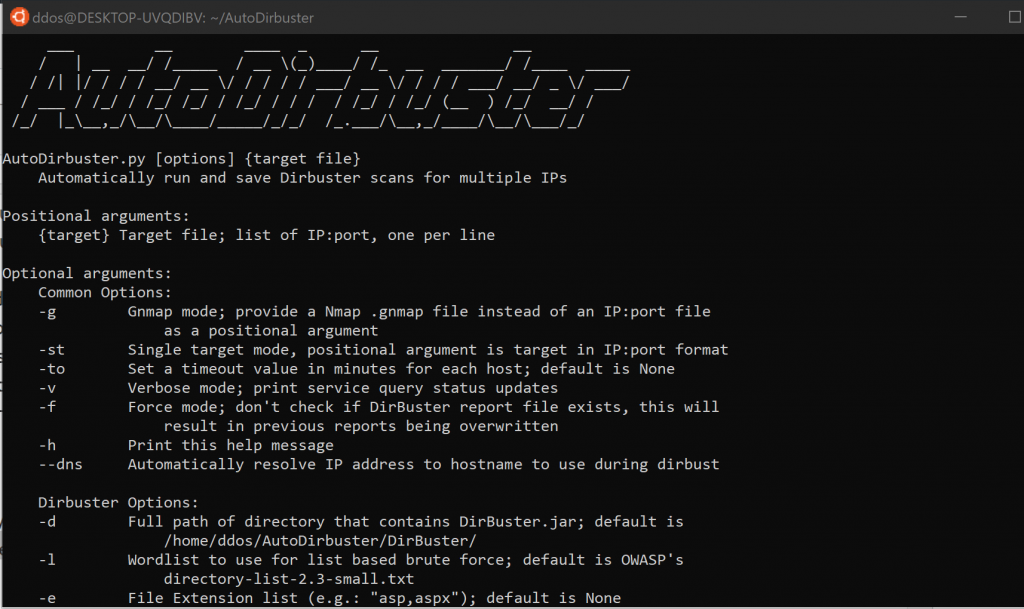
AutoDirbuster
Automatically run and save Dirbuster scans for multiple IPs
Why?
OWASP Dirbuster is a great directory buster but running it against multiple IPs and ports is a very manual process with a lot of downtime between scans. This script attempts to automate that process and eliminates downtime between scans.
What is the recommended usage?
If attacking multiple targets:
Run Nmap and find open ports, outputting the results with -oG or -oA
Run AutoDirbuster with the Nmap results and a timeout (closed ports or non-HTTP based services are ignored)
python AutoDirbuster.py -g Nmap_results.gnmap -to 15
As the pentest progresses, periodically review the Dirbust results using dirbust_read.py, which will ignore all Dirbuster error lines and only print the found directories and files
If attacking a single target:
python AutoDirbuster.py -st example.com:80
What data does this need?
The script can take three data sources:
List of IP
python AutoDirbuster.py ip_port_list.txt
An Nmap Gnmap result file
python AutoDirbuster.py -g Nmap_results.gnmap
A single target
python AutoDirbuster.py -st example.com:80
How does this script work?
A list of targets is provided
A TCP connect scan is done on the target port to test if it’s open
If it’s open, HTTP and HTTPS requests are sent to determine if the service is HTTP-based and whether it requires SSL
If the service is HTTP, a check is done to determine if a previous report file is in the same directory. Report files follow the format: DirBuster-Report-IP-port.txt
Dirbuster is run using Python’s subprocess.Popen(). If a timeout is specified, then after the timeout period, a SIGINT signal is sent to Dirbuster so it can safely shut down and write results to disk. A note is added to the report indicating that the scan timed out.
The next IP
This script isn’t working
Ensure the following
Are all of the dependencies listed in requirements.txt installed?
Is there a directory called “DirBuster” inside the same directory as AutoDirbuster.py?
Does this “DirBuster” directory contain the Dirbuster JAR file named “DirBuster.jar”?
Is “DirBuster.jar” version 0.12?
Does this “DirBuster” directory contain a file called “directory-list-2.3-small.txt” (the default wordlist)?
Does this “DirBuster” directory contain a subdirectory called “lib” with the default 13 required Dirbuster JAR dependencies?
Is Java installed?
Is Java in your path?
Run AutoDirbuster with the –debug flag to view the subprocess command that AutoDirbuster is using to launch Dirbuster. Run this command from the terminal to view standard error as AutoDirbuster is configured to send subprocess standard error to /dev/null
To see this hidden content, you must like this content.