13 Years of Service
100%
Please note, if you want to make a deal with this user, that it is blocked.
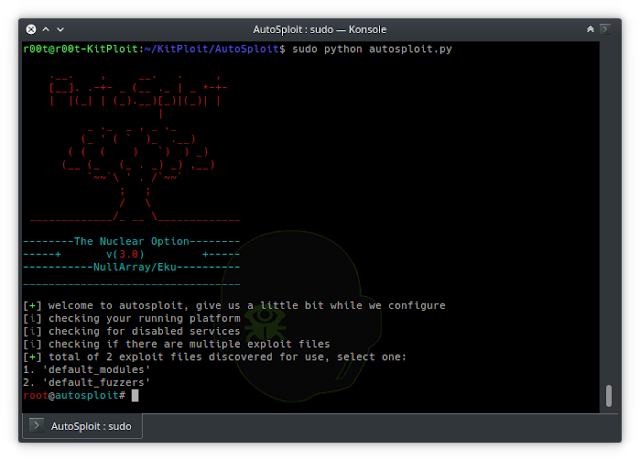
As the name might suggest AutoSploit attempts to automate the exploitation of remote hosts. Targets can be collected automatically through Shodan, Censys or Zoomeye. But options to add your custom targets and host lists have been included as well. The available Metasploit modules have been selected to facilitate Remote Code Execution and to attempt to gain Reverse TCP Shells and/or Meterpreter sessions. Workspace, local host and local port for MSF facilitated back connections are configured by filling out the dialog that comes up before the exploit component is started
Operational Security Consideration
Receiving back connections on your local machine might not be the best idea from an OPSEC standpoint. Instead consider running this tool from a VPS that has all the dependencies required, available.
The new version of AutoSploit has a feature that allows you to set a proxy before you connect and a custom user-agent.
This release adds a number of features and bug fixes.
Features
- New Terminal. Now also supports;
Custom Commands
- Command History
- Native binary execution (/bin & /sbin)
[*]Host file backup support
[*]Options to renew or reset API tokens
SRC
To see this hidden content, you must like this content.