- Joined
- Jan 8, 2019
- Messages
- 56,609
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,454
- Points
- 2,313
- Credits
- 32,610
6 Years of Service
76%
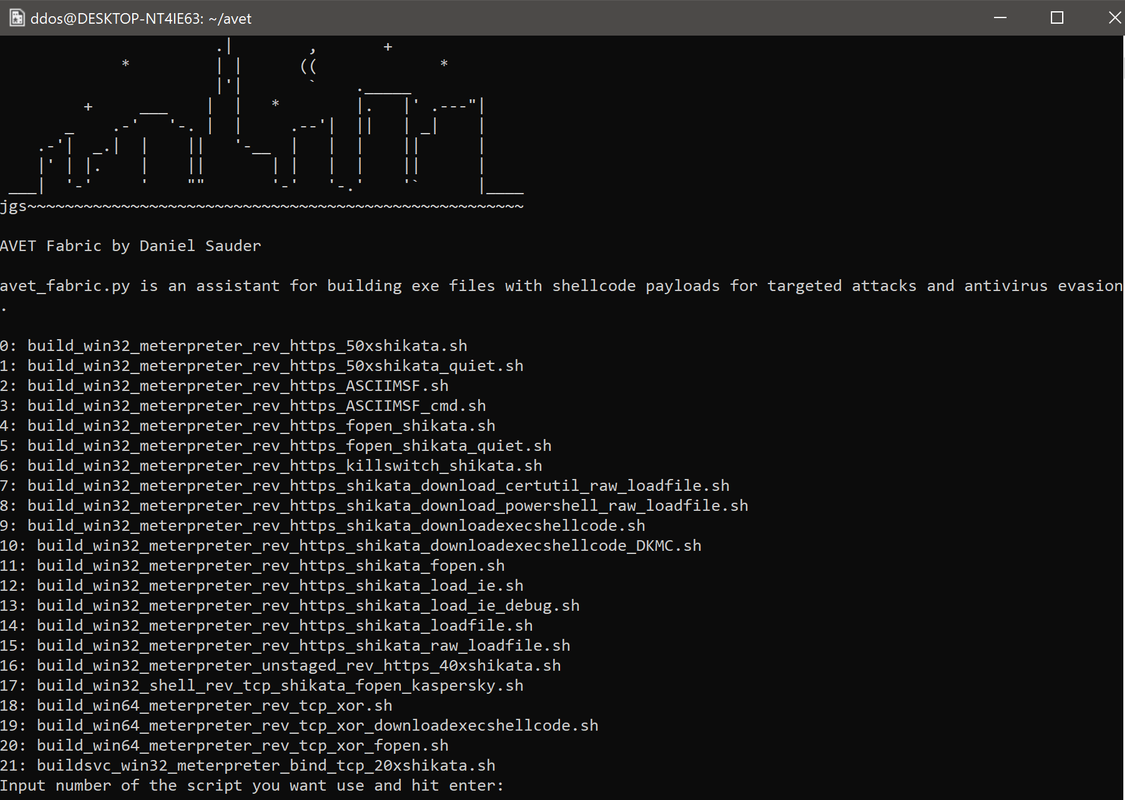
AVET is an AntiVirus Evasion Tool, which was developed for making life easier for pentesters and for experimenting with antivirus evasion techniques.
What & Why:
when running an exe file made with msfpayload & co, the exe file will often be recognized by the antivirus software
avet is an antivirus evasion tool targeting windows machines with executable files
assembly shellcodes can be used
make_avet can be used for configuring the source code
with make_avet you can load ASCII encoded shellcodes from a text file or from a web server, further it is using an av evasion technique to avoid sandboxing and emulation
for ASCII encoding the shellcode the tool format.sh and sh_format are included
this readme applies to Kali 2 (64bit) and tdm-gcc
Changelog v2.2
+++ CHANGES +++
– Generated executables are now named after their buildscripts instead of “output.exe”.
– added “build_script_tester.py”, a script which executes all build scripts and fetch error messages.
– Usage of executables is now echoed to screen
– replace “avet_fabric.py” with “avet.py”. “avet.py” helps new users to configure and build scripts without changing the orignal build script.
– new build scripts structure with tags(tags are only relevant for avet.py)
– adjust setup to work with Kali 2020.1
– updated tdm-gcc to version 9.2.0
To see this hidden content, you must like this content.