- Joined
- Jan 8, 2019
- Messages
- 56,608
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,454
- Points
- 2,313
- Credits
- 32,600
6 Years of Service
76%
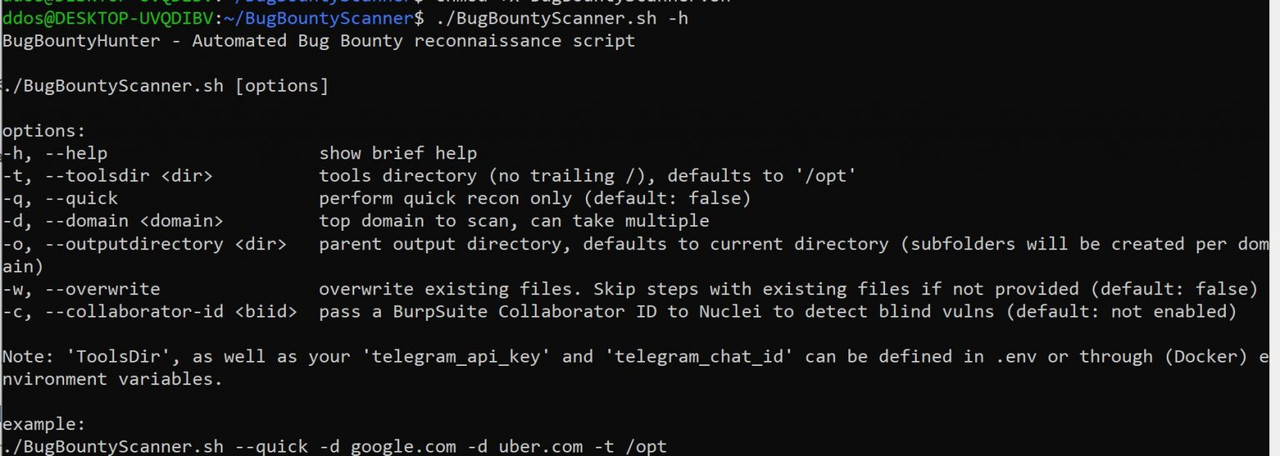
BugBountyScanner
A Bash script and Docker image for Bug Bounty reconnaissance, intended for headless use. Low on resources, high on information output.
It’s recommended to run BugBountyScanner from a server (VPS or home server), and not from your terminal. It is programmed to be low on resources, with potentially multiple days of scanning in mind for bigger scopes. The script functions on a stand-alone basis.
You can run the script either as a docker image or from your preferred Debian/Ubuntu system (see below). All that is required is kicking off the script and forgetting all about it! Running the script takes anywhere in between several minutes (for very small scopes < 10 subdomains) and several days (for very large scopes > 20000 subdomains). A ‘quick mode’ flag is present, which drops some time-consuming tasks such as vulnerability identification, port scanning, and web endpoint crawling.
Features
Resource-efficient, suitable for running in the background for a prolonged period of time on a low-resource VPS, home server, or Raspberry Pi
Telegram status notifications with per-command results
Extensive CVE and misconfiguration detection with Nuclei (optionally with detection of blind vulnerabilities via Burp Collaborator)
Subdomain enumeration and live web server detection
Web screenshotting and crawling, HTML screenshot report generation
Retrieving (hopefully sensitive) endpoints from the Wayback Machine
Identification of interesting parameterized URLs with Gf
Enumeration of common “temporary” and forgotten files with GoBuster
Automatic detection of LFI, SSTI, and Open Redirects in URL parameters
Subdomain takeover detection
Port scanning (Top 1000 TCP + SNMP)
‘Quick Mode’ for opsec-safe (ish) infrastructure reconnaissance
Tools
amass
dnsutils
Go
gau
Gf (with Gf-Patterns)
GoBuster
gospider
httpx
nmap
Nuclei (with Nuclei-Templates)
qsreplace
subjack
webscreenshot
To see this hidden content, you must like this content.