- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,456
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
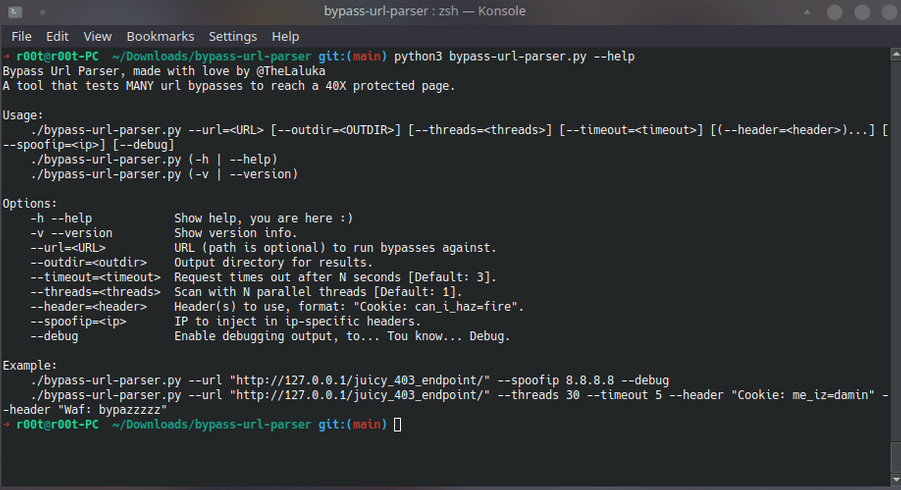
Tool that tests MANY url bypasses to reach a 40X protected page.
If you wonder why this code is nothing but a dirty curl wrapper, here's why:
Most of the python requests do url/path/parameter encoding/decoding, and I hate this.
If I submit raw chars, I want raw chars to be sent.
If I send a weird path, I want it weird, not normalized.
This is surprisingly hard to achieve in python without losing all of the lib goodies like parsing, ssl/tls encapsulation and so on.
So, be like me, use curl as a backend, it's gonna be just fine.
To see this hidden content, you must like this content.