dEEpEst
☣☣ In The Depths ☣☣
Staff member
Administrator
Super Moderator
Hacker
Specter
Crawler
Shadow
- Joined
- Mar 29, 2018
- Messages
- 13,860
- Solutions
- 4
- Reputation
- 27
- Reaction score
- 45,546
- Points
- 1,813
- Credits
- 55,340
7 Years of Service
56%
About
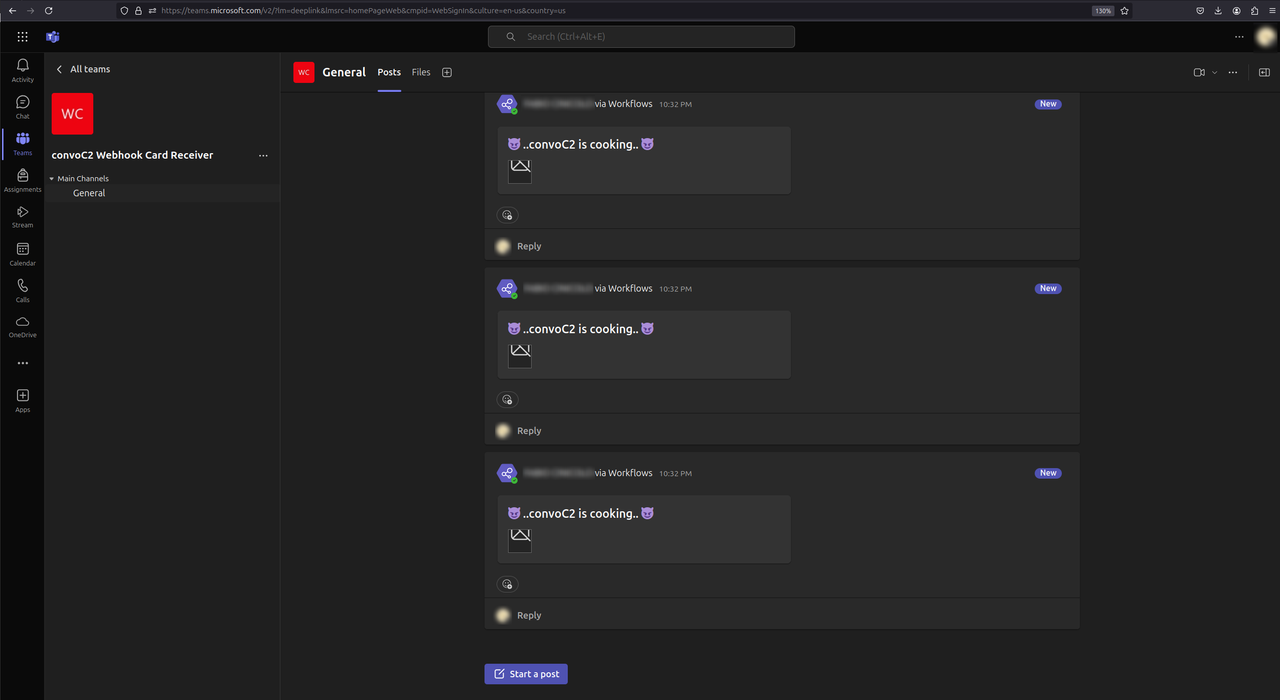
C2 infrastructure that allows Red Teamers to execute system commands on compromised hosts through Microsoft TeamsIntroduction
Command and Control infrastructure that allows Red Teamers to execute system commands on compromised hosts through Microsoft Teams.It infiltrates data into hidden span tags in Microsoft Teams messages and exfiltrates command outputs in Adaptive Cards image URLs, triggering out-of-bound requests to a C2 server.
The lack of direct communication between the victim and the attacker, combined with the fact that the victim only sends http requests to Microsoft servers and antiviruses don't look into MS Teams log files, makes detection more difficult.