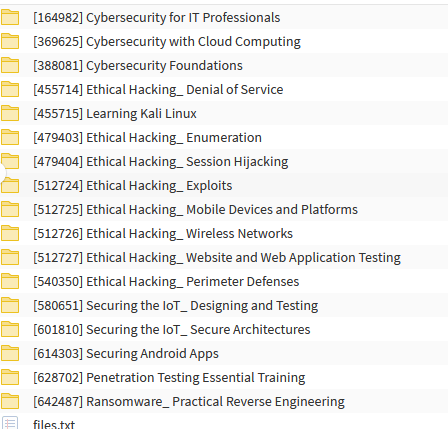
Including:

Cybersecurity for IT Professionals

Cybersecurity with Cloud Computing

Cybersecurity Foundations

Ethical Hacking Denial of Service

Ethical Hacking Enumeration

Ethical Hacking Session Hijacking

Ethical Hacking Wireless Networks

Ethical Hacking Mobile Devices and Platforms

Ethical Hacking Website and Web Application Testing

Ethical Hacking Exploits

Ethical Hacking Perimeter Defenses

Learning Kali Linux

Securing the IoT Designing and Testing

Securing Android Apps

Securing the IoT Secure Architectures

Penetration Testing Essential Training

Ransomware Practical Reverse Engineering
To see this hidden content, you must like this content.