- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,457
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
FuzzingTool
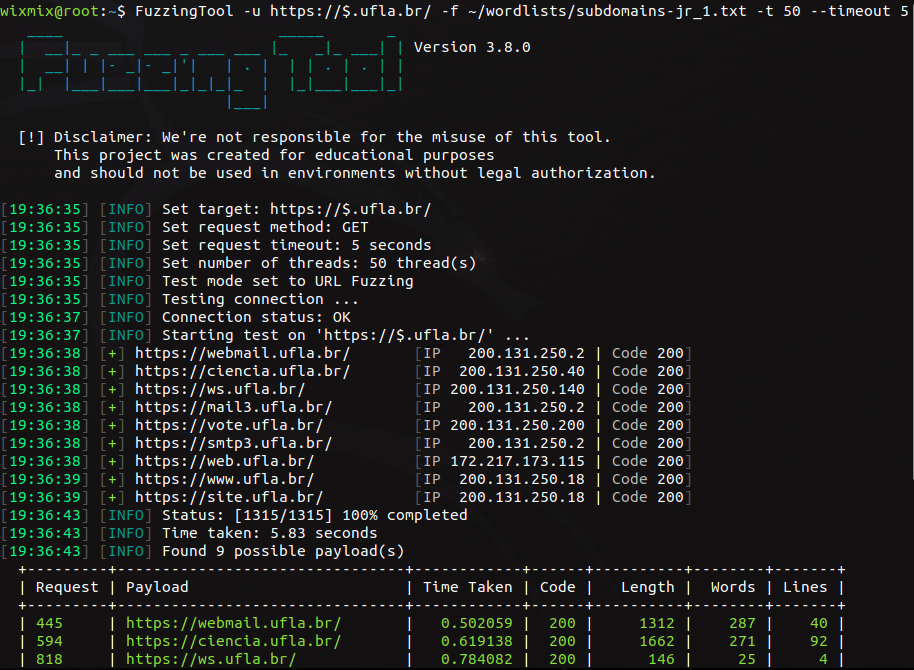
FuzzingTool is a web penetration testing tool, that handles with fuzzing. After the test is completed, all possible vulnerable entries (and the response data) are saved on a report file.
Changelog v3.9
New features
Option to insert multiple targets:
by urls (for each -u);
by raw HTTP (for each -r);
Option to insert custom, and multiple, http verbs (request methods);
Fuzzing http verbs;
Added scanners (see Default scanners and Custom scanners);
Added dictionaries (see Default dictionaries and Custom dictionaries);
Added encoders (see Encoders);
Use requests Session object to perform a session request for URL fuzzings. Keep the common request method for non URL fuzzings;
Blacklist a response status code to pause the application, or skip the current fuzzed target;
Added wordlists to the project;
Code refatored
ApplicationManager: Added callback functions to be called on Fuzzer, removed the proxies checker and ajusted the footer content;
OutputHandler: Moved the help menu to ApplicationManager;
FileHandler: Separated the reports and logs functions into classes – Logger and Reporter;
RequestParser: Bring the commom url parsing functions to out of the class;
Moved the exceptions to exceptions directory;
Moved the useful functions to utils directory;
To see this hidden content, you must like this content.