- Joined
- Jan 8, 2019
- Messages
- 56,602
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,445
- Points
- 2,313
- Credits
- 32,540
6 Years of Service
76%
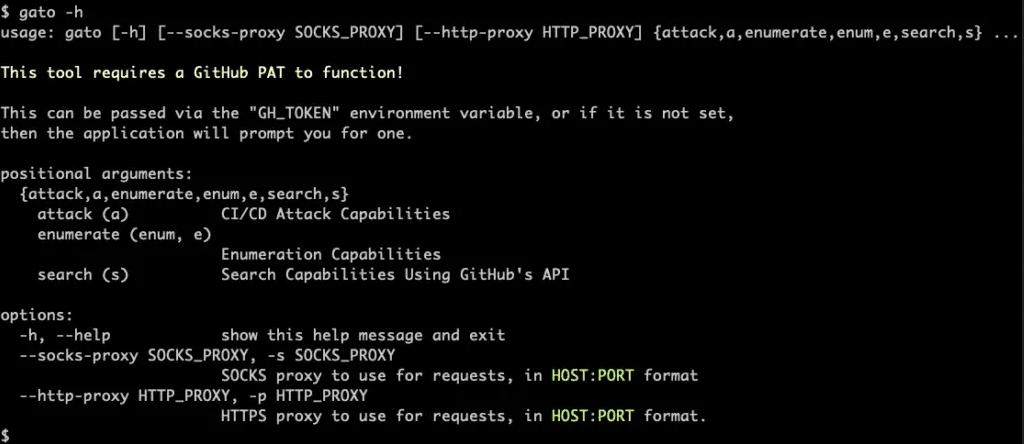
Gato, or GitHub Attack Toolkit, is an enumeration and attack tool that allows both blue teamers and offensive security practitioners to evaluate the blast radius of a compromised personal access token within a GitHub organization.
The tool also allows searching for and thoroughly enumerating public repositories that utilize self-hosted runners. GitHub recommends that self-hosted runners only be utilized for private repositories, however, there are thousands of organizations that utilize self-hosted runners.
Who is it for?
Security engineers who want to understand the level of access a compromised classic PAT could provide an attacker
Blue teams that want to build detections for self-hosted runner attacks
Red Teamers
Bug bounty hunters who want to try and prove RCE on organizations that are utilizing self-hosted runners
Features
GitHub Classic PAT Privilege Enumeration
GitHub Code Search API-based enumeration
GitHub Action Run Log Parsing to identify Self-Hosted Runners
Bulk Repo Sparse Clone Features
GitHub Action Workflow Parsing
Automated Command Execution Fork PR Creation
Automated Command Execution Workflow Creation
SOCKS5 Proxy Support
HTTPS Proxy Support
To see this hidden content, you must like this content.