- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,456
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
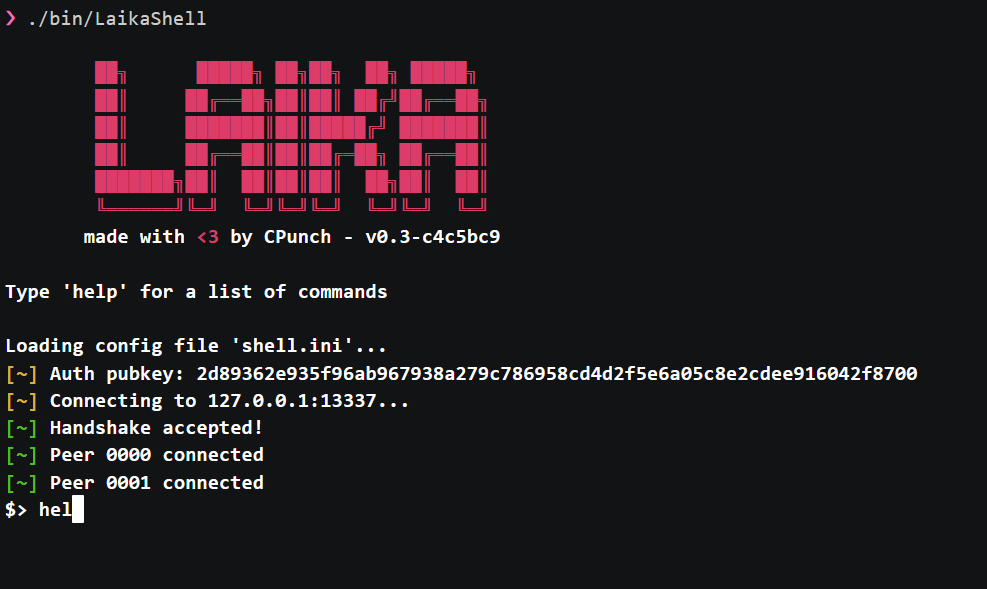
Laika is a simple cross-platform Remote Access Toolkit stack for educational purposes. It allows encrypted communication across a custom binary protocol. The bot client supports both Windows & Linux environments, while the shell & CNC server specifically target Linux environments. Laika is meant to be small and discreet, Laika believes in hiding in plain sight.
Some notable features thus far:
Lightweight, the bot alone is 183kb (MinSizeRel) and uses very little resources minimizing Laika's footprint.
Authentication & packet encryption using LibSodium and a predetermined public CNC key. (generated with bin/genKey)
Server and Shell configuration through .ini files.
Ability to open shells remotely on the victim's machine.
Persistence across reboot: (toggled with -DLAIKA_PERSISTENCE=On)
Persistence via Cron on Linux-based systems.
Persistence via Windows Registry.
Uses obfuscation techniques also seen in the wild (string obfuscation, tiny VMs executing sensitive operations, etc.)
Simple configuration using CMake:
Setting keypairs (-DLAIKA_PUBKEY=? -DLAIKA_PRIVKEY=?, etc.)
Obfuscation modes
To see this hidden content, you must like this content.