- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,456
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
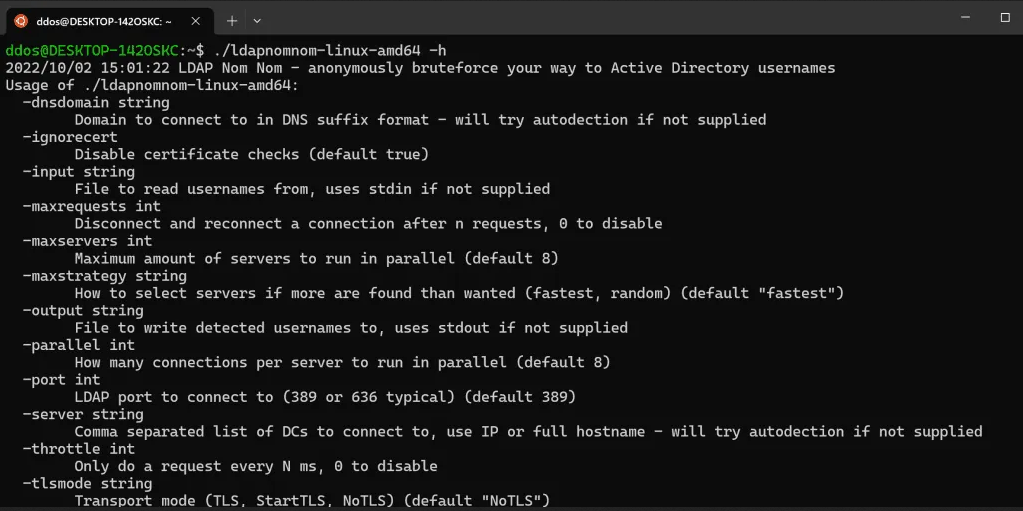
LDAP Nom Nom
Anonymously bruteforce Active Directory usernames from Domain Controllers by abusing LDAP Ping requests (cLDAP)
Looks for enabled normal user accounts. No Windows audit logs were generated. High-speed ~ up to 10K/sec – go beyond 25K/sec with multiple servers!
Tries to autodetect DC from environment variables on domain joined machines or falls back to machine hostname FQDN DNS suffix
Reads usernames to test from stdin (default) or file
Outputs to stdout (default) or file
Parallelized, multiple connections to multiple servers (defaults to 8 servers, 8 connections per server)
Shows a progressbar if you’re using both input and output files
Evasive maneuvers: Use –throttle 20 for a 20ms delay between each request (slows everything down to a crawl)
Evasive maneuvers: Use –maxrequests 1000 to close the connection and reconnect after 1000 requests in each connection (try to avoid detection based on traffic volume)
To see this hidden content, you must like this content.