- Joined
- Jan 8, 2019
- Messages
- 56,607
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,453
- Points
- 2,313
- Credits
- 32,590
6 Years of Service
76%
PE-Packer
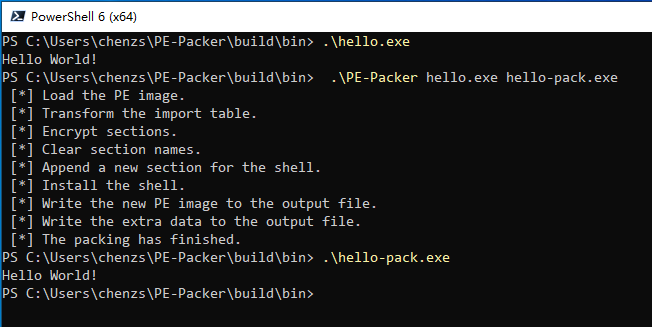
PE-Packer is a simple packer for Windows PE files. The new PE file after packing can obstruct the process of reverse engineering.
It will do the following things when packing a PE file:
Transforming the original import table.
Encrypting sections.
Clearing section names.
Installing the shell-entry.
When running a packed PE file, the shell-entry will decrypt and load the original program as follows:
Decrypting sections.
Initializing the original import table.
Relocation.
Before packing, using some disassembly tools can disassemble the executable file to analyze the code, such as IDA Pro.
To see this hidden content, you must like this content.