- Joined
- Jan 8, 2019
- Messages
- 56,609
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,454
- Points
- 2,313
- Credits
- 32,610
6 Years of Service
76%
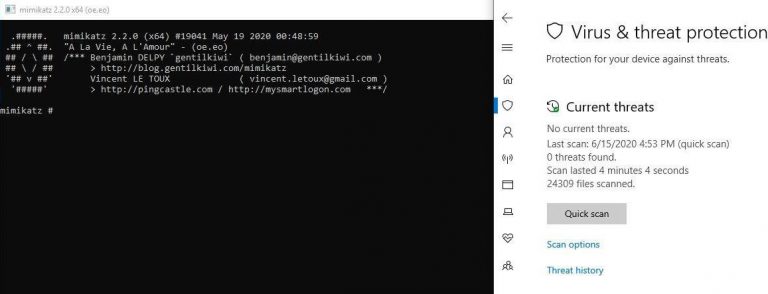
The phases of the development that will be described in detail are:
set up the development environment with Mingw-w64 and LLVM
shellcode injection with syscall inlining via NTDLL in-memory scraping (x86-64 only)
user-land hooks removal from in-memory NTDLL to retrieve correct syscall numbers
upgrade the shellcode injector to a full PE packer with Donut
ensure the produced shellcode is always different at each build with sgn
ensure the compiled loader is always different at each build with LLVM obfuscation
implement some simple anti-debug tricks for the initial loader
For the details of the techniques, please read the blog.
To see this hidden content, you must like this content.