dEEpEst
☣☣ In The Depths ☣☣
Staff member
Administrator
Super Moderator
Hacker
Specter
Crawler
Shadow
- Joined
- Mar 29, 2018
- Messages
- 13,861
- Solutions
- 4
- Reputation
- 27
- Reaction score
- 45,549
- Points
- 1,813
- Credits
- 55,350
7 Years of Service
56%
By it4chis3c
Impact description
A vulnerability existed in the OTP verification logic, which enabled me to bypass mobile number authentication during both account registration and login by manipulating the server response. The problem occurs because OTP is not being validated properly on the client side, allowing the account to be accessed without the need to verify a valid phone number.Steps to Reproduce
Step 1. Navigate to the URL:
This link is hidden for visitors. Please Log in or register now.
Step 2. Fill the registration form with all the legit details except Mobile number.
Step 3. Submit the form & it will prompt for OTP verification input.
Step 4. Enter wrong OTP and intercept this request using Burp Suite
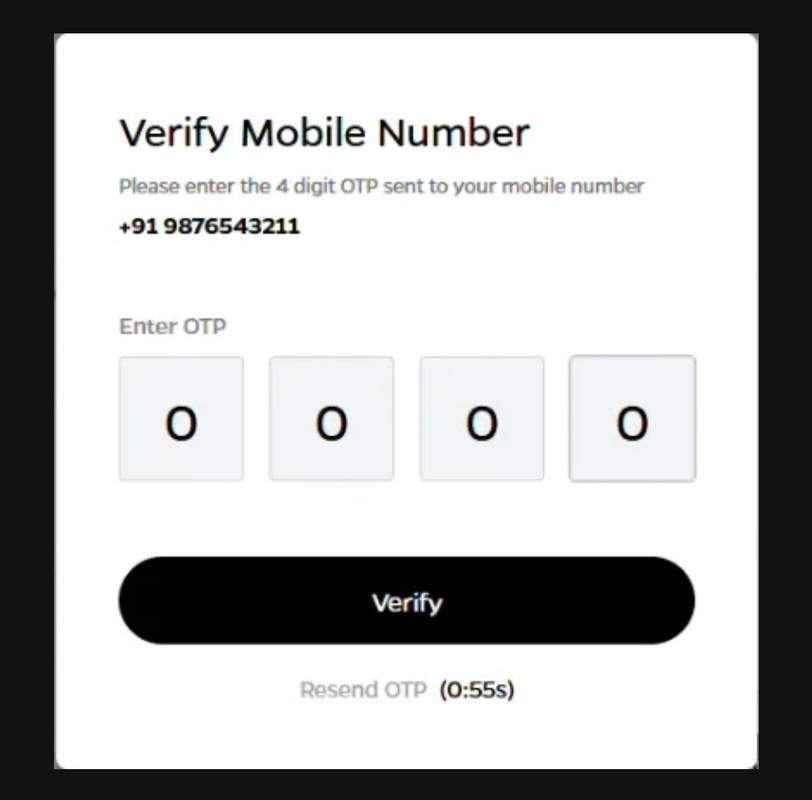
Step 5. Right click and go to “Do intercept” then “Response to this request” and click “Forward”
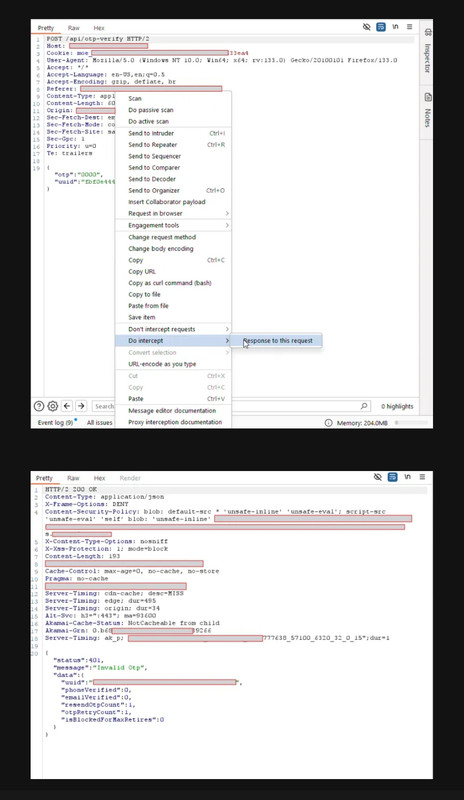
Step 6. In response JSON body, replace:
(i) “401” to “200”
(ii) “Invalid” to “Valid”
(iii) “phoneVerfified” and “emailVerified” parameters from the value “0” to “1”.
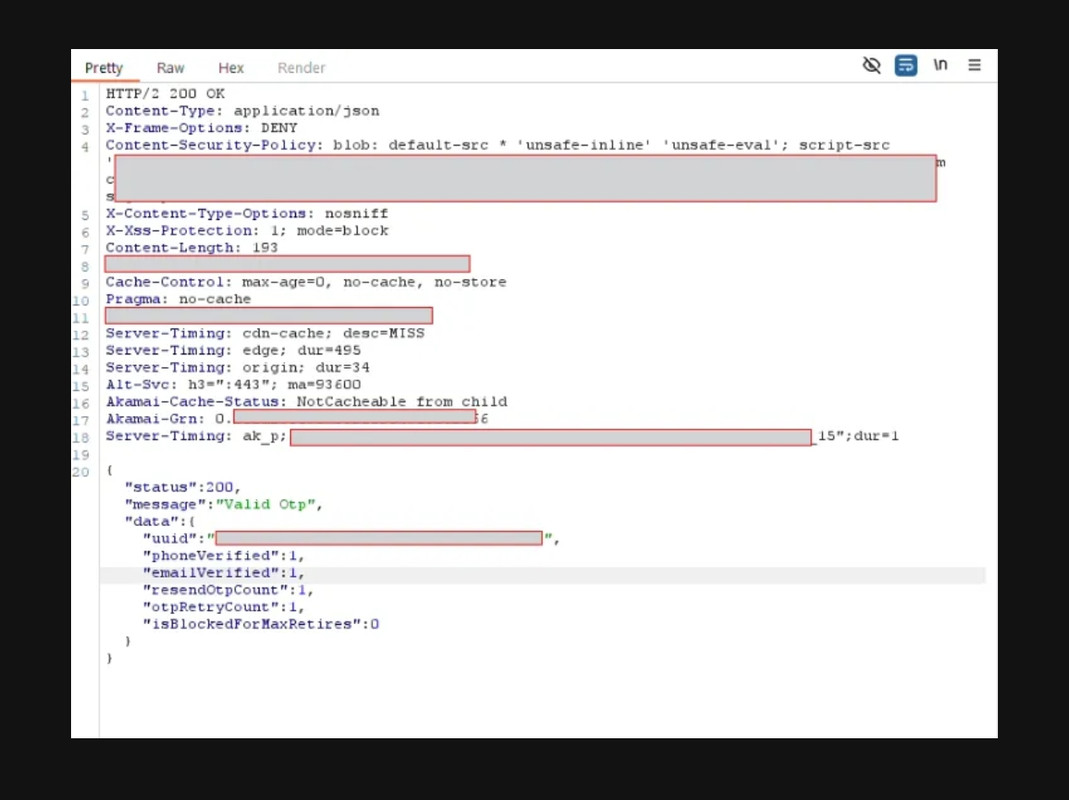
Step 7. Forward the response and the user gets registered successfully.
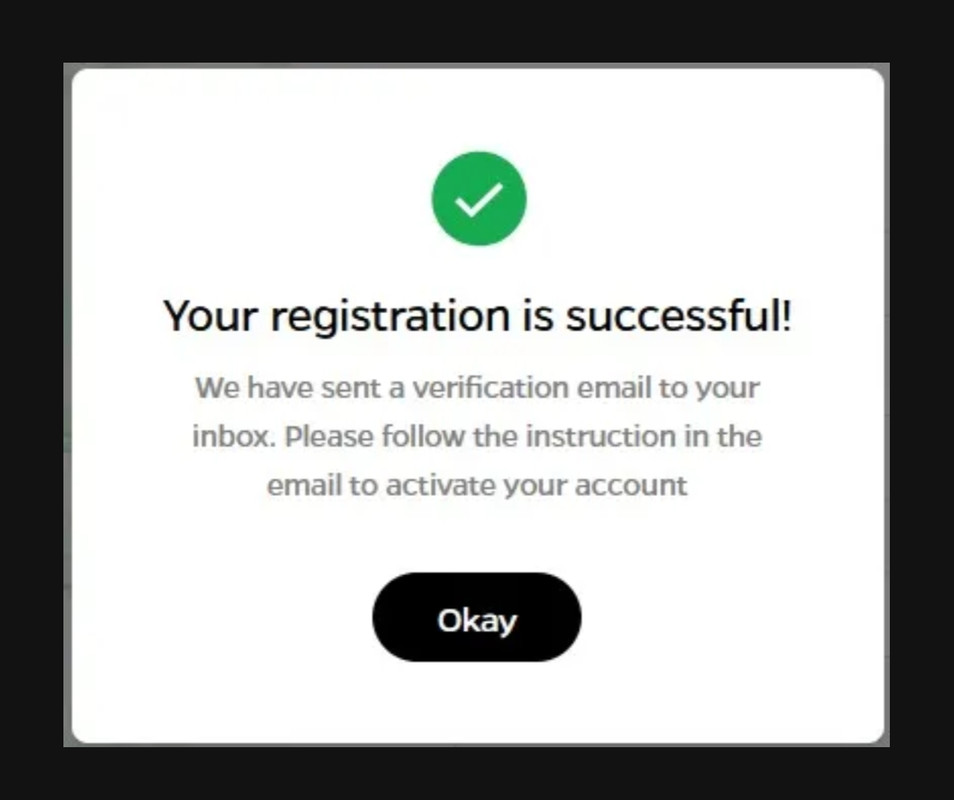
Step 8. Try to login with the email id and password used at the time of registration.
Step 9. Resend verification link and do verify the email id and account if not received the email.
Step 10. Again, login with the same credentials and you’ll now get logged in successfully.
Step 11. It prompted for OTP validation again after login, So, I used the step 4,5,6 & 7 to bypass the verification.
Step 12. Finally, the user is being registered at server side due to a vulnerability present in client-side without proper mobile no. and OTP validation.
Note: Due to the program’s non-disclosure privacy and policy, I can’t disclose the dashboard but can show you the masked POC -
Tip to be noted:
Whenever you see the input data visible in the request header or body, then do intercept its response in burp suite and look for any editable data in response body related to the input value.