- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,455
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
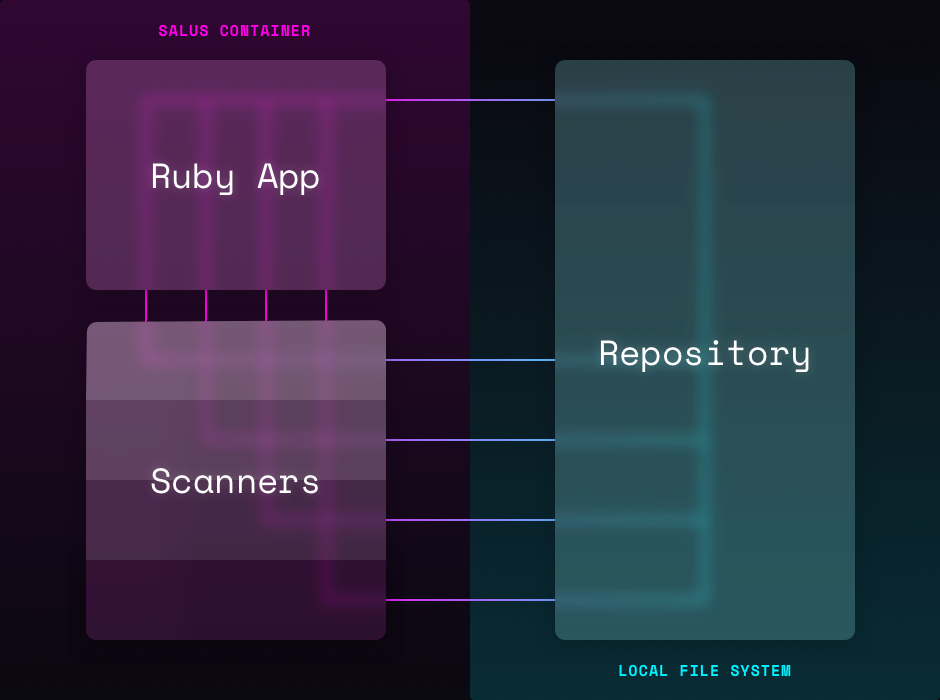
Salus: Guardian of Code Safety and Security
Salus (Security Automation as a Lightweight Universal Scanner), named after the Roman goddess of protection, is a tool for coordinating the execution of security scanners. You can run Salus on a repository via the Docker daemon and it will determine which scanners are relevant, run them and provide the output. Most scanners are other mature open source projects which we include directly in the container.
Salus is particularly useful for CI/CD pipelines because it becomes a centralized place to coordinate scanning across a large fleet of repositories. Typically, scanners are configured at the repository level for each project. This means that when making org-wide changes to how the scanners are run, each repository must be updated. Instead, you can update Salus and all builds will instantly inherit the change.
Salus supports a powerful configuration that allows for global defaults and local tweaks. Finally, Salus can report metrics on each repository, such as what packages are included or what concerns exist. These reports can be centrally evaluated in your infrastructure to allow for scalable security tracking.
Supported Scanners
Bandit – Execution of Bandit 1.6.2, looks for common security issues in Python code.
Brakeman – Execution of Brakeman 4.10.0, looks for vulnerable code in Rails projects.
semgrep – Execution of semgrep 0.36.0 which looks for semantic and syntactical patterns in code at the AST level.
BundleAudit – Execution of bundle-audit 0.7.0.1, looks for CVEs in ruby gem dependencies.
Gosec – Execution of gosec 2.7.0, looks for security problems in go code.
npm audit – Execution of npm audit 6.14.8 which looks for CVEs in node module dependencies.
yarn audit – Execution of yarn audit 1.22.0 which looks for CVEs in node module dependencies.
PatternSearch – Execution of sift 0.9.0, looks for certain strings in a project that might be dangerous or could require that certain strings be present.
Cargo Audit – Execution of Cargo Audit 0.14.0 Audit Cargo.lock files for crates with security vulnerabilities reported to the RustSec Advisory Database
Changelog v2.12
Added
#415 #417 #429 #432 CycloneDX integration
#413 #415 #419 #420 #421 #430 CycloneDX language support (Ruby, Rust, Python, Node Modules, Go)
Changed
#411 Updated ReportGoDep to use go.sum/go.mod in addition to gopkg.lock
#418 Scanner timeout values can now be floating point numbers
To see this hidden content, you must like this content.