- Joined
- Jan 8, 2019
- Messages
- 56,607
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,453
- Points
- 2,313
- Credits
- 32,590
6 Years of Service
76%
Security Onion
Security Onion is a free and open source Linux distribution for intrusion detection, enterprise security monitoring, and log management. It includes Elasticsearch, Logstash, Kibana, Snort, Suricata, Bro, OSSEC, Sguil, Squert, NetworkMiner, and many other security tools. The easy-to-use Setup wizard allows you to build an army of distributed sensors for your enterprise in minutes!
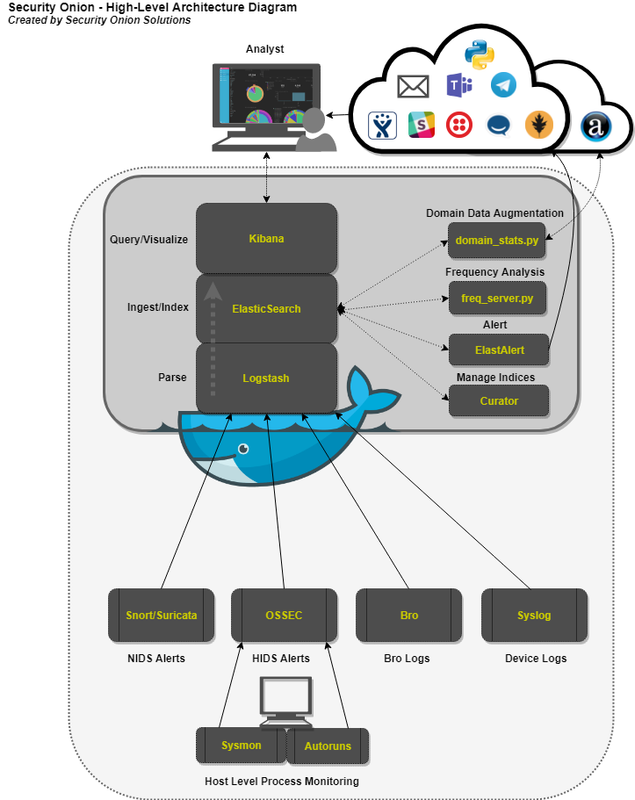
Below are several diagrams to represent the current architecture and deployment scenarios for Security Onion on the Elastic Stack.
Core Components
Logstash – Parse and format logs.
Elasticsearch – Ingest and index logs.
Kibana – Visualize ingested log data.
Auxiliary Components
Curator – Manage indices through scheduled maintenance.
ElastAlert – Query Elasticsearch and alert on user-defined anomalous behavior or other interesting bits of information.
FreqServer -Detect DGAs and find random file names, script names, process names, service names, workstation names, TLS certificate subjects and issuer subjects, etc.
DomainStats – Get additional info about a domain by providing additional context, such as creation time, age, reputation, etc.
Changelog v2.0 RC1
Re-branded 2.0 to give it a fresh look
All documentation has moved to our docs site
soup is alive! Note: This tool only updates Security Onion components. Please use the built-in OS update process to keep the OS and other components up to date.
so-import-pcap is back! See the so-import-pcap docs here.
Fixed issue with so-features-enable
Users can now pivot to PCAP from Suricata alerts
ISO install now prompts users to create an admin/sudo user instead of using a default account name
The web email & password set during setup is now used to create the initial accounts for TheHive, Cortex, and Fleet
Fixed issue with disk cleanup
Changed the default permissions for /opt/so to keep non-priviledged users from accessing salt and related files
Locked down access to certain SSL keys
Suricata logs now compress after they roll over
Users can now easily customize shard counts per index
Improved Elastic ingest parsers including Windows event logs and Sysmon logs shipped with WinLogbeat and Osquery (ECS)
Elastic nodes are now “hot” by default, making it easier to add a warm node later
so-allow now runs at the end of an install so users can enable access right away
Alert severities across Wazuh, Suricata and Playbook (Sigma) have been standardized and copied to event.severity:
1-Low / 2-Medium / 3-High / 4-Critical
Initial implementation of alerting queues:
Low & Medium alerts are accessible through Kibana & Hunt
High & Critical alerts are accessible through Kibana, Hunt and sent to TheHive for immediate analysis
ATT&CK Navigator is now a statically-hosted site in the nginx container
Playbook
All Sigma rules in the community repo (500+) are now imported and kept up to date
Initial implementation of automated testing when a Play’s detection logic has been edited (i.e., Unit Testing)
Updated UI Theme
Once authenticated through SOC, users can now access Playbook with analyst permissions without login
Kolide Launcher has been updated to include the ability to pass arbitrary flags – new functionality sponsored by SOS
Fixed issue with Wazuh authd registration service port not being correctly exposed
Added option for exposure of Elasticsearch REST API (port 9200) to so-allow for easier external querying/integration with other tools
Added option to so-allow for external Strelka file uploads (e.g., via strelka-fileshot)
Added default YARA rules for Strelka – default rules are maintained by Florian Roth and pulled from https://github.com/Neo23x0/signature-base
Added the ability to use custom Zeek scripts
Renamed “master server” to “manager node”
Improved unification of Zeek and Strelka file data
To see this hidden content, you must like this content.