- Joined
- Jan 8, 2019
- Messages
- 56,605
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,451
- Points
- 2,313
- Credits
- 32,570
6 Years of Service
76%
Security Onion
Security Onion is a free and open source Linux distribution for intrusion detection, enterprise security monitoring, and log management. It includes Elasticsearch, Logstash, Kibana, Snort, Suricata, Bro, OSSEC, Sguil, Squert, NetworkMiner, and many other security tools. The easy-to-use Setup wizard allows you to build an army of distributed sensors for your enterprise in minutes!
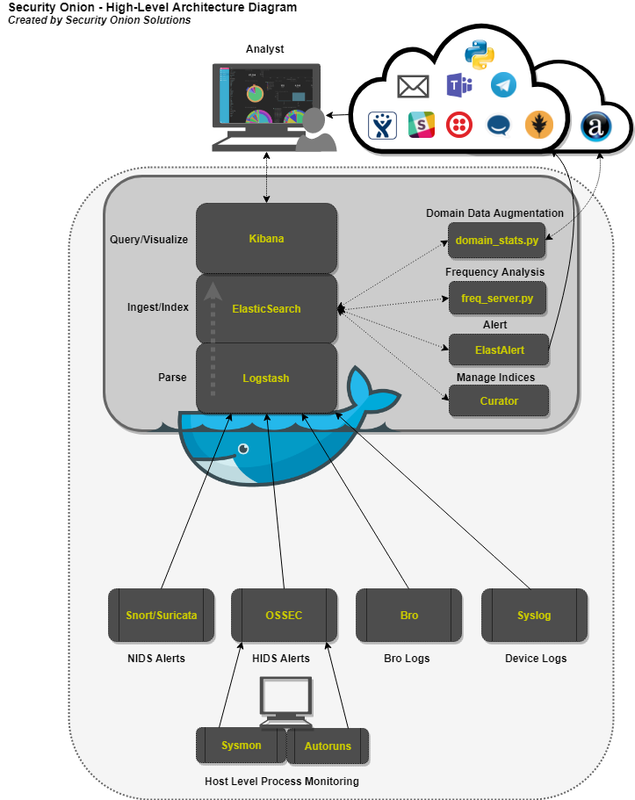
Below are several diagrams to represent the current architecture and deployment scenarios for Security Onion on the Elastic Stack.
Core Components
Logstash – Parse and format logs.
Elasticsearch – Ingest and index logs.
Kibana – Visualize ingested log data.
Auxiliary Components
Curator – Manage indices through scheduled maintenance.
ElastAlert – Query Elasticsearch and alert on user-defined anomalous behavior or other interesting bits of information.
FreqServer -Detect DGAs and find random file names, script names, process names, service names, workstation names, TLS certificate subjects and issuer subjects, etc.
DomainStats – Get additional info about a domain by providing additional context, such as creation time, age, reputation, etc.
Changelog v2.3.90
Changes
FEATURE: Add ASN annotation for GeoIP #5068
FEATURE: Add Endgame Support for Security Onion #6166
FEATURE: Add TI Module #5916
FEATURE: Add additional flags to stenographer config #5851
FEATURE: Add filebeat, auditbeat, and metricbeat downloads to SOC Download screen #5849
FEATURE: Add logstash and redis input plugins to telegraf #5960
FEATURE: Add so-deny script for removing access from firewall and other apps #4621
FEATURE: Add support for escalation to Elastic Cases #6048
FEATURE: Allow for Kibana customizations via pillar #3933
FEATURE: Allow users to set their profile information #5846
FEATURE: Allow vlan tagged NICs to be used as management interface #3687
FEATURE: Create Pipeline Overview Dashboard for Grafana #6177
FEATURE: Create script to reset elastic auth passwords #6206
FEATURE: Enable Kibana Settings for encryption #6146
FEATURE: Expose new user profile field for specifying a custom note about a user #5847
FEATURE: HTTP module for SOC event escalation #5791
FEATURE: Increase password lengths, provide a way to change existing passwords #6043
FEATURE: Indicate that setup has completed at the very end of sosetup.log #5032
FEATURE: Prevent SOUP from running if there is an issue with the manager pillar #5809
FEATURE: Provide quick-select date ranges from Hunt/Alerts date range picker #5953
FEATURE: SOC Hunt Timeline/Charts should be collapsible #5114
FEATURE: Support Ubuntu 20.04 #601
FEATURE: setup should run so-preflight #3497
FIX: ACNG sometimes returns 503 errors when updating Ubuntu through the manager #6151
FIX: Add details to Setup for Install Type menus #6105
FIX: Adjust timeout in check_salt_minion_status in so-functions #5818
FIX: All templates should honor replica settings #6005
FIX: Clear holds on Ubuntu installs #5588
FIX: Consider making the airgap option only settable on the manager #5914
FIX: Docker containers should not start unless file events are completed #5955
FIX: Ensure soc_users_roles file is cleaned up if incorrectly mounted by Docker #5952
FIX: Favor non-aggregatable data type when a cache field has multiple conflicting data types #5962
FIX: Firefox tooltips stuck on Hunt and Alerts screens #6010
FIX: Grafana sensor graphs only show interface graphs when selected individually #6007
FIX: Kibana saved objects #5193
FIX: Modify Steno packet loss calculation to show point in time packet loss #6060
FIX: Remove CURCLOSEDAYS prompt in Setup since it is no longer used #6084
FIX: Remove references to xenial (Ubuntu 16.04) from setup #4292
FIX: Remove unnecessary screens from Analyst Setup #5615
FIX: SOC docker should not start until file managed state runs #5954
FIX: SOC unable to acknowledge alerts when not grouped by rule.name #5221
FIX: Setup should ask if new or existing distributed deployment #6115
FIX: Setup should prevent invalid characters in Node Description field #5937
FIX: Support non-WEL Beats #6063
FIX: Unnecessary Port Binding for so-steno #5981
FIX: Use yaml.safe_load() in so-firewall (thanks to @clairmont32) #5750
FIX: Zeek state max depth not working #5558
FIX: so-ip-update should grant mysql root user access on new IP #4811
FIX: docker group can be given gid used by salt created groups #6071
FIX: packetloss.sh gives an error every 10 min though ZEEK is disabled #5759
FIX: so-import-evtx elastic creds & logging #6065
FIX: so-user delete function causes re-migration of user roles #5897
FIX: wazuh-register-agent times out after 15 minutes lower to 5 minutes #5794
FIX: yum pkg.clean_metadata occasionally fails during setup #6113
UPGRADE: ElastAlert to 2.2.2 #5751
UPGRADE: Elastic to 7.15.2 #5752
UPGRADE: FleetDM to 4.5 #6188
UPGRADE: Grafana to 8.2.3 #5852
UPGRADE: Kratos to 0.7.6-alpha.1 #5848
UPGRADE: Redis to 6.2.6 #6140
UPGRADE: Suricata to 6.0.4 #6274
UPGRADE: Telegraf to 1.20.3 #6075
To see this hidden content, you must like this content.