- Joined
- Jan 8, 2019
- Messages
- 56,612
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,454
- Points
- 2,313
- Credits
- 32,640
6 Years of Service
76%
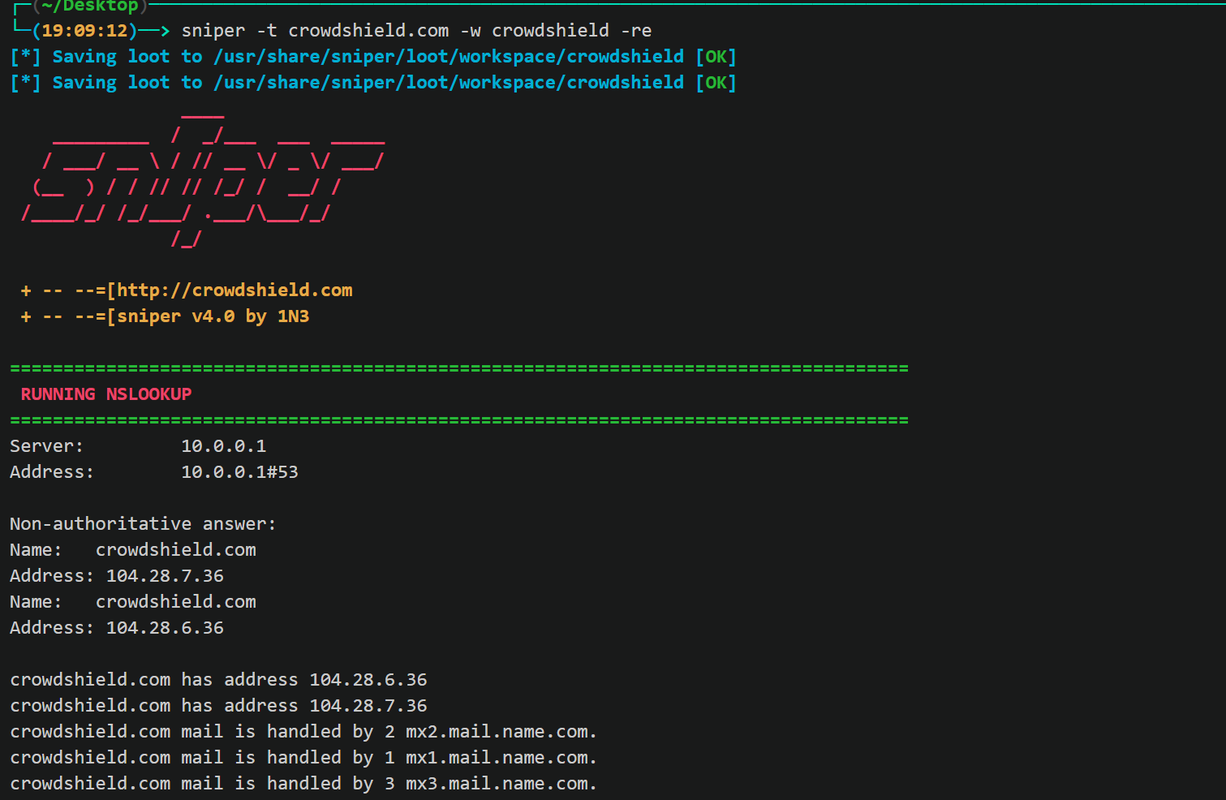
Sn1per Community Edition is an automated scanner that can be used during a penetration test to enumerate and scan for vulnerabilities. Sn1per Professional is Xero Security’s premium reporting add-on for Professional Penetration Testers, Bug Bounty Researchers and Corporate Security teams to manage large environments and pentest scopes.
FEATURES:
Automatically collects basic recon (ie. whois, ping, DNS, etc.)
Automatically launches Google hacking queries against a target domain
Automatically enumerates open ports via Nmap port scanning
Automatically brute forces sub-domains gathers DNS info and checks for zone transfers
Automatically checks for sub-domain hijacking
Automatically runs targeted Nmap scripts against open ports
Automatically runs targeted Metasploit scan and exploit modules
Automatically scans all web applications for common vulnerabilities
Automatically brute forces ALL open services
Automatically test for anonymous FTP access
Automatically runs WPScan, Arachni and Nikto for all web services
Automatically enumerates NFS shares
Automatically test for anonymous LDAP access
Automatically enumerate SSL/TLS cyphers, protocols and vulnerabilities
Automatically enumerate SNMP community strings, services and users
Automatically list SMB users and shares, check for NULL sessions and exploit MS08-067
Automatically exploit vulnerable JBoss, Java RMI and Tomcat servers
Automatically tests for open X11 servers
Auto-pwn added for Metasploitable, ShellShock, MS08-067, Default Tomcat Creds
Performs high-level enumeration of multiple hosts and subnets
Automatically integrates with Metasploit Pro, MSFConsole and Zenmap for reporting
Automatically gathers screenshots of all websites
Create individual workspaces to store all scan output
Changelog
v8.3 – Added Github subdomain retrieval (requires API key/conf options enabled)
v8.3 – Added NMAP_OPTIONS setting to sniper.conf to configure optional NMap scan settings
v8.3 – Added option to specify custom Sn1per configuration via (-c) switch
v8.3 – Created several custom config files to select from, including: bug_bounty_quick, bug_bounty_max_javascript, super_stealth_mode, webpwn_only + more
v8.3 – Added workspace –export option to backup/export a workspace
v8.3 – Added flyover mode tuning options to sniper.conf
v8.3 – Added GitGraber automated Github leak search (https://github.com/hisxo/gitGraber)
v8.3 – Added static Javascript parsing for sub-domains, URL’s, path relative links and comments
v8.3 – Added js-beautifier
v8.3 – Added LinkFinder Javascript link finder (https://github.com/GerbenJavado/LinkFinder)
v8.3 – Added fprobe HTTP probe checker (https://github.com/theblackturtle/fprobe)
v8.3 – Added Cisco RV320 and RV325 Unauthenticated Remote Code Execution CVE-2019-1653 MSF exploit
v8.3 – Improved performance of ‘stealth’ and ‘recon’ modes
v8.3 – Updated default port lists
v8.3 – Improved performance of all port scans
v8.3 – Removed all pip v2 commands from installer
v8.3 – Added fix for missing Amass package
v8.3 – Added sniper.conf options for OPENVAS_HOST and OPENVAS_PORT selection for remote instances
v8.3 – Improved ‘vulnscan’ mode via OpenVAS to scan the same asset multiple times with improved error handling
To see this hidden content, you must like this content.