- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,456
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
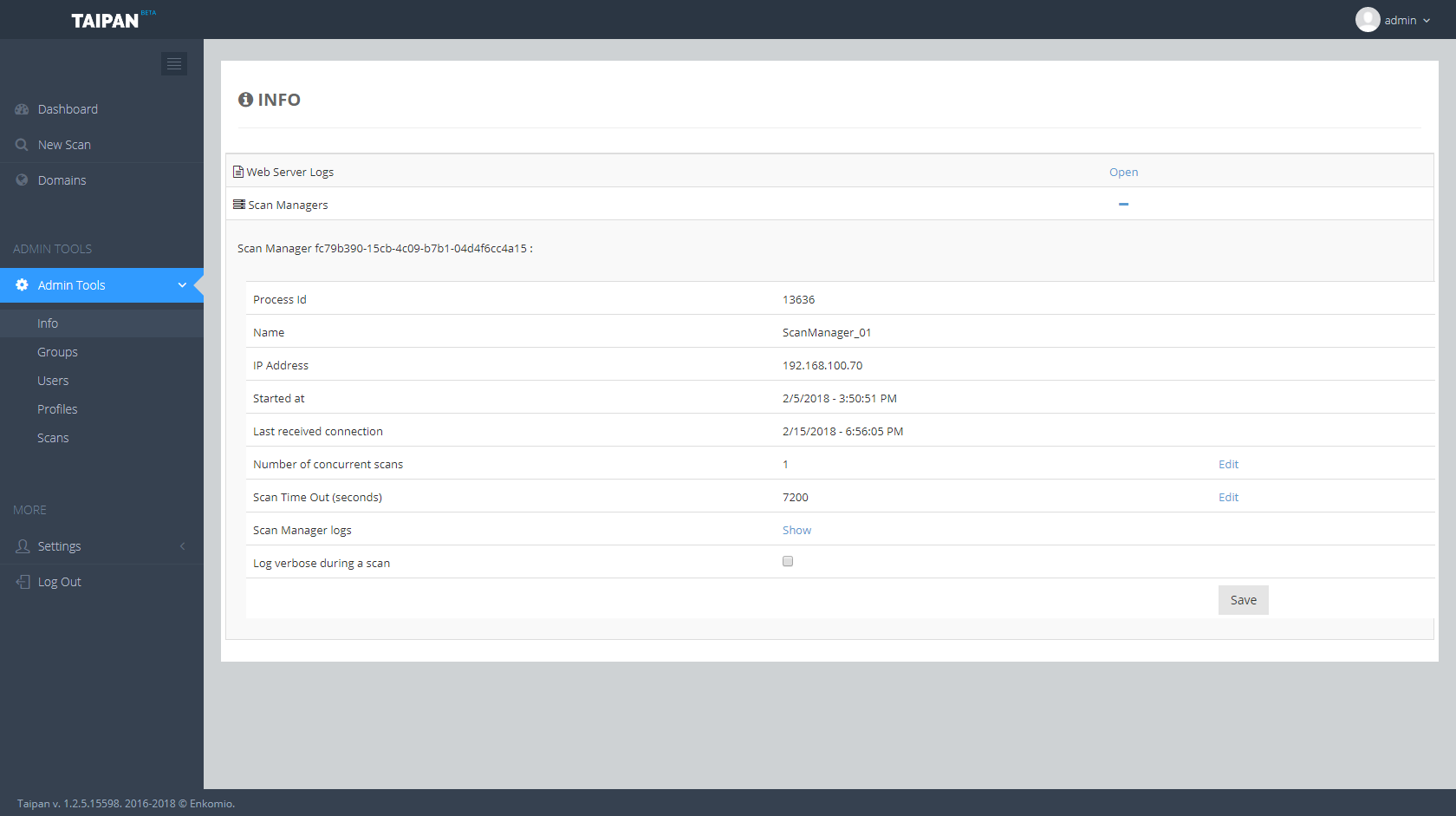
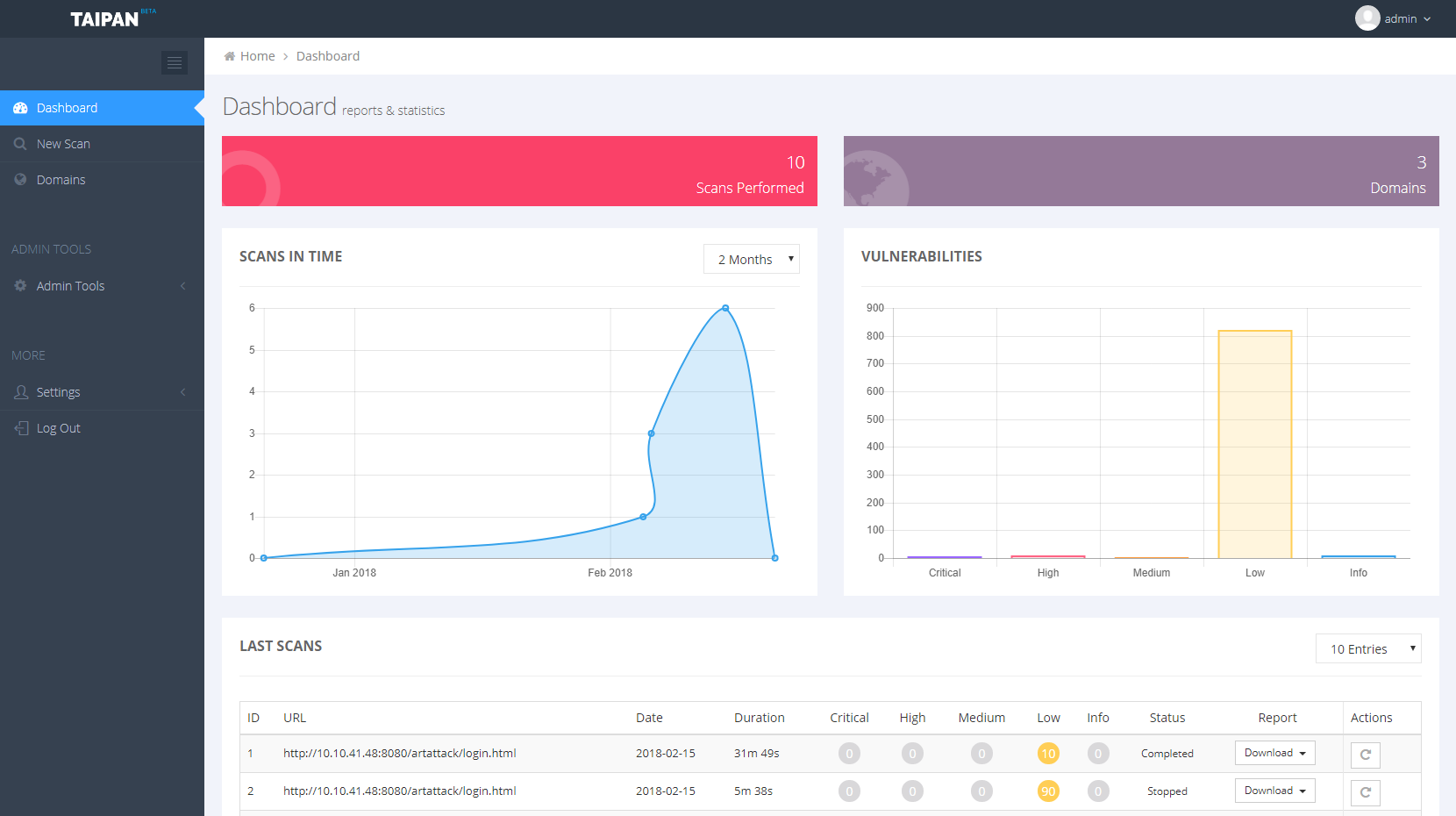
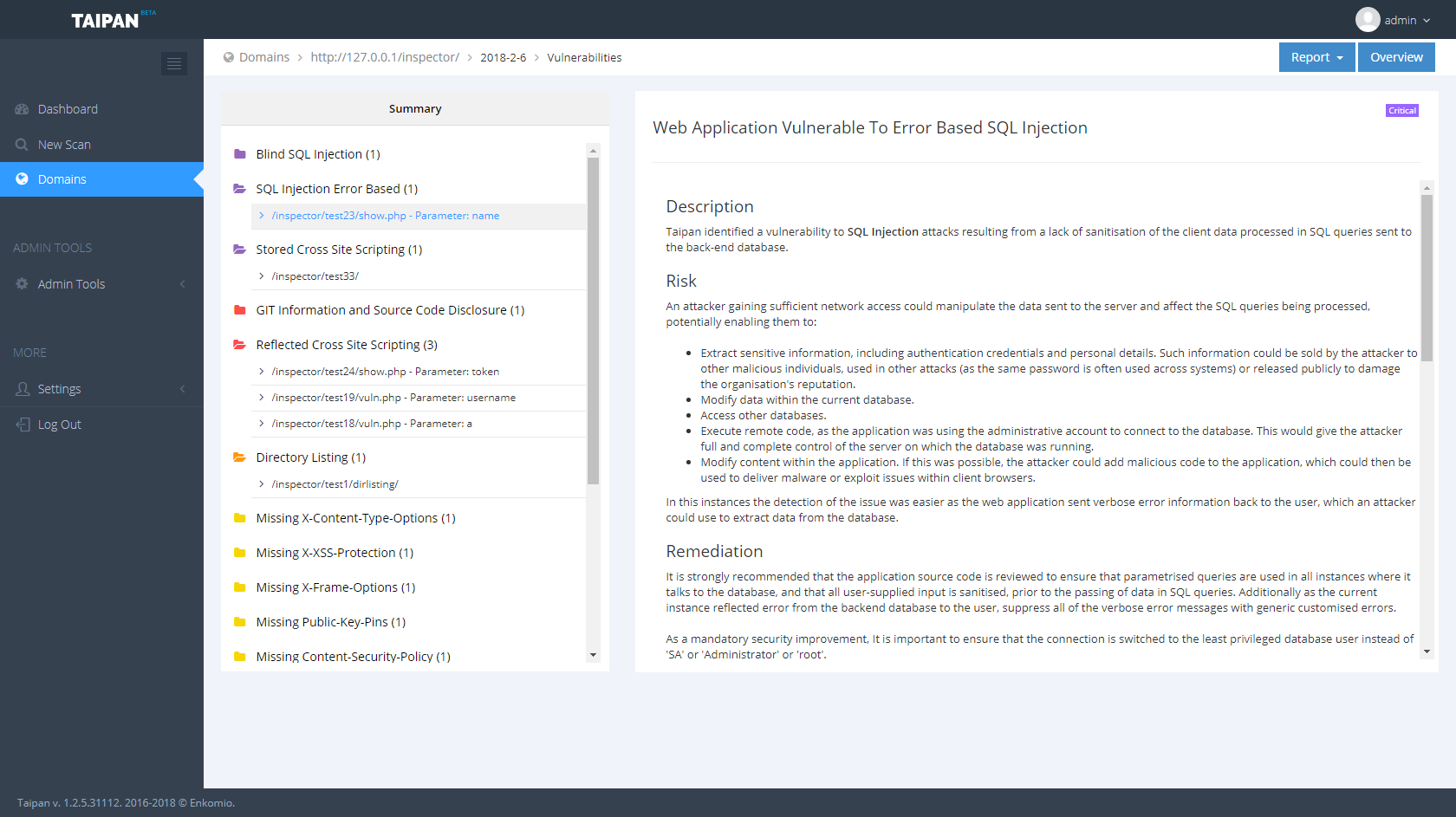
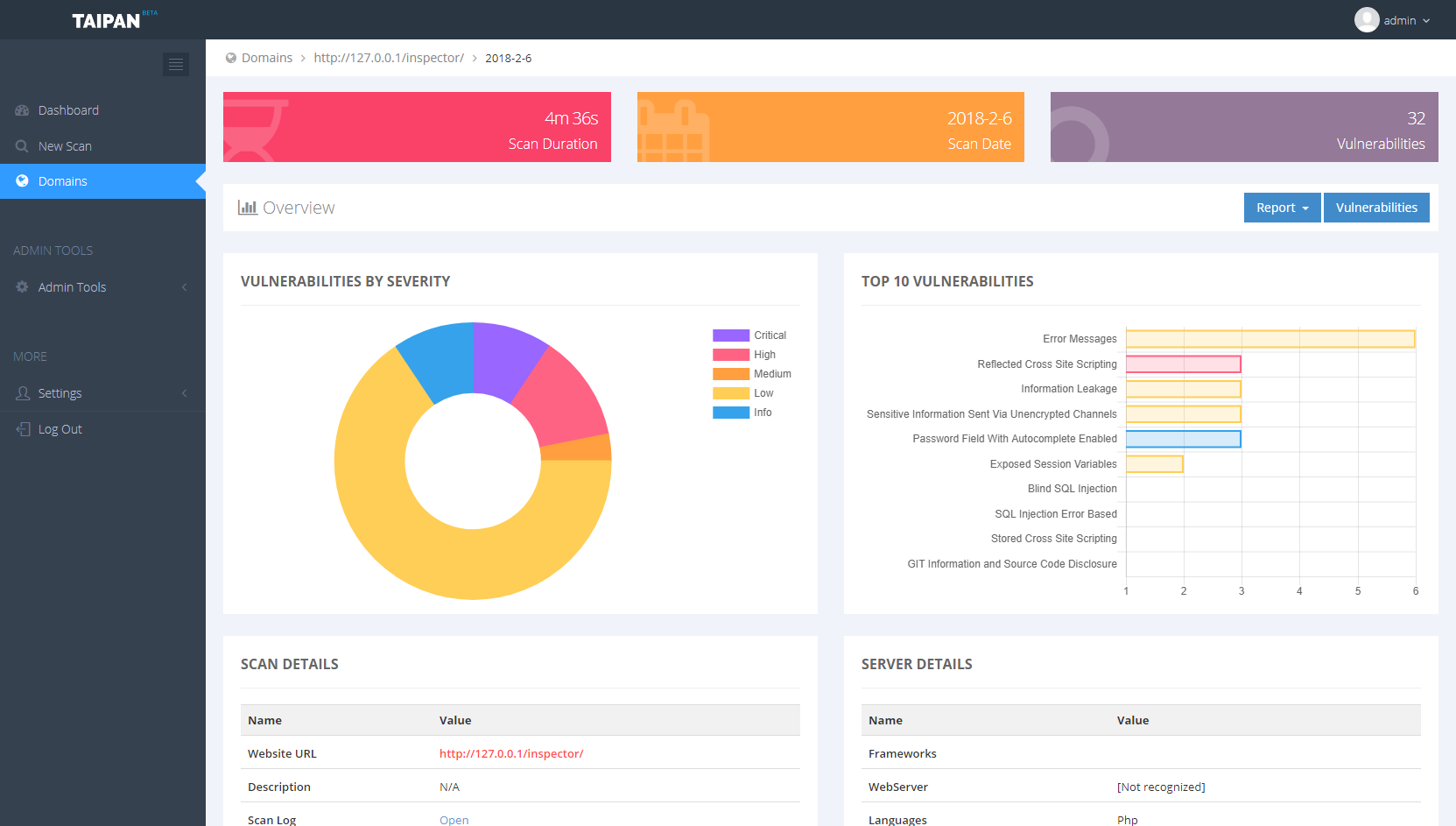
Taipan is a an automated web application scanner that allows to identify web vulnerabilities in an automatic fashion. This project is the core engine of a broader project which includes other components, like a web dashboard where you can manage your scans, download a PDF report and a scanner agent to run on specific host. Below are some screenshots of the Taipan dashboard:
To see this hidden content, you must like this content.
Code:
https://asciinema.org/a/166362Taipan is composed of four main components:
Web Application fingerprinter
it inspects the given application in order to identify if it is a COTS application. If so, it extracts the identified version. This components is very important since it allows to identify vulnerable web applications.
Hidden Resource Discovery
this component scans the application in order to identify resources that are not directly navigable or that shouldn't be accessed, like secret pages or test pages.
Crawler
This component navigates the web site in order to provide to the other components a list of pages to analyze. It allows to mutate the request in order to find not so common pathes.
Vulnerability Scanner
this component probes the web application and tries to identify possible vulnerabilities. It is composed of various AddOn in order to easily expand its Knowledge Base. It is also in charge for the identification of know vulnerabilities which are defined by the user.