- Joined
- Jan 8, 2019
- Messages
- 56,605
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,449
- Points
- 2,313
- Credits
- 32,570
6 Years of Service
76%
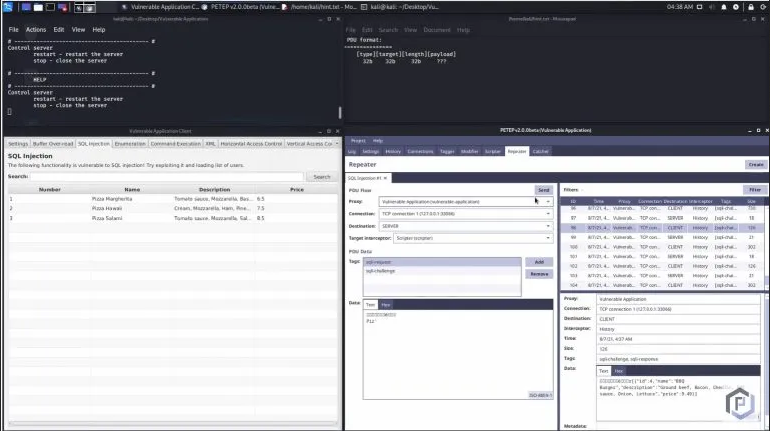
A vulnerable client-server application (VuCSA) is made for learning/presenting how to perform penetration tests of non-http thick clients. It is written in Java (with JavaFX graphical user interface).
Currently, the vulnerable application contains the following challenges:
Buffer Over-read (simulated)
Command Execution
SQL Injection
Enumeration
XML
Horizontal Access Control
Vertical Access Control
If you want to know how to solve these challenges, take a look at the PETEP website, which describes how to use the open-source tool PETEP to exploit them.
Tip: Before you start hacking, do not forget to check the data structure of the messages below.
To see this hidden content, you must like this content.