- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,457
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
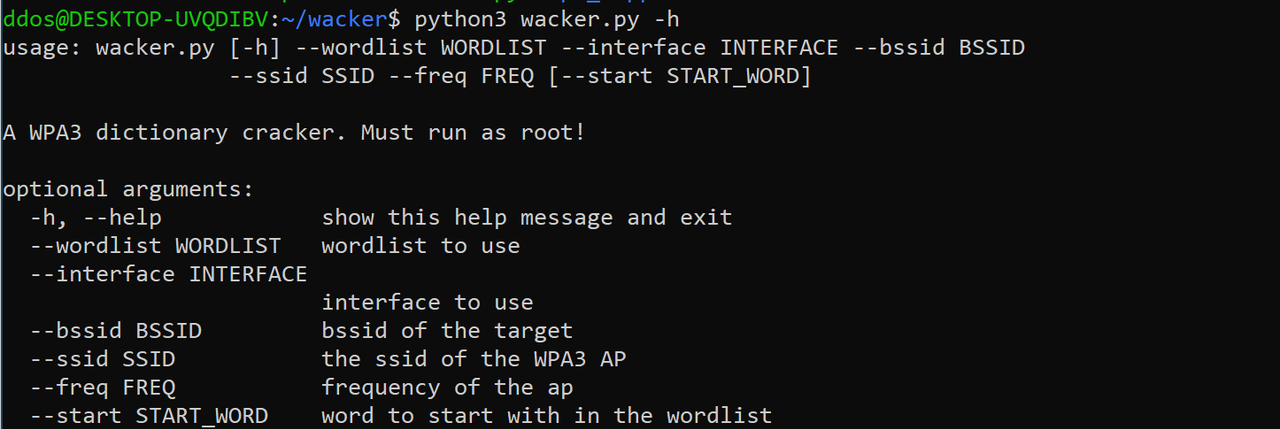
A set of scripts to help perform an online dictionary attack against a WPA3 access point. Wacker leverages the wpa_supplicant control interface to control the operations of the supplicant daemon and to get status information and event notifications ultimately helping speedup connection attempts during brute force attempts.
Files of interest
wacker is quite verbose. Files of interest are found under /tmp/wpa_supplicant/
wlan1: one end of the uds
wlan1_client: one end of the uds
wlan1.conf: initial wpa_supplicant conf needed
wlan1.log: supplicant output
wlan1.pid: pid file for the wpa_supplciant instance
wlan1_wacker.log: wacker debug output
Caution
wacker doesn’t handle acls put in place by the target WPA3 AP. Meaning, the current code always uses the same MAC address. If the target AP blacklists our MAC address then the script won’t differentiate between a true auth failure and our blacklisted MAC being rejected. This will mean that we’ll consider the true password as a failure. One way to solve…. we would have to add macchanger to the source at the expense of slowdown.
wacker will seemingly pause everything so often as the AP will issue a backoff timeout. This will cause the metric display to seemingly pause and then start again. This is the expected behavior.
To see this hidden content, you must like this content.