dEEpEst
☣☣ In The Depths ☣☣
Staff member
Administrator
Super Moderator
Hacker
Specter
Crawler
Shadow
- Joined
- Mar 29, 2018
- Messages
- 13,861
- Solutions
- 4
- Reputation
- 27
- Reaction score
- 45,549
- Points
- 1,813
- Credits
- 55,350
7 Years of Service
56%
DNS Tunneling
 Welcome to the world of digital security!
Welcome to the world of digital security!
Today we will talk about DNS tunneling — one of the most dangerous techniques used by bad guys.
⏺A bit of history: DNS tunneling was first discovered back in 1998. Then Oscar Pearson made a discovery and revealed how DNS can be used for hidden attacks. And in 2004, at the Black Hat conference, it had already become a full-fledged tool for hackers. Since then, this method has been actively used to transfer data, hiding in regular traffic.
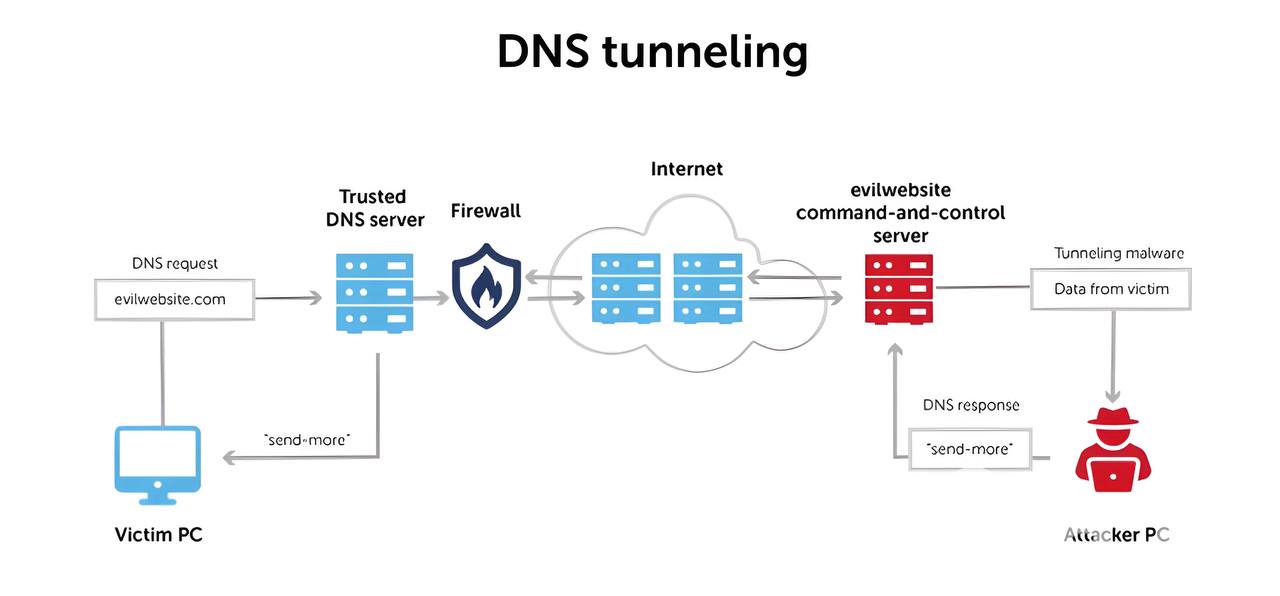
⏺How does DNS tunneling work? Let's imagine: there is a hypothetical attacker, and he disguises his not very legal actions as regular legitimate DNS traffic. Such a peculiar spy in a police officer's suit — he looks inconspicuous, but in fact he is up to something bad.
 The attacker starts by using DNS to hide his actions. And since DNS traffic is almost always allowed and not checked, it can operate freely in such an environment.
The attacker starts by using DNS to hide his actions. And since DNS traffic is almost always allowed and not checked, it can operate freely in such an environment.
 Next, it tunnels other protocols, such as HTTP, through DNS.
Next, it tunnels other protocols, such as HTTP, through DNS.
 Then IP traffic and stolen information are transmitted.
Then IP traffic and stolen information are transmitted.
 After that, the stolen data is converted into a form that is easy to perceive.
After that, the stolen data is converted into a form that is easy to perceive.
 And, finally, the established tunnels are used to transmit malware.
And, finally, the established tunnels are used to transmit malware.
Today we will talk about DNS tunneling — one of the most dangerous techniques used by bad guys.
⏺A bit of history: DNS tunneling was first discovered back in 1998. Then Oscar Pearson made a discovery and revealed how DNS can be used for hidden attacks. And in 2004, at the Black Hat conference, it had already become a full-fledged tool for hackers. Since then, this method has been actively used to transfer data, hiding in regular traffic.
⏺How does DNS tunneling work? Let's imagine: there is a hypothetical attacker, and he disguises his not very legal actions as regular legitimate DNS traffic. Such a peculiar spy in a police officer's suit — he looks inconspicuous, but in fact he is up to something bad.
