- Joined
- Jan 8, 2019
- Messages
- 56,602
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,445
- Points
- 2,313
- Credits
- 32,540
6 Years of Service
76%
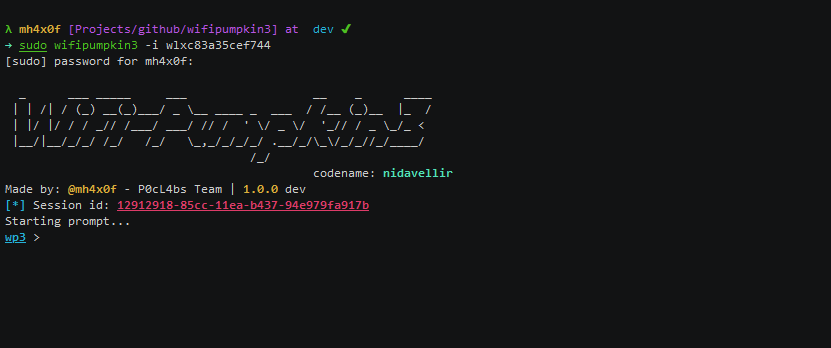
Wifipumpkin3
wifipumpkin3 is a powerful framework for rogue access point attack, written in Python, that allows and offers to security researchers, red teamers, and reverse engineers to mount a wireless network to conduct a man-in-the-middle attack.
Main Features
Rogue access point attack
Man-in-the-middle attack
Rogue Dns Server
Captive portal attack (captiveflask)
Intercept, inspect, modify and replay web traffic
WiFi networks scanning
DNS monitoring service
Credentials harvesting
Transparent Proxies
LLMNR, NBT-NS, and MDNS poisoner (Responder3)
and more!
Changelog v1.1.3R1
Added
improve: module extra_captiveflask to install without reinstall the tool
added: binary exec mode plugin options
added: debian package for build .deb
added: ignore venv from .gitignore
update: screenshot for version 1.1.3
update: readme information about version
Changed
changed: control user login and logout with python object
moved: captiveflask and pumpkinproxy to console script on setup.py installation
Deprecated
Removed
removed: responder3 depedencies now responder need to installed by default for use
removed: extensions for update from CLI ui
Fixed
fixed: set python3 version on binary sslstrip3 and captiveflask
fixed: set path default config files to /usr/share/wifipumpkin3
fixed: improves code with black format
fixed: Werkzeug depedency flask 2.0
To see this hidden content, you must like this content.