- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,456
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
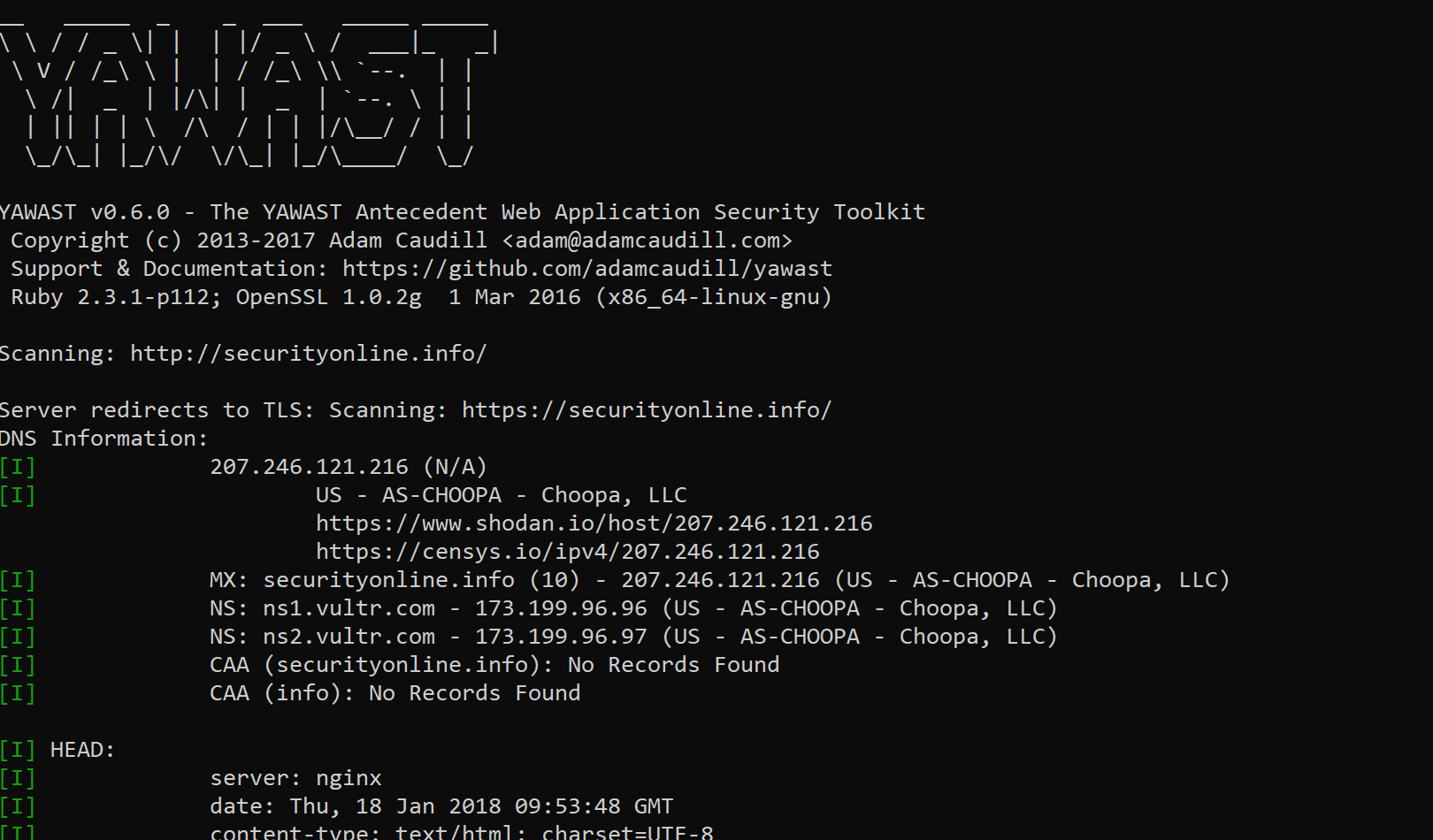
YAWAST is an application meant to simplify initial analysis and information gathering for penetration testers and security auditors. It performs basic checks in these categories:
- TLS/SSL – Versions and cipher suites supported; common issues.
- Information Disclosure – Checks for common information leaks.
- Presence of Files or Directories – Checks for files or directories that could indicate a security issue.
- Common Vulnerabilities
- Missing Security Headers
This is meant to provide an easy way to perform initial analysis and information discovery. It’s not a full testing suite, and it certainly isn’t Metasploit. The idea is to provide a quick way to perform initial data collection, which can then be used to better target further tests. It is especially useful when used in conjunction with Burp Suite (via the –proxy parameter).
Changelog v0.8.0b4
Various improvements
Like a Gem: pip3 install yawast
Via Docker: docker pull adamcaudill/yawast
It’s strongly recommended that you review the installation documentation, to make sure you have the proper dependencies.
Tests
The following tests are performed:
(Generic) Info Disclosure: X-Powered-By header present
(Generic) Info Disclosure: X-Pingback header present
(Generic) Info Disclosure: X-Backend-Server header present
(Generic) Info Disclosure: X-Runtime header present
(Generic) Info Disclosure: Via header present
(Generic) Info Disclosure: PROPFIND Enabled
(Generic) TRACE Enabled
(Generic) X-Frame-Options header not present
(Generic) X-Content-Type-Options header not present
(Generic) Content-Security-Policy header not present
(Generic) Public-Key-Pins header not present
(Generic) X-XSS-Protection disabled header present
(Generic) SSL: HSTS not enabled
(Generic) Source Control: Common source control directories present
(Generic) Presence of crossdomain.xml or clientaccesspolicy.xml
(Generic) Presence of sitemap.xml
(Generic) Presence of WS_FTP.LOG
(Generic) Presence of RELEASE-NOTES.txt
(Generic) Presence of readme.html
(Generic) Missing cookie flags (Secure, HttpOnly, and SameSite)
(Generic) Search for files (14,169) & common directories (21,332)
(Apache) Info Disclosure: Module listing enabled
(Apache) Info Disclosure: Server version
(Apache) Info Disclosure: OpenSSL module version
(Apache) Presence of /server-status
(Apache) Presence of /server-info
(Apache Tomcat) Presence of Tomcat Manager
(Apache Tomcat) Presence of Tomcat Host Manager
(Apache Tomcat) Tomcat Manager Weak Password
(Apache Tomcat) Tomcat Host Manager Weak Password
(Apache Tomcat) Tomcat version detection via invalid HTTP verb
(Apache Tomcat) Tomcat PUT RCE (CVE-2017-12617)
(Apache Struts) Sample files which may be vulnerable
(IIS) Info Disclosure: Server version
(ASP.NET) Info Disclosure: ASP.NET version
(ASP.NET) Info Disclosure: ASP.NET MVC version
(ASP.NET) Presence of Trace.axd
(ASP.NET) Presence of Elmah.axd
(ASP.NET) Debugging Enabled
(nginx) Info Disclosure: Server version
(PHP) Info Disclosure: PHP version
CMS Detection:
- Generic (Generator meta tag) [Real detection coming as soon as I get around to it…]
SSL Information:
- Certificate details
- Certificate chain
- Supported ciphers
- Maximum requests using 3DES in a single connection
- DNS CAA records
Checks for the following SSL issues are performed:
- Expired Certificate
- Self-Signed Certificate
- MD5 Signature
- SHA1 Signature
- RC4 Cipher Suites
- Weak (< 128 bit) Cipher Suites
- SWEET32
Certain DNS information is collected:
- IP Addresses
- IP Owner/Network (via api.iptoasn.com)
- TXT Records
- MX Records
- NS Records
- CAA Records (with CNAME chasing)
- Common Subdomains (2,354 subdomains) – optional, via --subdomains
- SRV Records – optional, via --srv
In addition to these tests, certain basic information is also displayed, such as IPs (and the PTR record for each IP), HTTP HEAD request, and others.
To see this hidden content, you must like this content.