- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,455
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
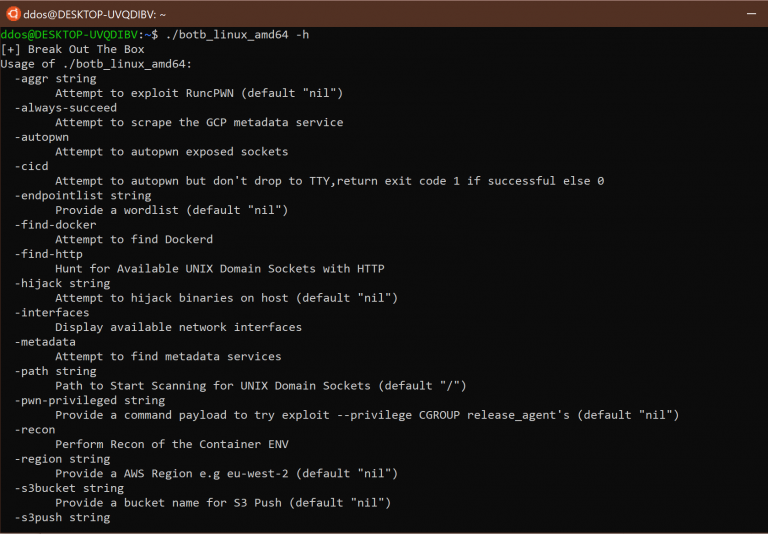
Break out the Box (BOtB)
BOtB is a container analysis and exploitation tool designed to be used by pentesters and engineers while also being CI/CD friendly with common CI/CD technologies.
What does it do?
BOtB is a CLI tool which allows you to:
Exploit common container vulnerabilities
Perform common container post-exploitation actions
Provide capability when certain tools or binaries are not available in the Container
Use BOtB’s capabilities with CI/CD technologies to test container deployments
Perform the above in either a manual or an automated approach
Current Capabilities
Find and Identify UNIX Domain Sockets
Identify UNIX domain sockets which support HTTP
Find and identify the Docker Daemon on UNIX domain sockets or on an interface
Analyze and identify sensitive strings in ENV and process in the ProcFS i.e /Proc/{pid}/Environ
Identify metadata services endpoints i.e http://169.254.169.254, http://metadata.google.internal/ and http://100.100.100.200/
Perform a container breakout via exposed Docker daemons
Perform a container breakout via CVE-2019-5736
Hijack host binaries with a custom payload
Perform actions in CI/CD mode and only return exit codes > 0
Scrape metadata info from GCP metadata endpoints
Push data to an S3 bucket
Break out of Privileged Containers
Force BOtB to always return a Exit Code of 0 (useful for non-blocking CI/CD)
Perform the above from the CLI arguments or from a YAML config file
Perform reverse DNS lookup
Identify Kubernetes Service Accounts secrets and attempt to use them
Changelog v1.8
In this release, the following is addressed:
Added @initree‘s Keyctl pwnage to extract entries from the Linux Kernel Keyring (https://www.antitree.com/2020/07/keyctl-unmask-going-florida-on-the-state-of-containerizing-linux-keyrings/)
Modified the new Keyctl code to be multi-threaded to make use of Go workers to speed up enumeration
To see this hidden content, you must like this content.