dEEpEst
☣☣ In The Depths ☣☣
Staff member
Administrator
Super Moderator
Hacker
Specter
Crawler
Shadow
- Joined
- Mar 29, 2018
- Messages
- 13,860
- Solutions
- 4
- Reputation
- 27
- Reaction score
- 45,546
- Points
- 1,813
- Credits
- 55,340
7 Years of Service
56%




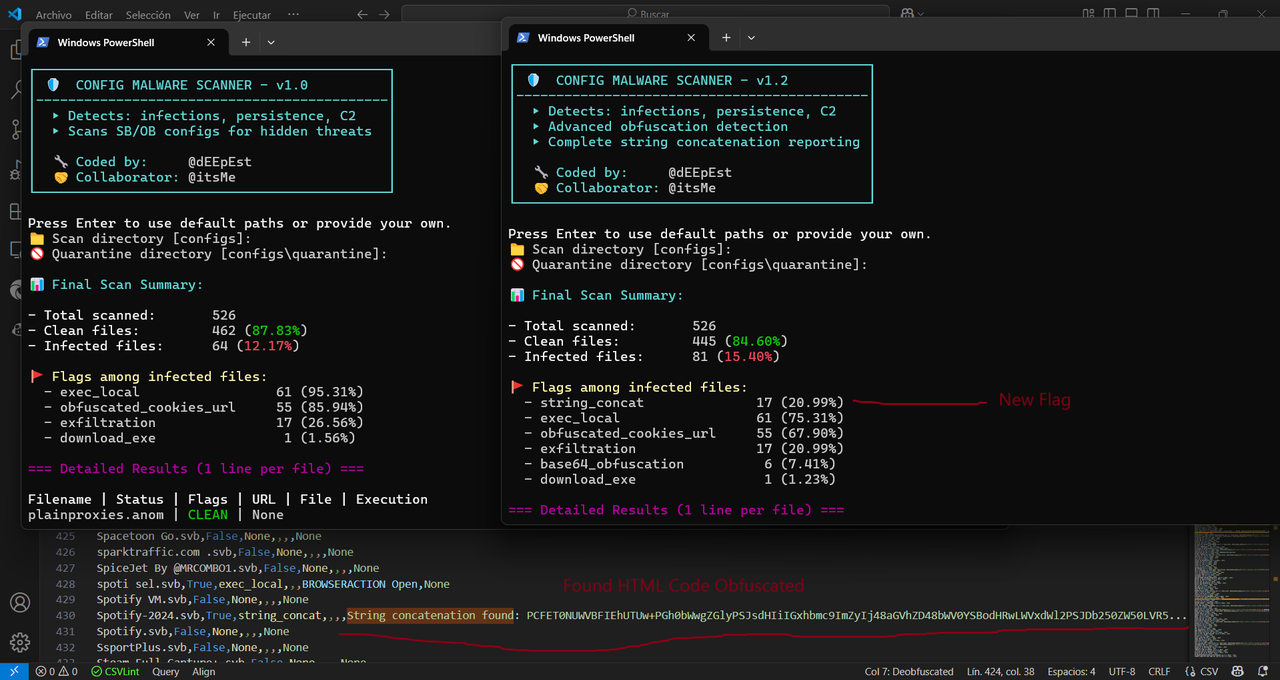
CONFIG MALWARE SCANNER v1.0 is a forensic analysis tool that scans SilverBullet, OpenBullet, and OpenBullet 2 config files for signs of malware infection. It detects hidden behaviors like execution, persistence, exfiltration, and malware download through obfuscated cookies.
- Malware downloads via direct .exe, .scr, .xe file links
- Silent execution using cmd, powershell, or ShellExecute
- Persistence mechanisms in registry or startup folders
- Exfiltration of data to remote services like Pastebin, GitHub, Discord, etc.
- Cookie-based obfuscation to build malware URLs and payload paths
- Dynamic URL chains assembled from multiple cookies
| Flag | Meaning | Main Trigger |
|---|---|---|
| download_exe | Detects direct executable file downloads | Line like -> FILE pointing to .exe, .xe, .scr |
| exec_local | Detects local command execution | Usage of BROWSERACTION Open, ShellExecute, cmd /c, start "", powershell -e |
| persistence | Detects persistence mechanisms | Entries like \Startup\, \Run\, reg add, schtasks |
| exfiltration | Detects data exfiltration to suspicious domains | URLs to pastebin, ghostbin, rentry, .php, IPs or Onion links |
| obfuscated_cookies_url | Detects use of cookies to hide full URLs | Cookies like "hst:", "hdp:", "htp:", "hht:" |
| obfuscated_file_write | Detects file writes using cookie logic | Lines like -> FILE "<COOKIES(...)>/file.exe" |
| suspicious_cookie_chain | Detects chained cookies forming suspicious paths | Multiple cookies generating URLs to .php, cdn.discordapp.com, raw.githubusercontent.com |
Code:
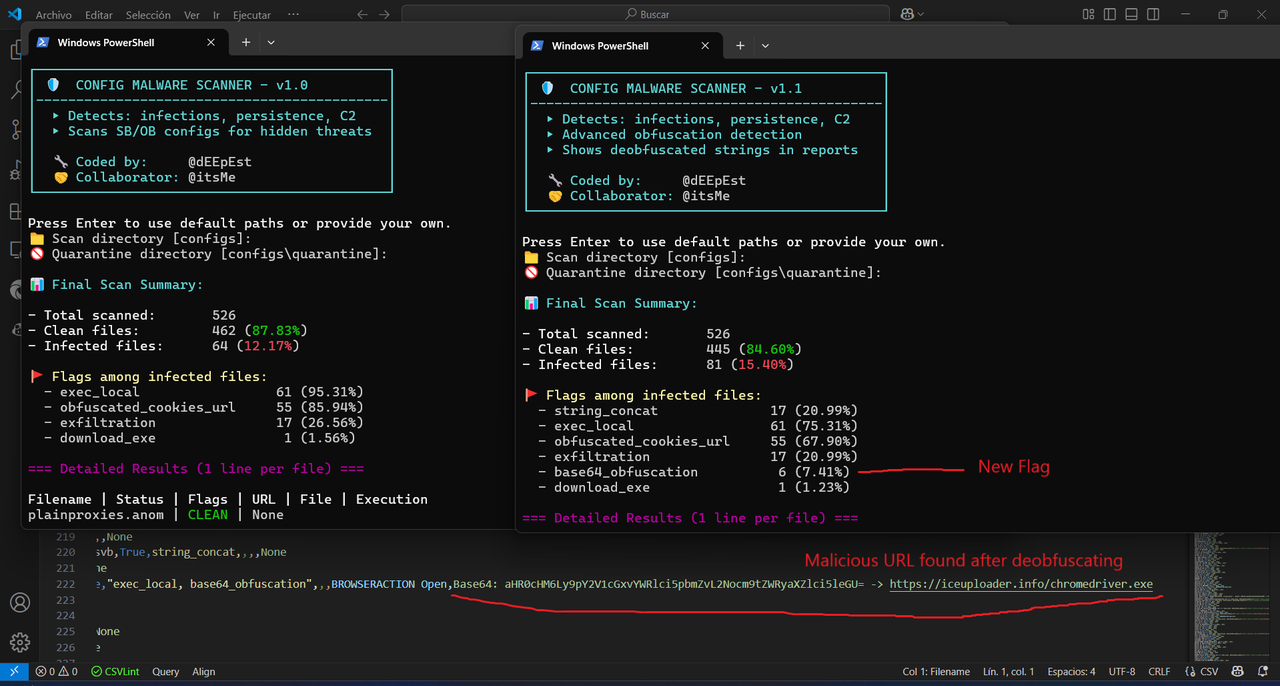
📊 Final Scan Summary:
Total scanned: 37
Clean files: 33 (89.19%)
Infected files: 4 (10.81%)
🚩 Flags among infected files:
download_exe 3 (75.00%)
exec_local 2 (50.00%)
exfiltration 2 (50.00%)
obfuscated_cookies_url 1 (25.00%)
=== Detailed Results (1 line per file) ===
stealer.config | INFECTED | download_exe, exec_local, exfiltration | URL: https://dropper.malware.xyz/bin/payload | File: temp32/payload.exe | Exec: cmd /c start
safe.config | CLEAN | None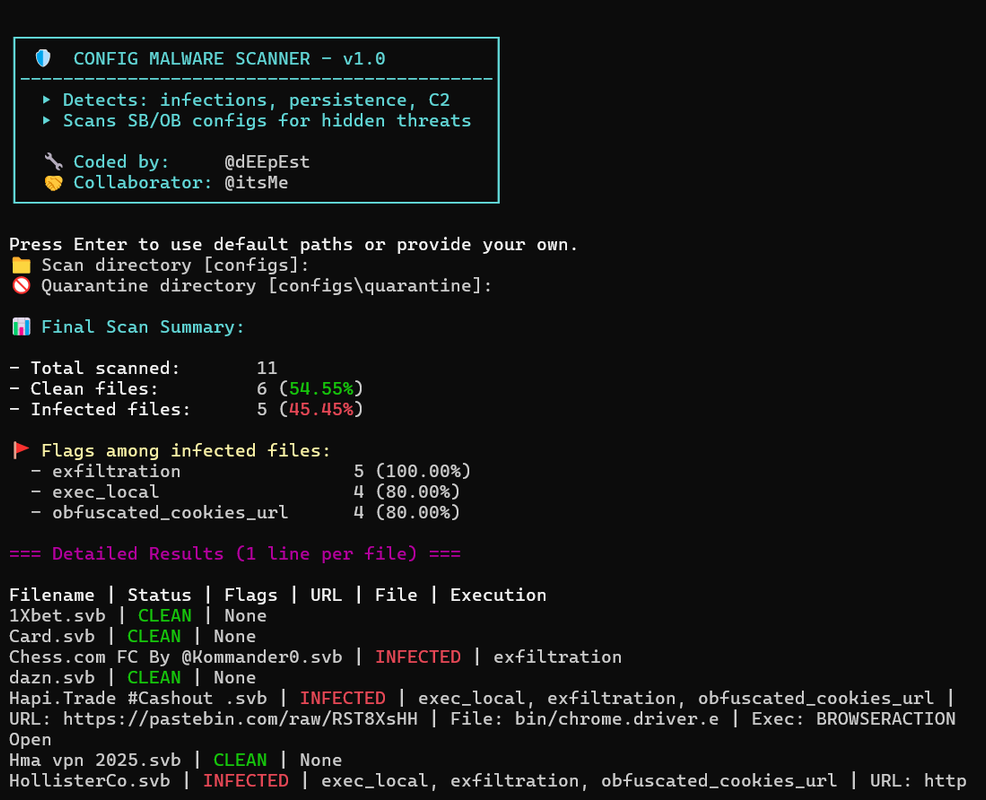
Bash:
Run ConfigMal.exe/quarantine/.infected_config_report.csv.I'm listening to your feedback and requests, they are welcome.
This tool is strictly for ethical research and analysis purposes only.
Do not use it on unauthorized or stolen configurations. Always respect legal boundaries.
Maybe
This link is hidden for visitors. Please Log in or register now.




NEW VERSION






Made for Hack Tools Dark Community
Last edited: