dEEpEst
☣☣ In The Depths ☣☣
Staff member
Administrator
Super Moderator
Hacker
Specter
Crawler
Shadow
- Joined
- Mar 29, 2018
- Messages
- 13,861
- Solutions
- 4
- Reputation
- 27
- Reaction score
- 45,549
- Points
- 1,813
- Credits
- 55,350
7 Years of Service
56%
Find XSS Vulnerabilities in Just 2 Minutes
Coffinxp Said: said:Hello everyone! Today I will show you my XSS finding technique in a very simple and effective way. This is my second article on Medium, I hope it will help you in bug hunting. Let’s get started!
The process is very simple and efficient. The first step is to copy the target website URL. Now that we know the target, the next step will be to execute a very simple, yet powerful one-liner command that streamlines the testing process. Here’s how it works
Code:
echo example.com | gau | gf xss | uro | Gxss | kxss | tee xss_output.txtBut before we go any further, let me explain these commands step by step:
- GAU: fetches old URLs from passive sources like WaybackURLs, AlienVault, Common Crawl, and URLscan.
- GF pattern: filters for URLs with parameters often vulnerable to XSS
- URO: removes duplicate URLs, so only unique entries remain.
- Gxss: checks for URLs with parameters which reflect in the response.
- Kxss: identifies URLs with unfiltered special characters, useful for XSS execution
- tee: saves output to a file…
Hit enter and wait a second. As you can see, we now have all the URLs with the reflected parameters with unfiltered characters that are used in xss payloads.
Refining and Validating Results
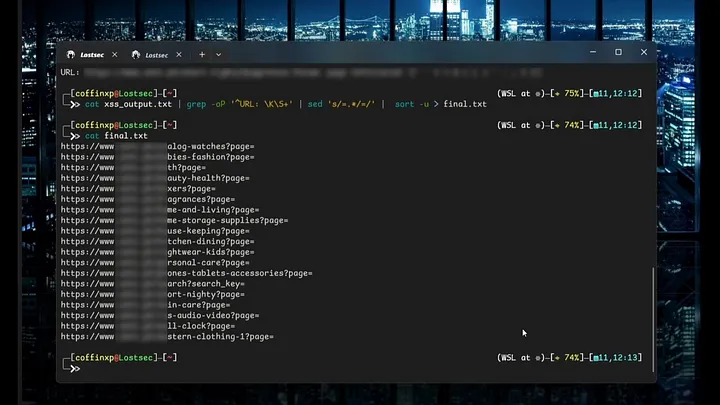
Now open the saved output. You can see the results, although they include some noisy entries. to improve this, let’s filter out everything we don’t need. Enter below command which cleans up the output, it will show URLs with XSS-vulnerable parameters
Code:
cat xss_output.txt | grep -oP '^URL: \K\S+' | sed 's/=.*/=/' | sort -u > final.txt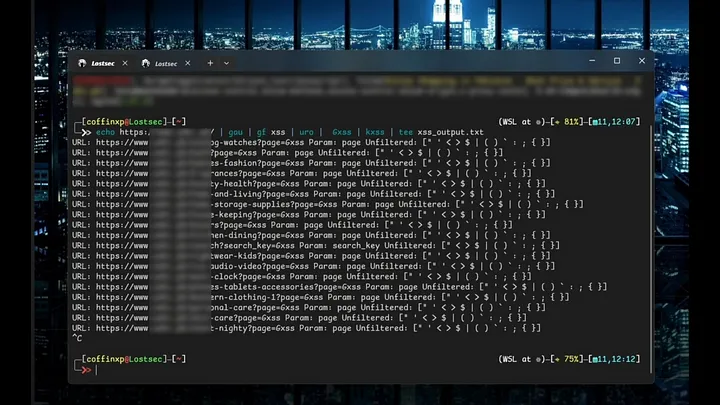
Final exploitation with our Loxs tool
So, let’s send these result to our Loxs tool folder. Now run the Loxs tool, select option 4 for xss, enter the results file final.txt , provide the path to the payload file and press Enter.

Perfect! As you can see it shows all XSS vulnerable URLs on the terminal copy it now and paste it into the browser to see the XSS popup. Or you can wait to finish the full scan so it will generate a clean html report with all the details then you can open that one by one to see xss popup’s
you can download our Loxs tool from my github repo:This link is hidden for visitors. Please Log in or register now.
You can also watch this video where I showed the complete practicle of this method:Conclusion
Byfollowing this structured approach, you can effectively identify xss vulnerability enhancing your bug-hunting efforts. also i provided all the waf Bypass payload list with the tool so it will help you to bypass waf. I hope you found this guide helpful and it makes your bug-hunting journey easier and more efficient! If you have any questions or feedback, feel free to leave a comment below. have a nice day“The best hackers aren’t just coders; they’re thinkers, problem solvers, and explorers.” — Coffinxp
Last edited: