13 Years of Service
100%
Please note, if you want to make a deal with this user, that it is blocked.
Several companies confirmed so far to have fallen victim to GoldenEye/Petya ransomware: Chernobyl’s radiation monitoring system, DLA Piper law firm, pharma company Merck, a number of banks, an airport, the Kiev metro, Danish shipping and energy company Maersk, British advertiser WPP and Russian oil industry company Rosnoft. The attacks were widespread in Ukraine, affecting Ukrenergo, the state power distributor, and several of the country’s banks.
GoldenEye/Petya operators have already received 13 payments in almost two hours. That is $3.5K USD worth in digital currency.
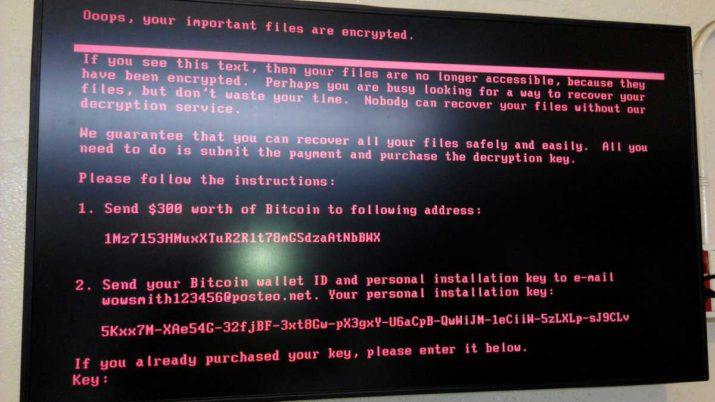
Bitdefender has identified a massive ransomware campaign that is currently unfolding worldwide. Preliminary information shows that the malware sample responsible for the infection is an almost identical clone of the GoldenEye ransomware family. At the time of writing this there is no information about propagation vector but we presume it to be carried by a wormable component.
Unlike most ramsonware, the new GoldenEye variant has two layers of encryption: one that individually encrypts target files on the computer and another one that encrypts NTFS structures. This approach prevents victims computers from being booted up in a live OS environment and retreiving stored information or samples.
Just like Petya, GoldenEye encrypts the the entire hard disk drive and denies the user access to the computer. However, unlike Petya, there is no workaround to help victims retrieve the decryption keys from the computer.
Additionally, after the encryption process is complete, the ransomware has a specialized routine that forcefully crashes the computer to trigger a reboot that renders the computer unusable until the $300 ransom is paid.
Source
To see this hidden content, you must like this content.
