- Joined
- Jan 8, 2019
- Messages
- 56,602
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,445
- Points
- 2,313
- Credits
- 32,540
6 Years of Service
76%
STEALER FUNCTIONS:
1. Bypassing Chrome cookie V20 Protection
2. Chromium and Gecko browsers (cookies, passwords, card, forms)
3. Popular cryptocurrencies (Exodus, Monero, Zcash, Jax, Electrum, DashCore, MetaMask and so on)
4. FTP, Steam, popular VPN services
5. Telegram session, Discord tokens
6. Screenshot
7. Grabber (files from the victim's PC)
INSTRUCTION:
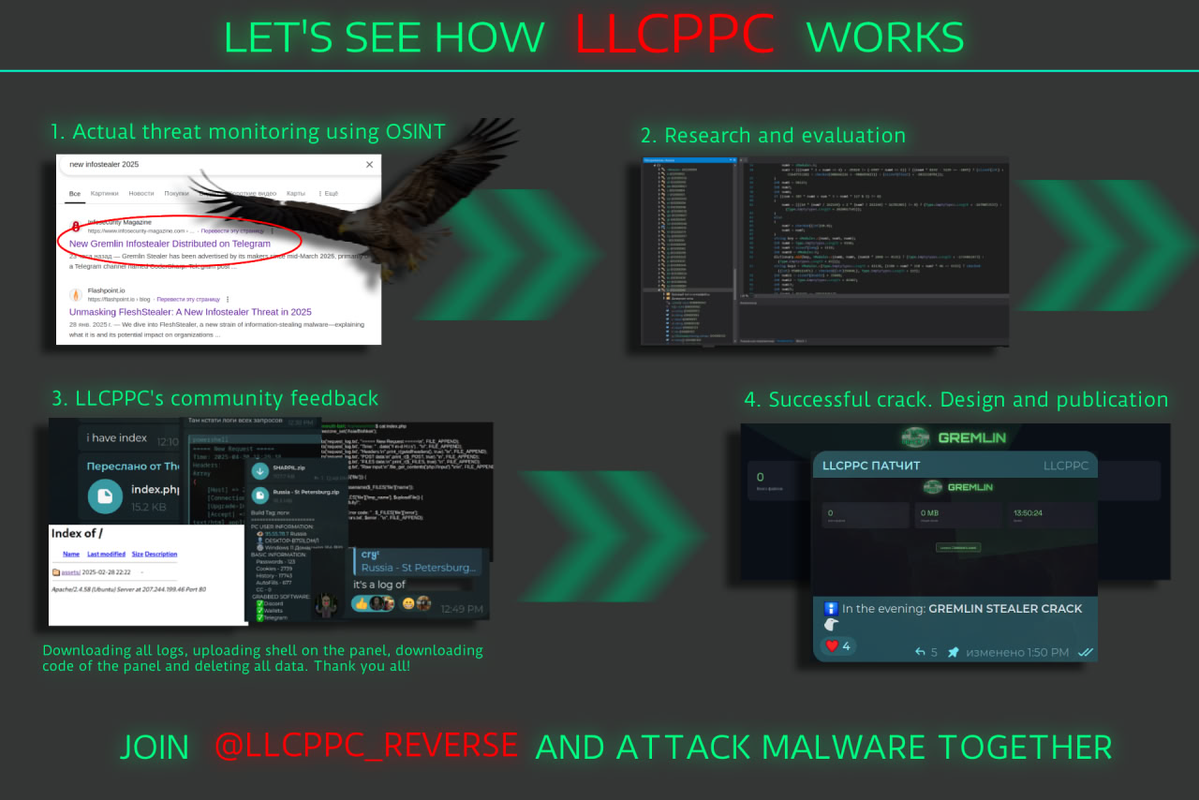
1. Change password inside "i.php"
2. Upload "i.php" on the server, create "uploads", create .htaccess folder and restrict raw access to the "/uploads" folder
3. Run "Gremlin_Builder.exe" and enter URL to the "i.php". Example:
This link is hidden for visitors. Please Log in or register now.
4. Press "GENERATE BUILD GREMLIN STEALER" button. Your build will generated under "Gremlin_build.exe.llcppc" file name (delete .llcppc)
5. Success!
WARNING: Panel is vulnerable to RCE attacks! (anyone can upload .php shell to your panel, to fix that you need add extension checks inside "i.php")
File loaded correctly.
Sending file to server...
Completed analysis, generating link ...
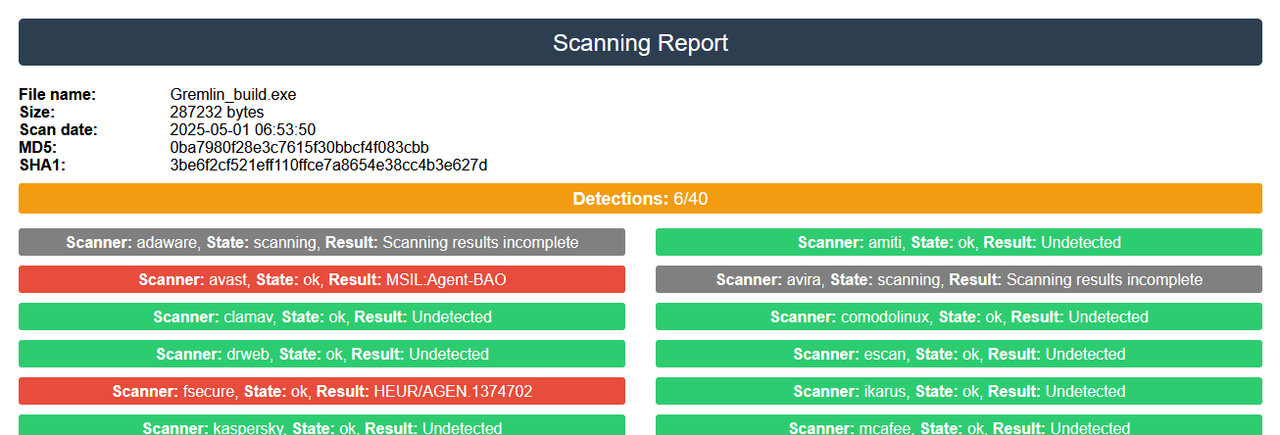
Sending file to server...
Completed analysis, generating link ...

News

Gremlin Stealer: Emerging Infostealer Targets Cryptocurrency and VPN Credentials
Unit 42 recently identified a new infostealer named Gremlin Stealer, actively marketed on underground forums via Telegram. Written in C#, this malware is capable of exfiltrating sensitive data such as credit card details, browser cookies, cryptocurrency wallets, and VPN credentials. Distributed through a dedicated Telegram channel, Gremlin Stealer is in active development and poses a significant threat to user privacy and data security.
Key features of Gremlin Stealer include its ability to bypass Chrome's cookie v20 protection, targeting popular browsers, FTP, Steam, VPNs, and messaging platforms like Telegram and Discord for data theft. It collects this data into ZIP archives and uploads it to a specific server. Palo Alto Networks provides robust protection against threats like Gremlin Stealer through solutions like Advanced WildFire, Advanced Threat Prevention, and Cortex XDR.
• Uses Telegram for distribution
• Targets browsers to steal cookies and passwords
• Bypasses Chrome's cookie v20 protection
• Collects cryptocurrency wallet information
• Steals VPN credentials from popular software
What stood out to me was Gremlin Stealer's ability to bypass Chrome's cookie protection, a technique threat actors are increasingly employing.
Curious how other teams are handling the defense against sophisticated information stealers like this one.
More details here:
This link is hidden for visitors. Please Log in or register now.
Last edited by a moderator: