- Joined
- Jan 8, 2019
- Messages
- 56,618
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,455
- Points
- 2,313
- Credits
- 32,700
6 Years of Service
76%
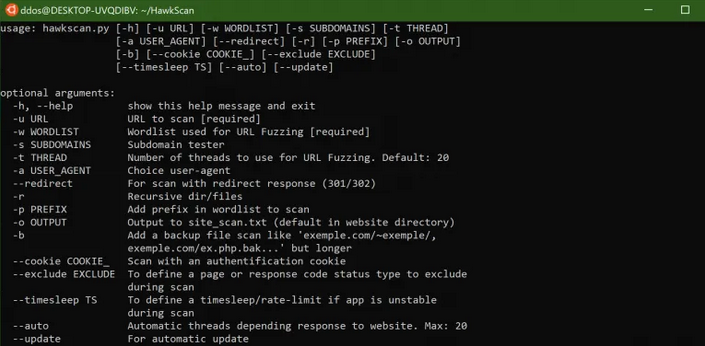
Security Tool for Reconnaissance and Information Gathering on a website. (python 2.x & 3.x)
This script uses “WafW00f” to detect the WAF in the first step.
This script uses “Sublist3r” to scan subdomains.
This script uses “waybacktool” to check in the waybackmachine.
Features
URL fuzzing and dir/file detection
Test backup/old file on all the files found (index.php.bak, index.php~ …)
Check header information
Check DNS information
Check whois information
User-agent random or personal
Extract files
Keep a trace of the scan
Check @mail in the website and check if @mails leaked
CMS detection + version and vulns
Subdomain Checker
Backup system (if the script stopped, it take again in the same place)
WAF detection
Add personal prefix
Auto-update script
Auto or personal output of scan (scan.txt)
Check Github
Recursive dir/file
Scan with an authentication cookie
Option –profil to pass profil page during the scan
HTML report
Work it with py2 and py3
Add option rate-limit if the app is unstable (–timesleep)
Check-in waybackmachine
Response error to WAF
Check if DataBase firebaseio exists and is accessible
Automatic threads depending on the response to a website (and reconfig if WAF is detected too many times). Max: 30
Search S3 buckets in the source code page
Testing bypass of waf if detected
Testing if it’s possible scanning with “localhost” host
Changelog v2.1
New: Option -nfs (not first step) to pass the first recon steps
Fixed: Any bug with the download file and bypass forbidden when differents options
New: Google cse search (buckets…)
New: Add LICENSE & PyPI version and stats
To see this hidden content, you must like this content.