- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,455
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
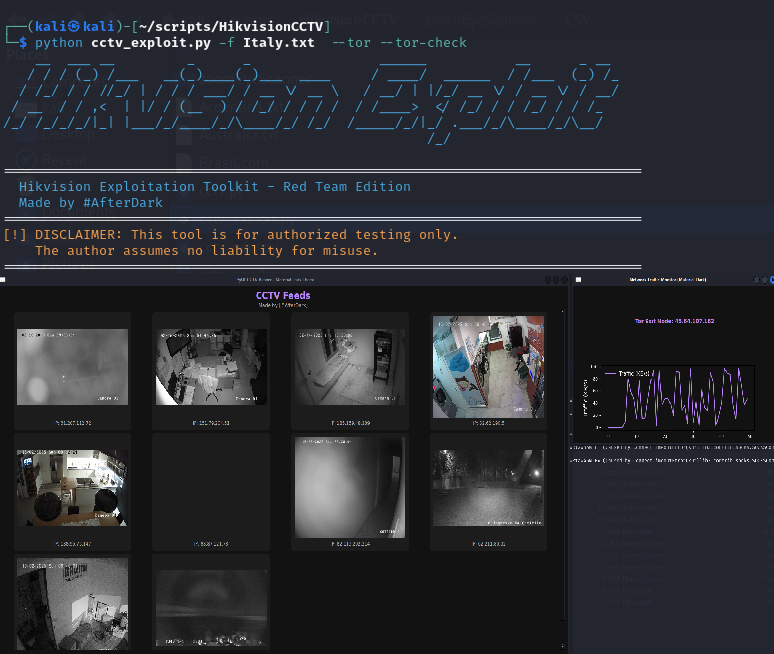
A Python-based Hikvision exploitation and CCTV viewer toolkit. Features live feed previews, snapshot analysis (with zoom and pan), Tor integration, and an ASCII banner reminiscent of the original scanner.
About
Hikvision-AfterDark is a comprehensive toolkit for CCTV reconnaissance, live monitoring, and vulnerability assessment.
It includes multiple tools designed to locate, analyze, and exploit exposed Hikvision cameras across the internet.
This toolkit is ideal for:
Red Teaming – Identify and exploit exposed CCTV cameras in real time.
OSINT & Reconnaissance – Gather intelligence on unsecured surveillance systems.
Vulnerability Research – Test for known security flaws, including CVE-2021-36260.
For ethical use only! Unauthorized access to devices you do not own is illegal.
Features
Live Feed Previews – See multiple Hikvision cameras in real-time.
Snapshot Analysis – Click a feed to open a zoomable, pannable snapshot window for detailed inspection.
Tor Integration – Optionally route traffic via Tor (--tor, --tor-check).
IP Display – Shows each camera's resolved IP.
CVE-2021-36260 Exploit – Identifies vulnerable Hikvision devices.
Shodan & ZoomEye Support – Scan for public CCTV cameras worldwide.
To see this hidden content, you must like this content.