This guy is amazing!!! I thought he was hilarious. We all need to learn this and take down all the scamming kids. You can follow him on his X account.
 How we destroyed a turkish card operation, a thread:
How we destroyed a turkish card operation, a thread:

This morning I was casually scrolling through Telegram when I stumbled across a link dropping a "suspicious file"...

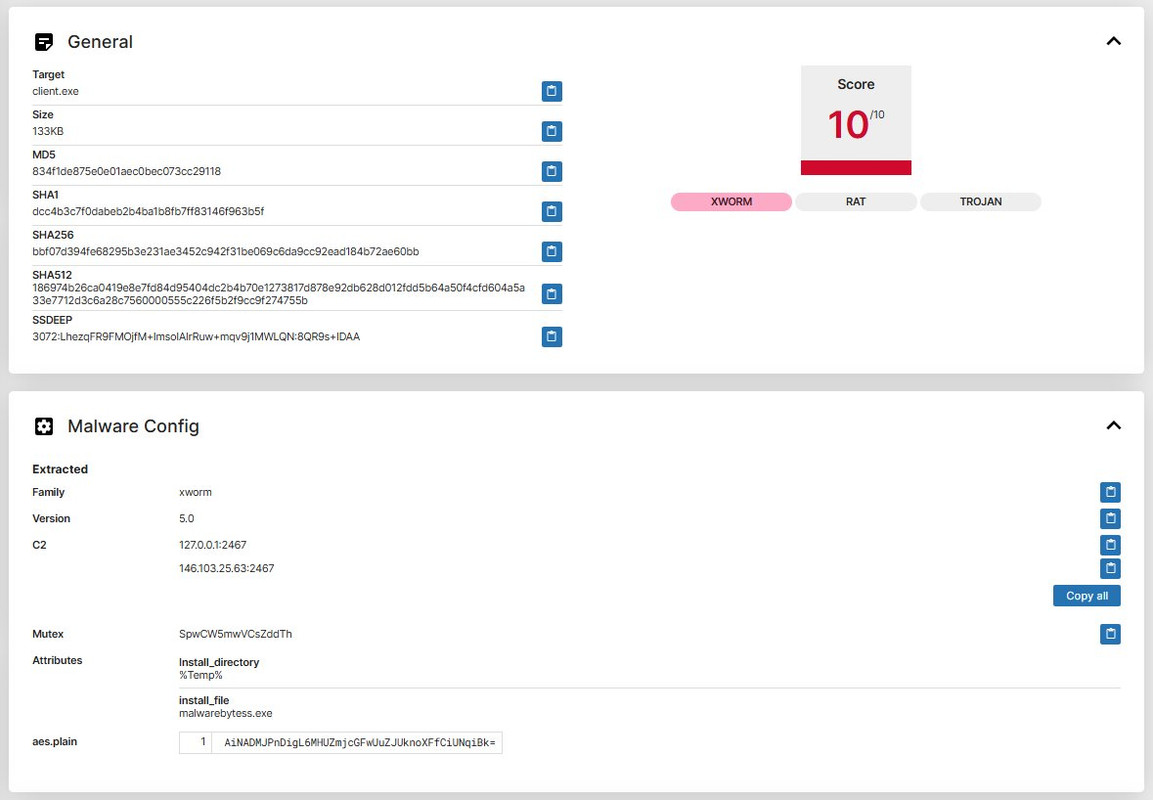
Out of curiosity, I grabbed the file and sent it through triage (
|

Screen 1) for analysis. A few minutes later, the verdict came back: #XWorm.

I pinged my guy @Swezy_1337 — time to have some fun.
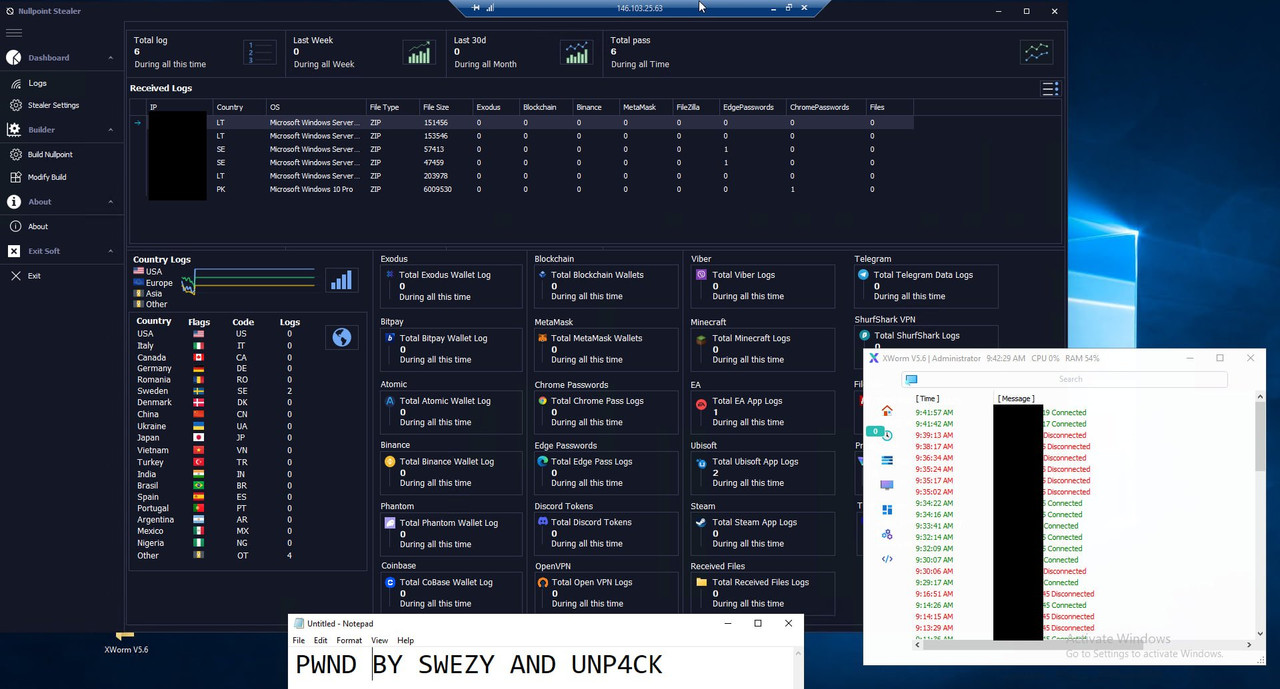
➡ For some context, Swezy developped a tool to RCE the malwares C2, so we can access the RDP pretty easily... (

Screen 2)

So we started reversing the binary and quickly noticed a shitty implementation in the C2 communication (146[.]103[.]25[.]63).

With this, we could easily use the tool from Swezy, and of course, get access to the RDP, thanks to some black magic


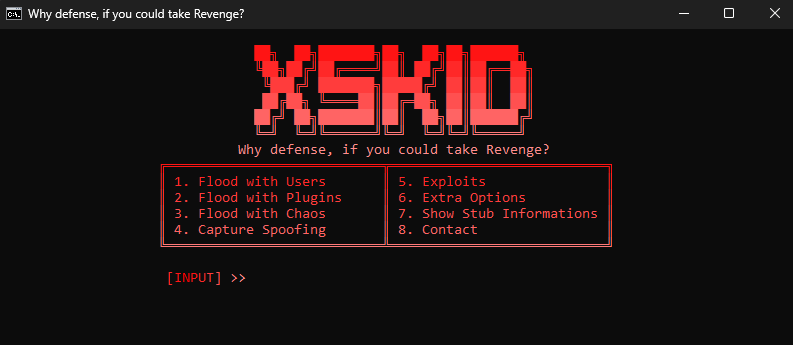
Once inside the VPS, we discovered what this "hacker" was up to. The dude was targeting hotel management systems, using the RAT to steal credit card details, booking records, and personal info from customers, for this, he use 2 tool (

Screen 3):

"#Nullpoint", a free Opensource #infostealer (available on github)

and of course, XWorm V5.6, cracked...

Logs were full of stolen data (from stealers), some screenshots, clipboard dumps and databases dump. All routed back to a little CNC hosted on a Windows RDP in

Lithuania by Space Hosting (AS15440).

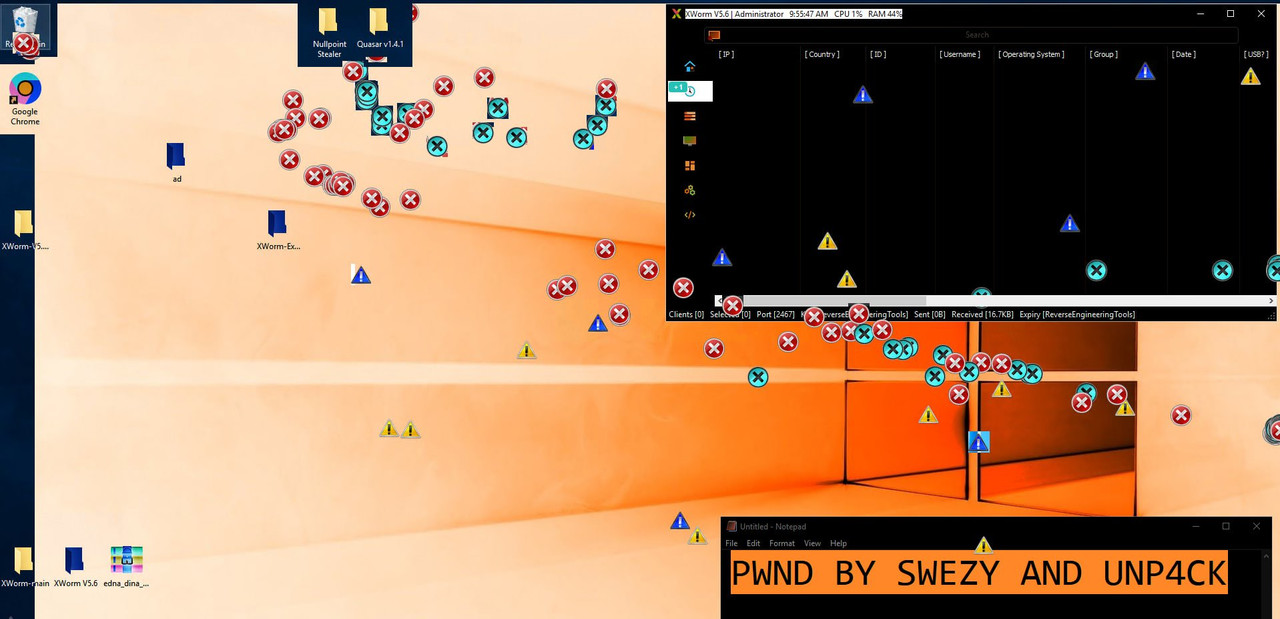
We wiped everything (and have a bit of fun with it). (

Screen 4)
➡All the stolen victim data? Gone (womp womp).
➡RAT C2? Deleted.
➡Logs? Burned.
➡We even left a nice little note (you will see in screenshot below ahah).
➡And of course, we completely nuked the server — RIP the boot sector

⏲ An hours later, the "hacker" — a underage Turkish skid — started DMing us on Telegram, panicking. He had no clue what happened. We had his full name, email, server IPs, Telegram handle...

This idiot, in a way to appear strong and powerful, talked a little too much, and told us more about his rat method. In fact, he's having fun sending PDFs containing the malware via WhatsApp to quickly and easily infect hotels, of which we've only detected 2 so far:
-

Black Lotus Hotel İzmir
-

Luxus Grand Hotel

You don’t get to rat hotels and harvest cards while hiding behind your little obfuscated stub and think you’re safe.
➡You play dirty, you get reversed, pwned, and humiliated.


It was fun.


cc/@abuse_ch @banthisguy9349 @redrabytes @swezy_1337
 How we destroyed a turkish card operation, a thread:
How we destroyed a turkish card operation, a thread: