- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,456
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
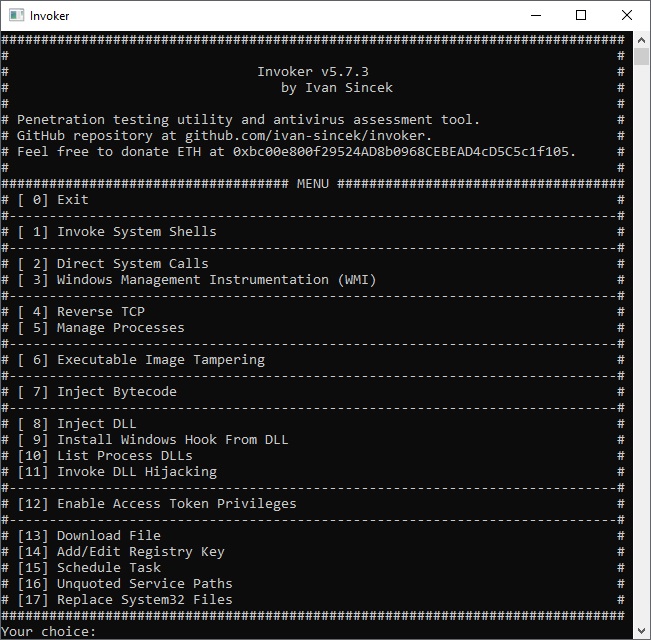
Penetration testing utility.
The goal is to use this tool when access to some Windows OS features through GUI is restricted.
Capabilities:
invoke the Command Prompt and PowerShell,
use Windows Management Instrumentation (WMI),
connect to a remote host,
run a new process,
terminate a running process,
dump a process memory,
inject a bytecode into a running process,
inject a DLL into a running process,
list DLLs of a running process,
install a hook procedure,
enable access token privileges,
duplicate the access token of a running process,
download a file,
add a registry key,
schedule a task,
list unquoted service paths and restart a running service,
replace System32 files.
Changelog v3.5.1
Added process hollowing. File read and write update.
Added bytecode and DLL injection through an asynchronous procedure call (APC).
To see this hidden content, you must like this content.