- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,456
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
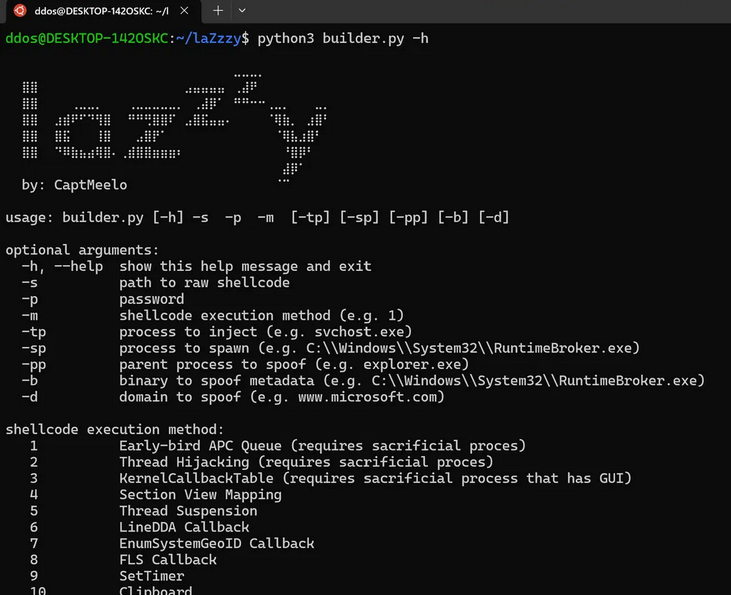
laZzzy is a shellcode loader that demonstrates different execution techniques commonly employed by malware. laZzzy was developed using different open-source header-only libraries.
Features
Direct syscalls and native (Nt*) functions (not all functions but most)
Import Address Table (IAT) evasion
Encrypted payload (XOR and AES)
Randomly generated key
Automatic padding (if necessary) of payload with NOPS (\x90)
Byte-by-byte in-memory decryption of the payload
XOR-encrypted strings
PPID spoofing
Blocking of non-Microsoft-signed DLLs
(Optional) Cloning of PE icon and attributes
(Optional) Code signing with spoofed cert
To see this hidden content, you must like this content.