dEEpEst
☣☣ In The Depths ☣☣
Staff member
Administrator
Super Moderator
Hacker
Specter
Crawler
Shadow
- Joined
- Mar 29, 2018
- Messages
- 13,861
- Solutions
- 4
- Reputation
- 27
- Reaction score
- 45,549
- Points
- 1,813
- Credits
- 55,350
7 Years of Service
56%
What is Cyber Threat Hunting?
Cyber threat hunting is proactively and systematically searching for signs of potential cyber threats within an organization’s network or systems. This can be done through manual and automated techniques, such as analyzing log data, conducting network scans, and using threat intelligence feeds. Cyber threat hunting aims to identify potential threats that may have evaded traditional security controls, such as firewalls or intrusion detection systems. By detecting and responding to these threats early, organizations can reduce their risk of being impacted by a cyber attack and maintain the security and availability of their systems and networks.Threat hunting can be defined as a practice designed to help you find adversaries hiding in your network before they can execute an attack or fulfill their goals. Unlike most security strategies, threat hunting is a proactive technique that combines the data and capabilities of an
This link is hidden for visitors. Please Log in or register now.
Threat hunting is quite a different activity from either
This link is hidden for visitors. Please Log in or register now.
Threat hunting also differs from
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
What Do You Need to Start Threat Hunting?
As we’ve seen, the cyber threat hunting process is all about aggressively seeking out hidden IOCs and covert behavior by assuming a breach has occurred and then searching for anomalous activity. To do that, security analysts must separate the unusual from the usual, filtering out the noise of everyday network traffic in search of as yet-unknown activity.Doing that effectively begins with comprehensive visibility into your network and rich data from your endpoints. Device telemetry should include things like encrypted traffic,
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
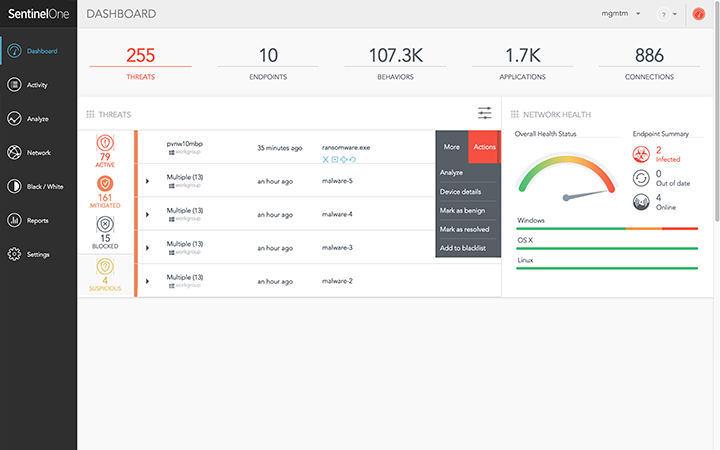
Features that can
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
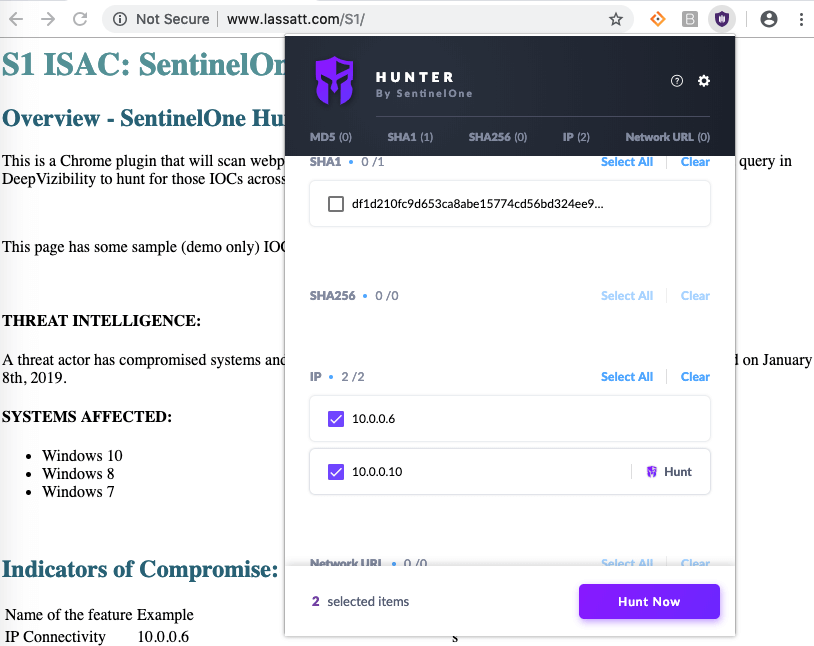
A threat-hunting program requires proper reporting tools to provide analysts with quality data, but it also presupposes that they have full confidence in the
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
Another vital security tool for analysts is good
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
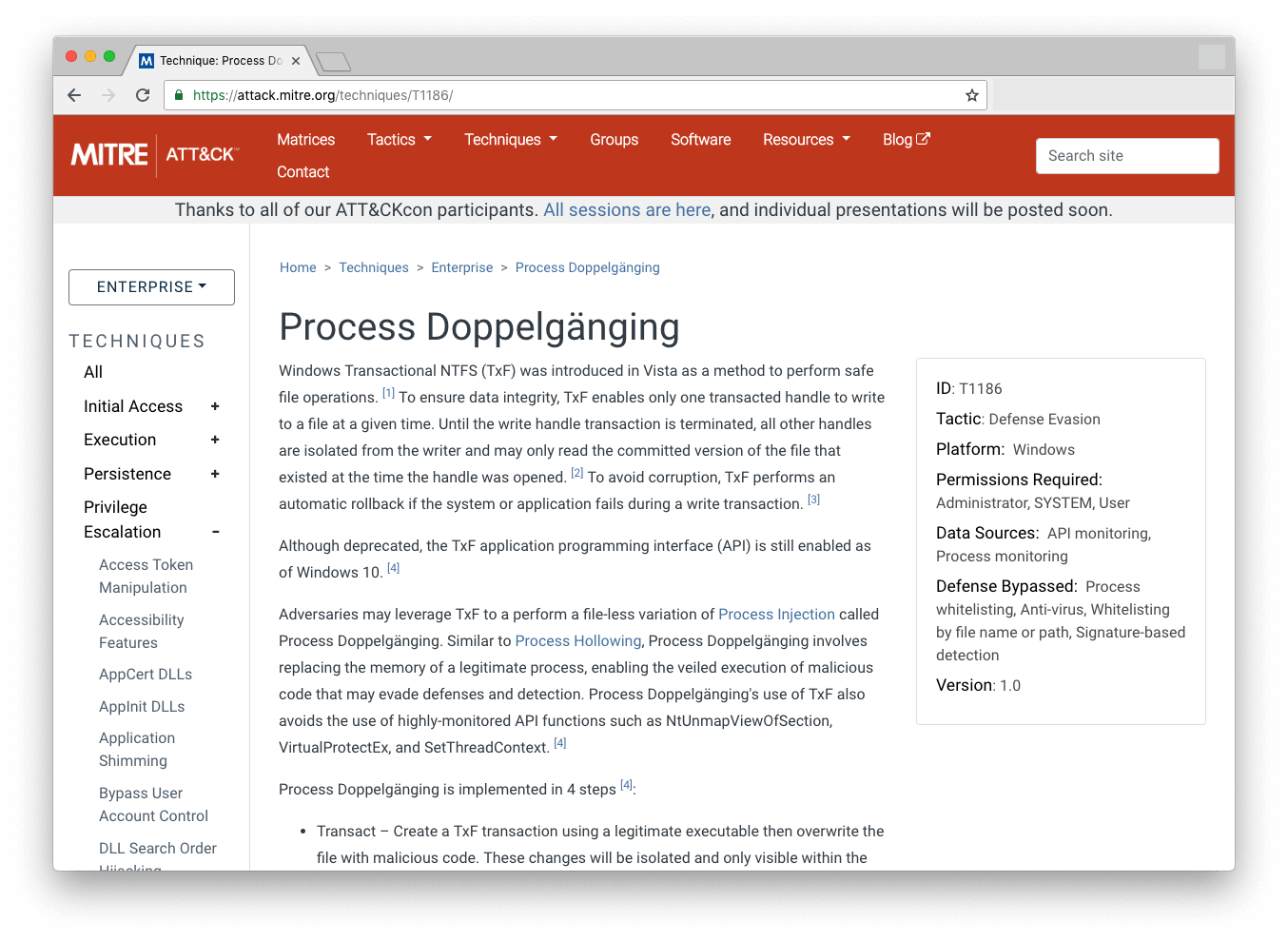
How Do You Know What to Look For?
Using
This link is hidden for visitors. Please Log in or register now.
Threat hunters need a solid understanding of the organization’s profile, business activities that could attract threat actors (such as hiring new staff or acquiring new assets, companies, etc), and baseline usage.
Attackers will often want to blend in with ordinary users and try to acquire user credentials such as from a
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
“Which users have accessed location XYZ for the first time in the last n days?”
Advanced threat-hunting techniques will try to automate as many tasks as possible using statistical analyses and machine learning. Monitoring user behavior and comparing that behavior against itself to search for anomalies, for example, is far more effective than running individual queries, though both techniques are likely to be required in practice. Both are made easier if you have tools like SentinelOne that have a rich set of native APIs enabling full integration across your security software stack.
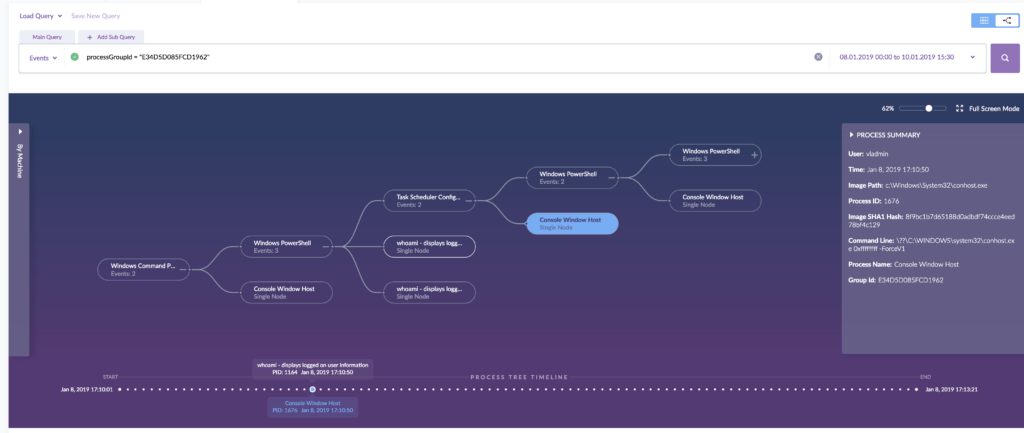
How Often Should You Threat Hunt?
Some businesses only hunt for new threats on an ad hoc basis. This might be triggered when a certain event (e.g., an access attempt on a particularly sensitive service or file location) or staff has free time from other duties. While ad hoc hunting allows organizations with restricted staff and budgets to still engage in this extra layer of defense, it has the drawback of only allowing minimal hunts for a limited set of behaviors and is the least effective way to employ the strategy.Scheduled threat hunting, where time is dedicated for staff to conduct hunts at regular intervals, is an improvement and can allow organizations to prioritize searches at different times and improve efficiency. However, scheduled threat hunting has the drawback of offering a certain
This link is hidden for visitors. Please Log in or register now.
Ideally, organizations with sufficient staff and budget should engage in continuous, real-time threat hunting in which the network and endpoints are proactively engaged to uncover attacks on the network as part of a sustained effort.
Who Should Conduct Your Threat Hunting?
It’s probably clear by now that threat hunting is a specialist task. It requires a security analyst who can use various tools, understand and analyze the risks your organization faces, and is versed in the methods and tools used by advanced attackers.While hiring in-house threat hunters can be a great way to go, organizations need to have the budget for it and access to people with the relevant skills. For many enterprises, a more realistic approach can be to engage threat hunting services from
This link is hidden for visitors. Please Log in or register now.
Conclusion
Threat hunting allows you to get out in front of the latest threats by proactively hunting for malicious activity. Advanced solutions like behavioral AI will stop most cyberattacks in their tracks and are prerequisites to providing the visibility threat hunting requires, but malicious actors are always innovating and looking for ways around enterprise network security. Organizations need to be vigilant to prevent vectors such as
This link is hidden for visitors. Please Log in or register now.
More info:
This link is hidden for visitors. Please Log in or register now.