13 Years of Service
57%
Source code of Phoenix Exploit Kit Version 2.3
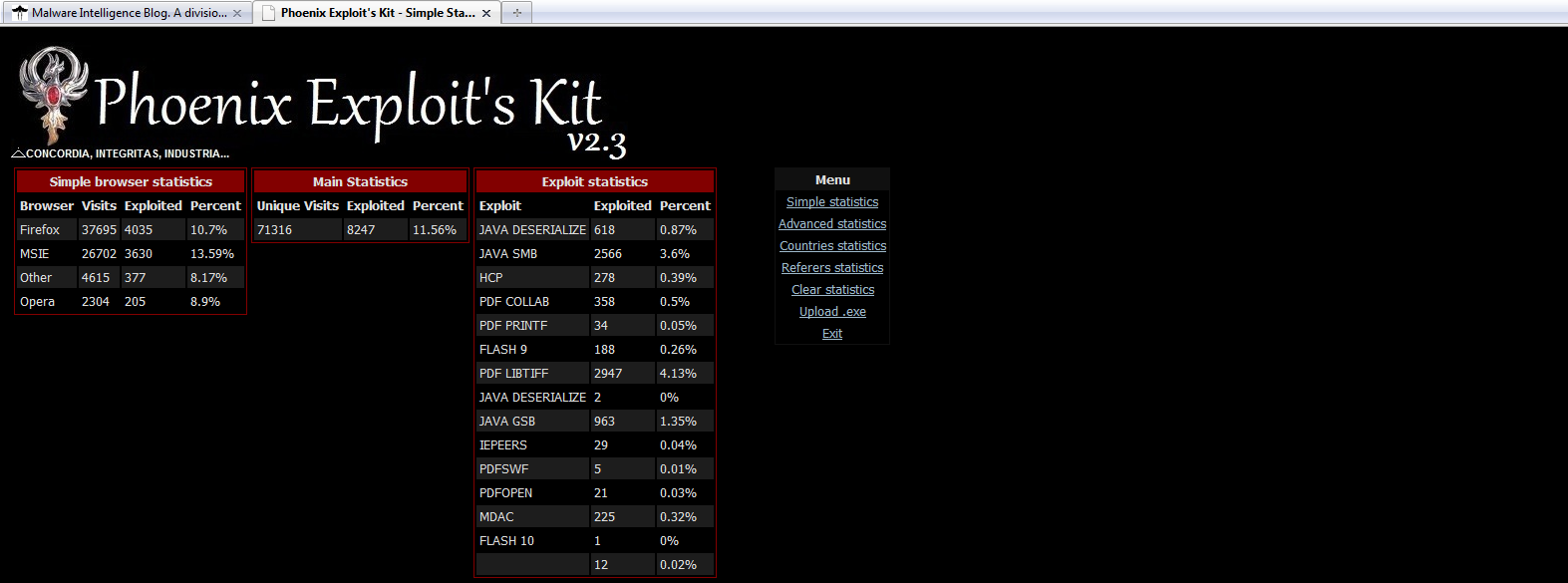
PEK (Phoenix Exploit’s Kit) has become one of the
most used by those who flood the Internet every day
with different types of malicious code. The sale of this
version began in July 2010 at a cost of $2200.
The default exploits for this version are:
Adobe Reader newPlayer CVE-2009-4324
Adobe Reader LibTiff CVE-2010-0188
Adobe PDF SWF CVE-2010-1297
Adobe Reader/Foxit Reader PDF OPEN CVE-
2009-0836
Java HsbParser.getSoundBank (GSB) CVE-2009-
3867
Java Runtime Environment (JRE) CVE-2008-5353
Java SMB CVE-2010-0746
IE iepeers CVE-2010-0806
Windows Help Center (HCP) CVE-2010-1885
IE SnapShot Viewer ActiveX CVE-2008-2463
One of the most important changes in this release was
PDF libtiff support the use of bypass ASLR, DEP more
for PDF file reader Adobe Reader on your version 8.0-
9.3.0 for Windows Vista and Windows7.
Generally we have seen the spread executable binary
as a variant of the trojan generated with the private
constructor SpyEye: exe.exe (014678ec0f5e2b92d7f0
89a20ffe77fa).
Once executed, the malware establishes a
connection to the domain clandestine fordkaksosat.info
(193.105.207.45 – AS50793 ALFAHOSTNET) from
which you download and run malware automatically a
rogue type.
This malware is also promoted through a website
from which, using social engineering, simulates the sale
of an antivirus program through a file called PCDefend
erSilentSetup.msi (ecff63c1f983858dfd7fb926738cb47
8), which represents the so-called rogue PC Defender
Antivirus. The cost is typically USD 59.95.
PEK has been around since mid-2007.

PEK (Phoenix Exploit’s Kit) has become one of the
most used by those who flood the Internet every day
with different types of malicious code. The sale of this
version began in July 2010 at a cost of $2200.
The default exploits for this version are:
Adobe Reader newPlayer CVE-2009-4324
Adobe Reader LibTiff CVE-2010-0188
Adobe PDF SWF CVE-2010-1297
Adobe Reader/Foxit Reader PDF OPEN CVE-
2009-0836
Java HsbParser.getSoundBank (GSB) CVE-2009-
3867
Java Runtime Environment (JRE) CVE-2008-5353
Java SMB CVE-2010-0746
IE iepeers CVE-2010-0806
Windows Help Center (HCP) CVE-2010-1885
IE SnapShot Viewer ActiveX CVE-2008-2463
One of the most important changes in this release was
PDF libtiff support the use of bypass ASLR, DEP more
for PDF file reader Adobe Reader on your version 8.0-
9.3.0 for Windows Vista and Windows7.
Generally we have seen the spread executable binary
as a variant of the trojan generated with the private
constructor SpyEye: exe.exe (014678ec0f5e2b92d7f0
89a20ffe77fa).
Once executed, the malware establishes a
connection to the domain clandestine fordkaksosat.info
(193.105.207.45 – AS50793 ALFAHOSTNET) from
which you download and run malware automatically a
rogue type.
This malware is also promoted through a website
from which, using social engineering, simulates the sale
of an antivirus program through a file called PCDefend
erSilentSetup.msi (ecff63c1f983858dfd7fb926738cb47
8), which represents the so-called rogue PC Defender
Antivirus. The cost is typically USD 59.95.
PEK has been around since mid-2007.
This link is hidden for visitors. Please Log in or register now.
This link is hidden for visitors. Please Log in or register now.
Last edited by a moderator: