dEEpEst
☣☣ In The Depths ☣☣
Staff member
Administrator
Super Moderator
Hacker
Specter
Crawler
Shadow
- Joined
- Mar 29, 2018
- Messages
- 13,861
- Solutions
- 4
- Reputation
- 32
- Reaction score
- 45,552
- Points
- 1,813
- Credits
- 55,350
7 Years of Service
56%
 Stego Injector – Red Channel Steganography Dropper & Executable Cloaker
Stego Injector – Red Channel Steganography Dropper & Executable Cloaker
Stego Injector is a Red Team tool that allows you to inject any .exe payload into a PNG image using red-channel steganography and export a final executable disguised as a `.png`. This PoC is ideal for education, awareness, and research in covert execution techniques.

 Features
Features
- Hide any `.exe` inside a valid PNG image (stego PNG)
- Use XOR obfuscation on the red channel (1 byte per pixel)
- Embed the PNG into an automatic dropper stub
- Execute the payload and show the image seamlessly
- Compile the final `.exe` with custom icon and filename
- Camouflage the final `.exe` as a `.png` using Unicode RTLO
- Clean and silent – no dependencies once compiled
 How it works
How it works
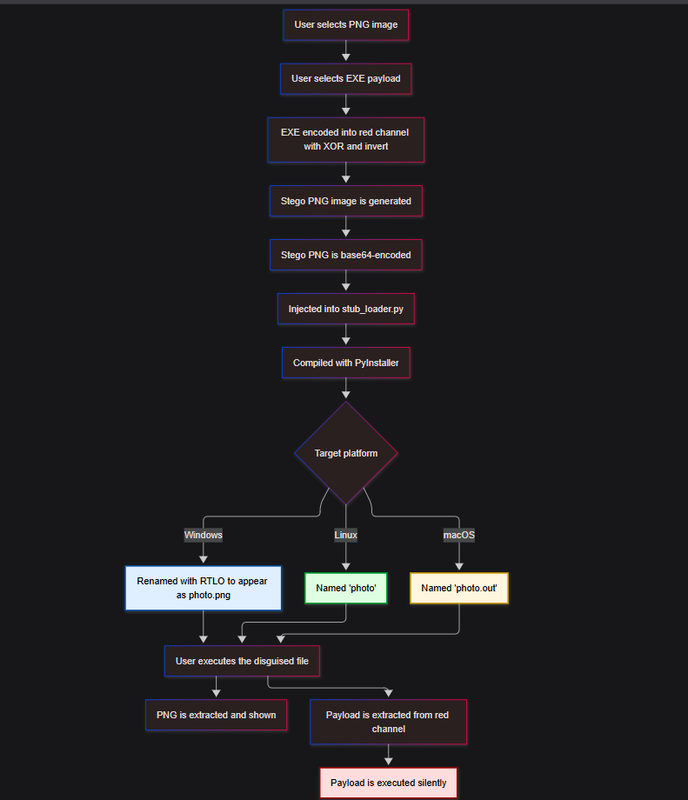
- The selected `.exe` is encoded byte-by-byte into the red channel of a PNG image using `XOR 0x72` + inversion.
- The modified image is saved as a valid stego PNG.
- The stego PNG is then base64-encoded and injected into a
stub_loader.pytemplate. - The stub is compiled into a `.exe` using PyInstaller (with optional custom icon).
- The resulting `.exe` is renamed using
U+202E(RTLO) so it appears as `photo.png` even with extensions visible. - When executed, the file:
- Extracts the PNG
- Displays the image
- Extracts and executes the original `.exe` payload silently
 Execution Flow Diagram
Execution Flow Diagram
 Output Example
Output Example
Code:
Original files:
- innocent.png
- reverse_shell.exe
Final file:
- photognp.exe → (shown as photo.png)
Payload:
- Executes reverse_shell.exe
- Displays innocent.png to avoid suspicion Requirements Builder
Requirements Builder
- Python 3.7+
- PyInstaller
- Pillow
 Final File Requirements
Final File Requirements
- None
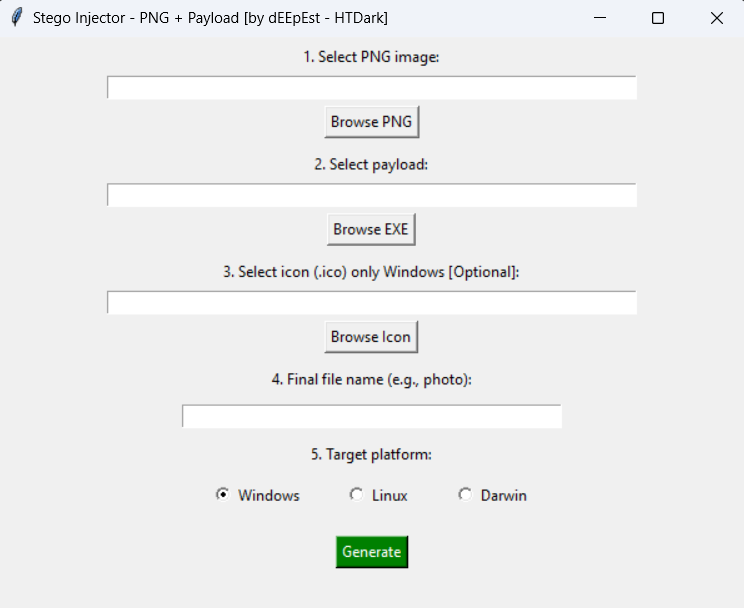
 GUI Screenshot
GUI Screenshot

 Scanner result
Scanner result
 Detection notes
Detection notes
- The final `.exe` will be flagged by AVs if the payload is malicious.
- The current detection rate is very low despite testing with malicious files.
- This tool is designed for ethical use and simulation only.
- The PNG shown is fake – it only masks execution; the file is still a PE.
 Tested platforms
Tested platforms


 Tested Rats
Tested Rats
 Forensic Evasion
Forensic Evasion
- File extension appears harmless: `.png`
- Valid PNG signature (but only visually; file starts with MZ)
- Payload hidden in pixel data – difficult to detect by casual inspection
- Does not drop to disk until runtime
 Disclaimer
Disclaimer
This tool is for educational purposes only. It is intended to demonstrate steganography and evasion techniques in Red Team scenarios, CTFs, and training labs.
Do not use this tool on systems you don’t own or without explicit authorization. The author assumes no responsibility for misuse.
 Credits
Credits
Created by @dEEpEst_23 for HTDark Community Designed to blend payloads with pixels
Stealth meets simplicity.
 Download
Download
- The download is free!!
- Nothing is for sale!!
- It's free!!
- You must decrypt the password.
- Send me the decrypted password via private message.
- Maximum 2 attempts per user.
- You must note in this post that you sent a private message participating.
- The first person to decrypt the password gets it for free.
The code appears at the indicated time: 14:00 UTC
Code:
In the image you could find the password to decipher.
Clue:
“The image holds information in the LSB of RGB components. Normalize it first. Then look at the parity.”
Order used to encrypt the password → ROT13 → Base64 (x3) → AES(key= name domain forum) → DES(key= name old domain forum) → Vigenère (key= name creator tool Stego Injector)
https://htdark.com/filecloud/download.php?id=p6d61rt2vz
Password: htdark.com Source or Demo
Source or Demo
Maybe Visit:
This link is hidden for visitors. Please Log in or register now.
 Related tools that may interest you
Related tools that may interest you
 Did you know that a simple PNG image can hide malicious code?
Did you know that a simple PNG image can hide malicious code?
StegAnalyzer GUI is a forensic analysis and steganalysis tool designed to detect payloads hidden in PNG images.
 It features:
It features:
Multi-technique analysis: LSB, XOR, block patterns, metadata, and magic headers
Reports in text and JSON (with SHA-256 hashes)
Heuristic filtering by entropy, repetitions, and ASCII characters
 Demo:
Demo:
This link is hidden for visitors. Please Log in or register now.
- dEEpEst
- #cybersecurity #infosec #malwareanalysis forensics gui python steganography tool
- Replies: 0
- Forum: Protection Tools

StegoCracker
What is steganography
Steganography is the art of hiding a secret message within a normal message. This is used to transfer some secret message to another person; with this technique, no one else in between will know the secret message you wanted to convey.
This art of hiding secret messages has been used for years in real-life communications. Since the evolution of digital communication, it has also been used in digital conversations.
This software can hide your secret...
- itsMe
- and free open-source steganography stegocracker: tool
- Replies: 0
- Forum: Pentesting
Next-Gen Covert Channels for Red Team
Thread starter Thread starter dEEpEst Start date Start date Jun 9, 2025...
 htdark.com
htdark.com
Last edited: