- Joined
- Jan 8, 2019
- Messages
- 56,623
- Solutions
- 2
- Reputation
- 32
- Reaction score
- 100,456
- Points
- 2,313
- Credits
- 32,750
6 Years of Service
76%
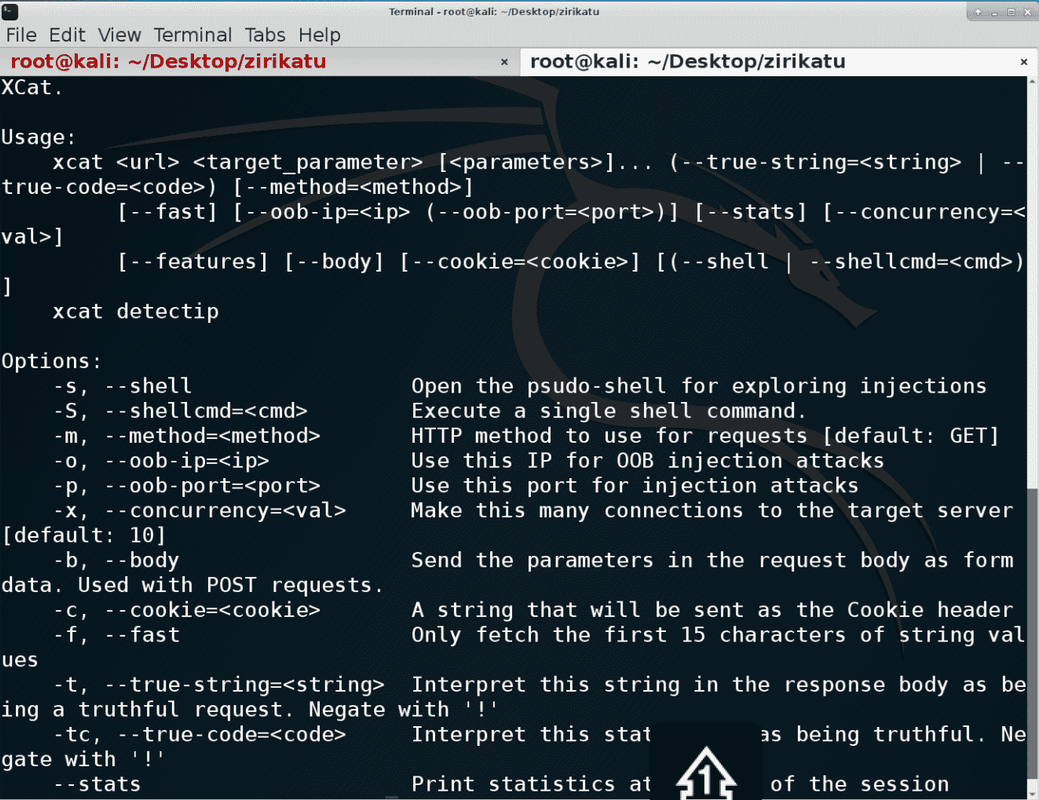
XCat is a command line tool to exploit and investigate blind XPath injection vulnerabilities.
For a complete reference read the documentation here:
This link is hidden for visitors. Please Log in or register now.
It supports an large number of features:
Auto-selects injections (run xcat injections for a list)
Detects the version and capabilities of the xpath parser and selects the fastest method of retrieval
Built in out-of-bound HTTP server
Automates XXE attacks
Can use OOB HTTP requests to drastically speed up retrieval
Custom request headers and body
Built in REPL shell, supporting:
Reading arbitrary files
Reading environment variables
Listing directories
Uploading/downloading files (soon TM)
Optimized retrieval
Uses binary search over unicode codepoints if available
Fallbacks include searching for common characters previously retrieved first
Normalizes unicode to reduce the search space
To see this hidden content, you must like this content.